Gladys is a new employee at the company. She received an email notifying her that the IT department would be performing some work on her personal computer. She was instructed to call the IT team, who would tell her how to allow them remote access. However, this IT team is actually a group of hackers attempting to attack Forela.
Task1 What is the name of the executable uploaded as a C2 agent?
Open the Microsoft-Windows-Sysmon%4Operational.evtx log file.
Microsoft-Windows-Sysmon operational.evtx is an event log file generated by Windows Sysmon (System Monitor), which records various activities and events on the system. Sysmon is part of the Sysinternals Suite and enhances Windows logging capabilities by providing detailed event monitoring to assist with security analysis and incident response.
Sysmon can monitor and log the following types of events:
- Process Creation: Monitors the creation of new processes, including command line arguments.
- Network Connections: Records information about outbound and inbound network connections.
- File Creation Time: Logs events related to file creation, modification, and deletion.
- Driver Loading: Monitors drivers loaded in the system.
- File Hash: Records the hash values of files for later analysis.
- Registry Operations: Monitors the creation, modification, and deletion of registry keys.
- Raw Event Logging: Records other significant system events.
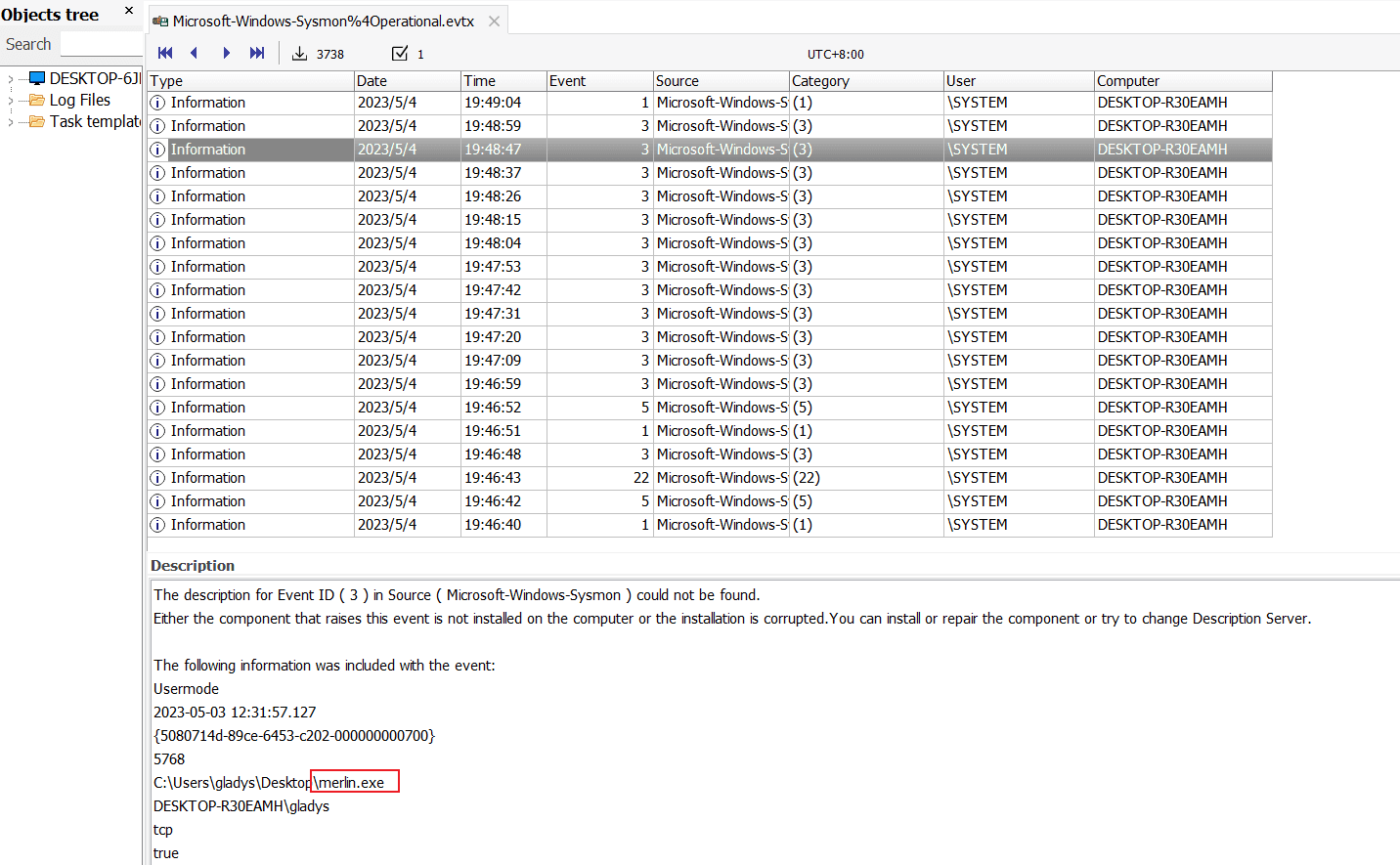
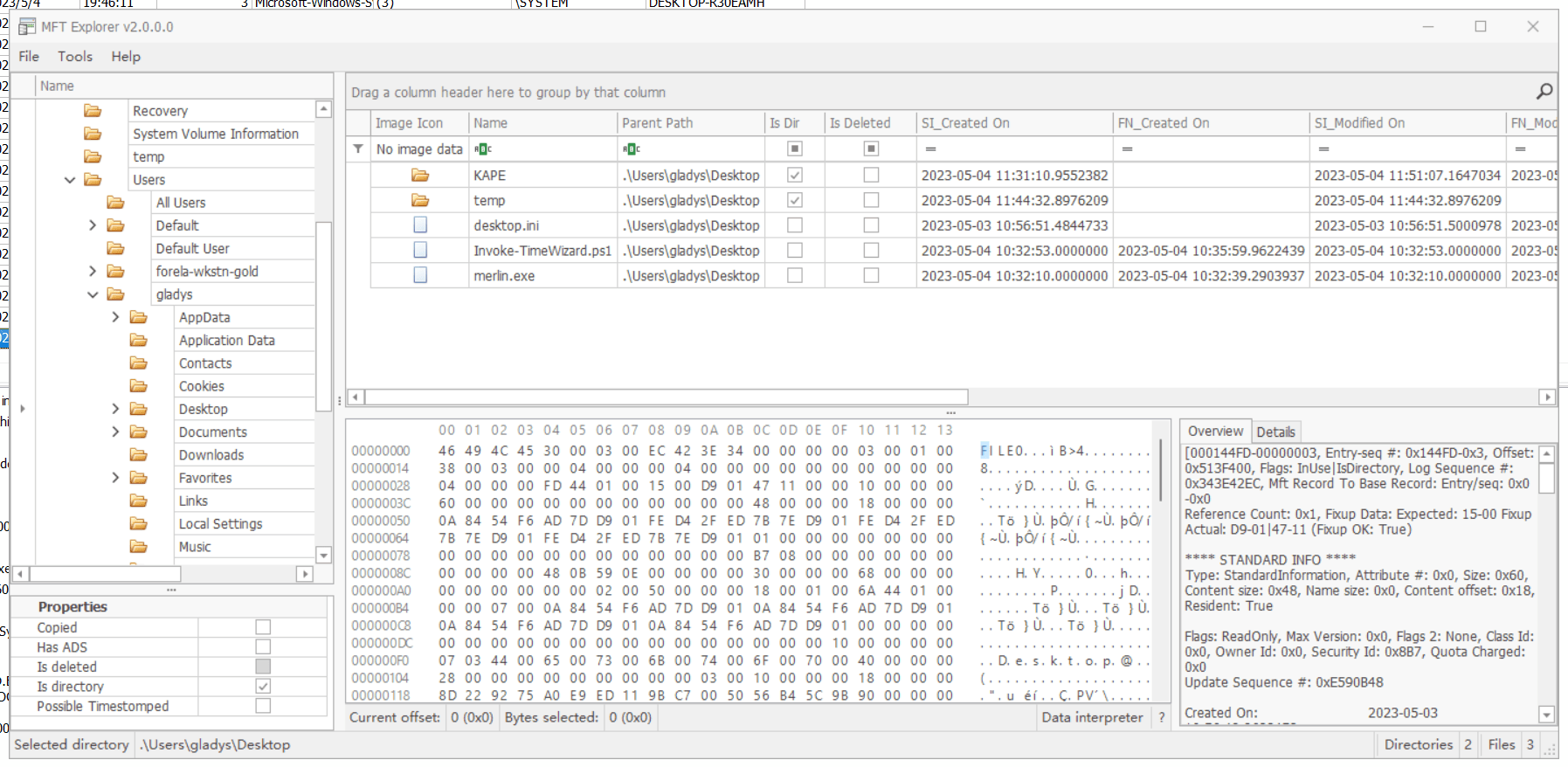
Alternatively, check the MFT records, and you can see this file on the desktop.
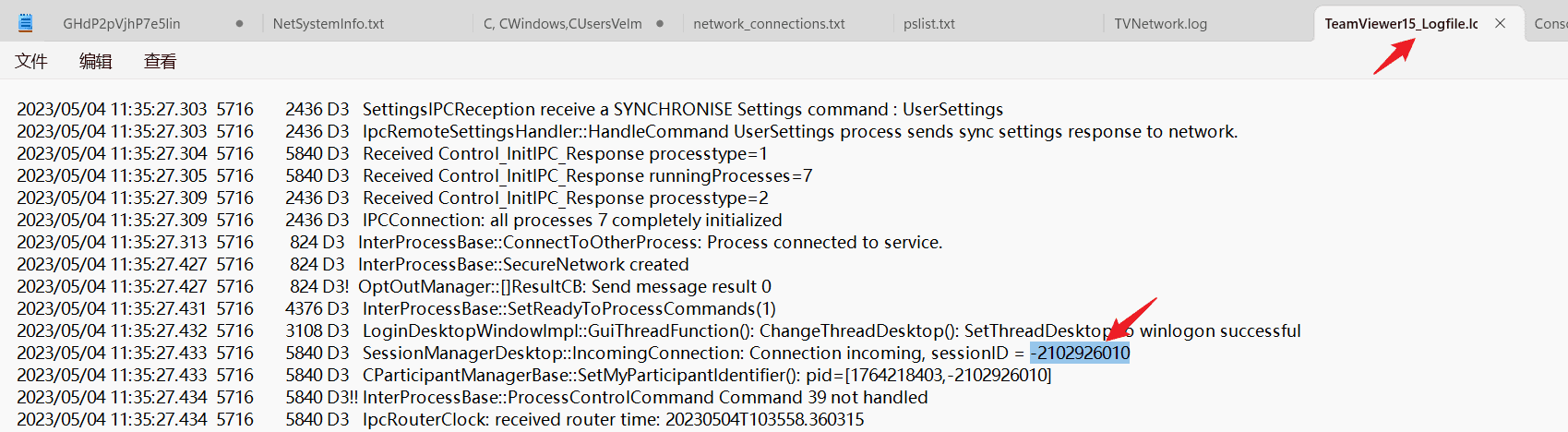
Task2 What is the session ID at the time of initial access?
The attacker accessed remotely via TeamViewer software, check the TeamViewer logs.
The log path is as follows:
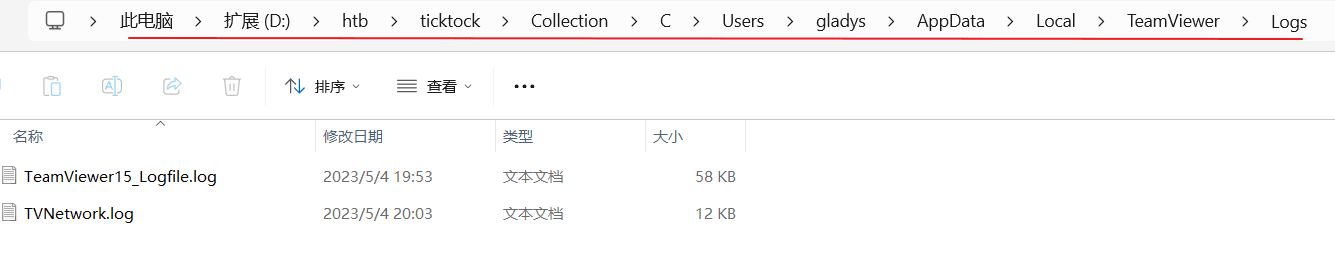
At the very beginning, you can see the session ID.
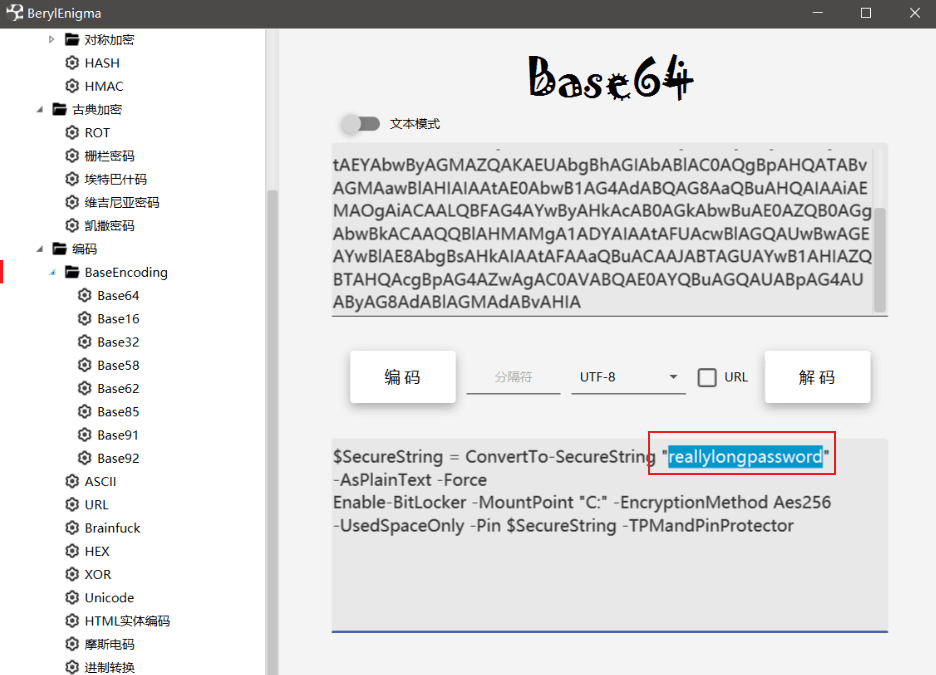
Task3 What is the password that the attacker tried to set for BitLocker on the C: drive?
Check the Windows PowerShell.evtx log.
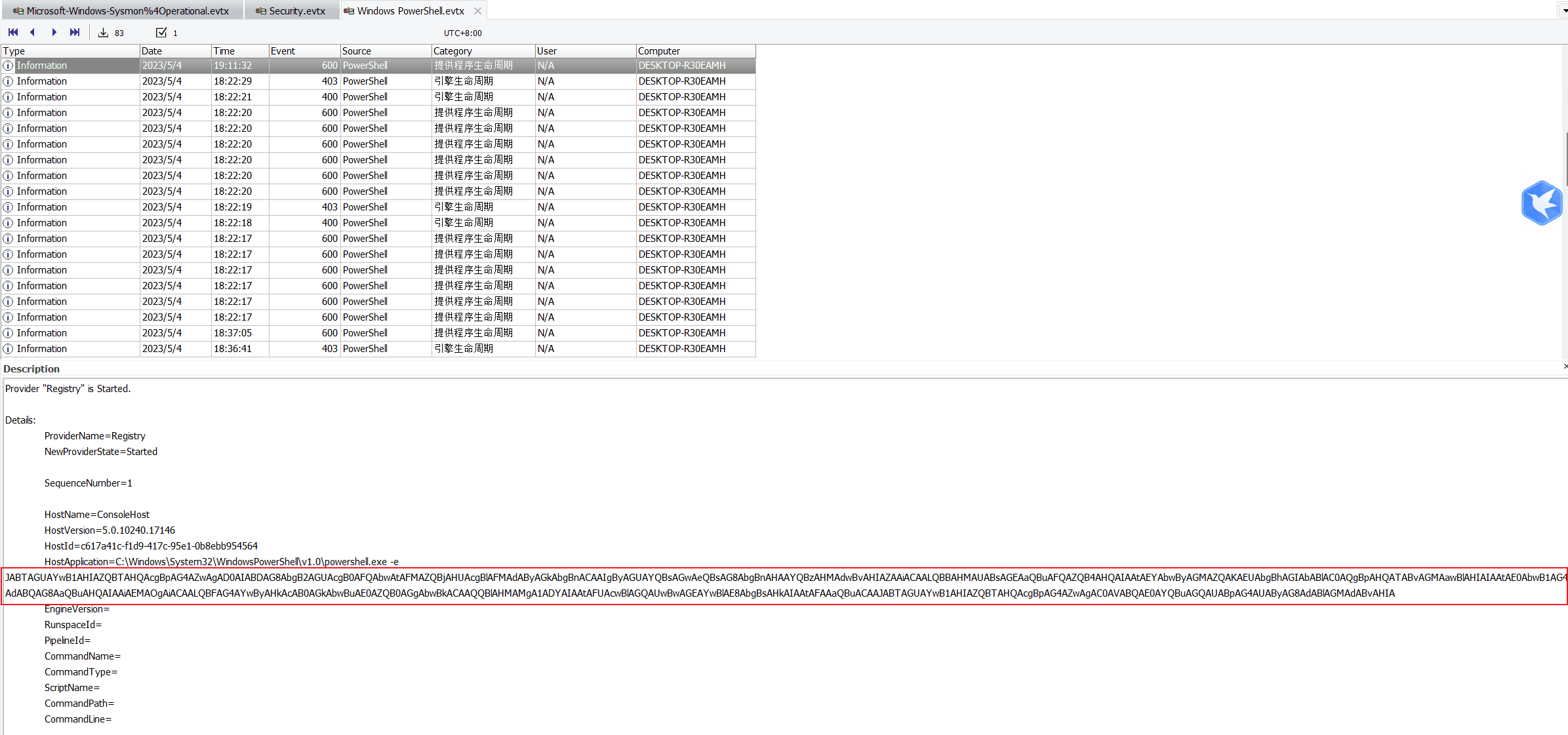
Base64 decode to get the password.
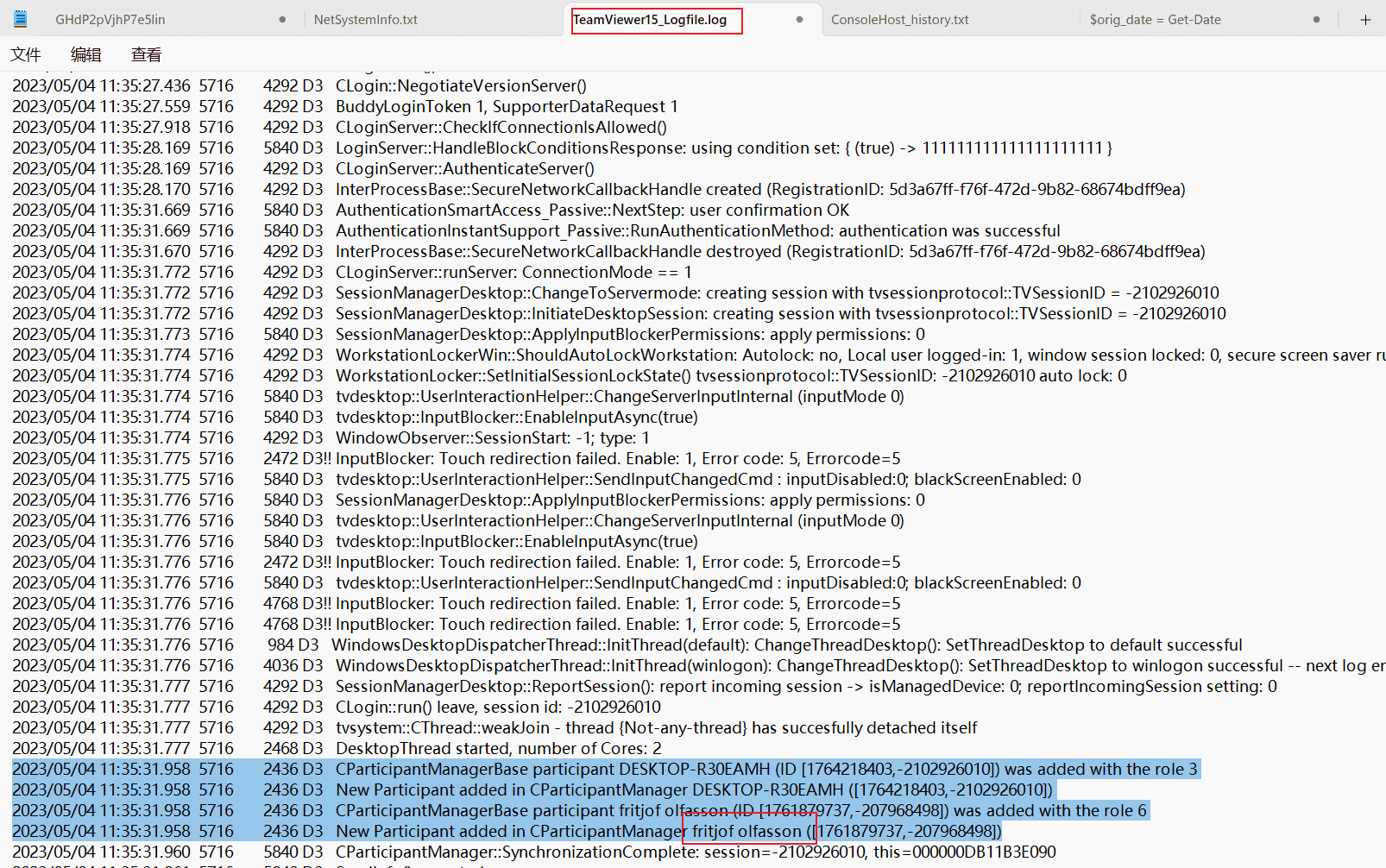
Task4 What name did the attacker use?
Check the TeamViewer logs.
Task5 Which IP address did the C2 connect back to?
Check the Microsoft-Windows-Sysmon%4Operational.evtx log file.
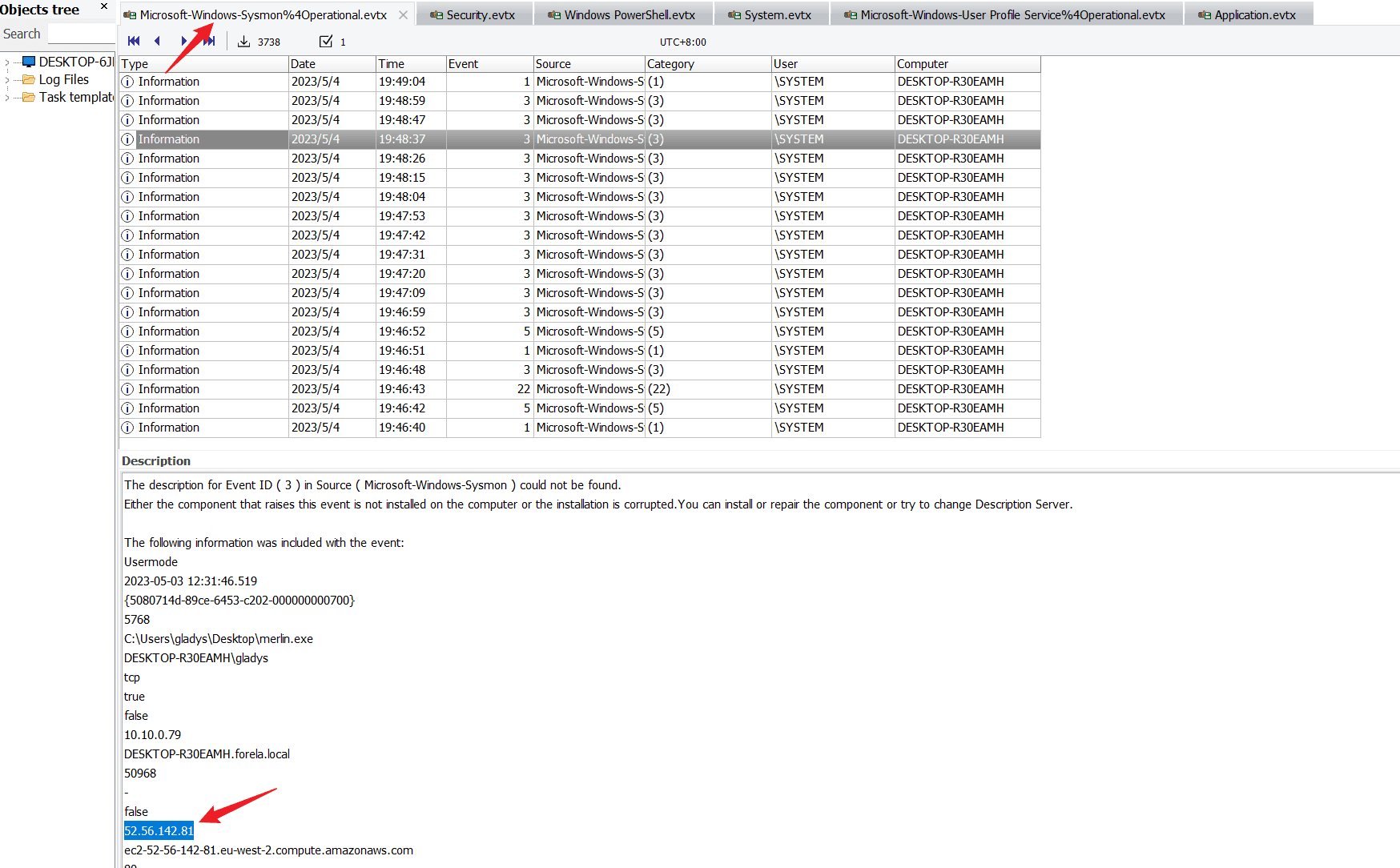
52.56.142.81
Task6 What category did Windows Defender assign to the C2 binary?
Check the Windows Defender logs.
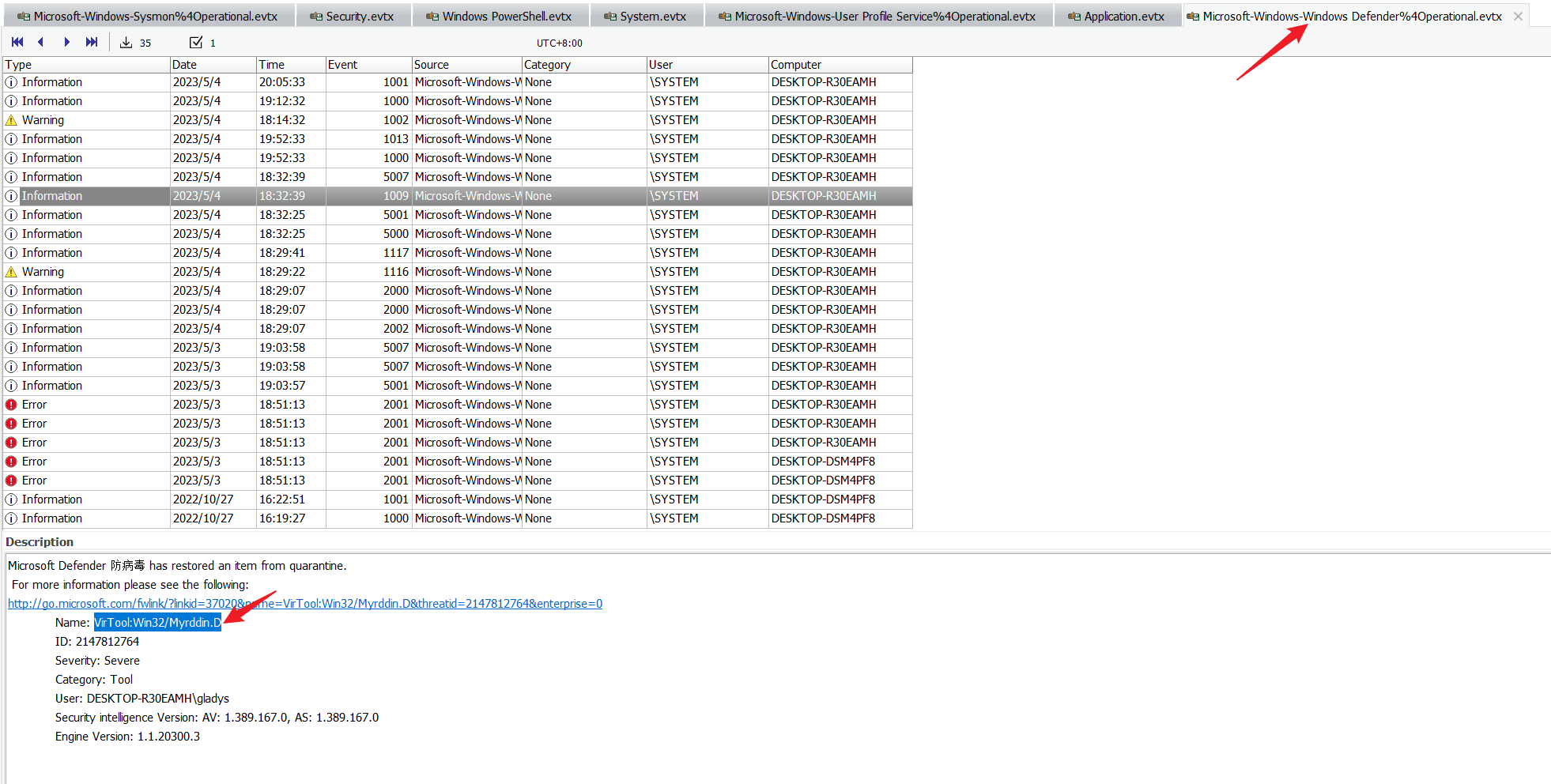
VirTool/Myrddin.D
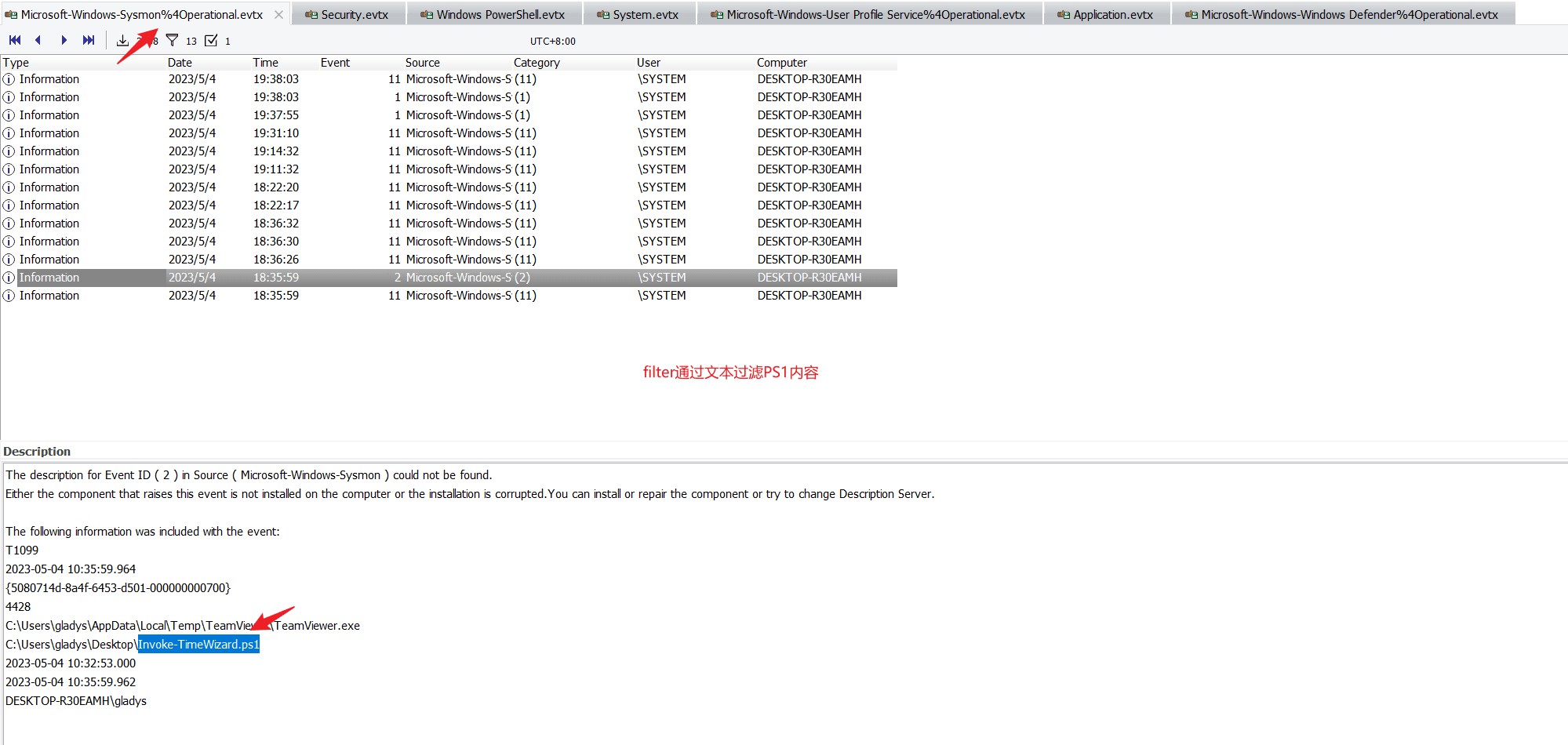
Task7 What is the filename of the PowerShell script the attacker used to manipulate time?
Check the Microsoft-Windows-Sysmon%4Operational.evtx log file, filter for PS1 suffix.
You can see the script related to time.
Alternatively, analyze the MFT file, and you can also find the PS1 script on the desktop.
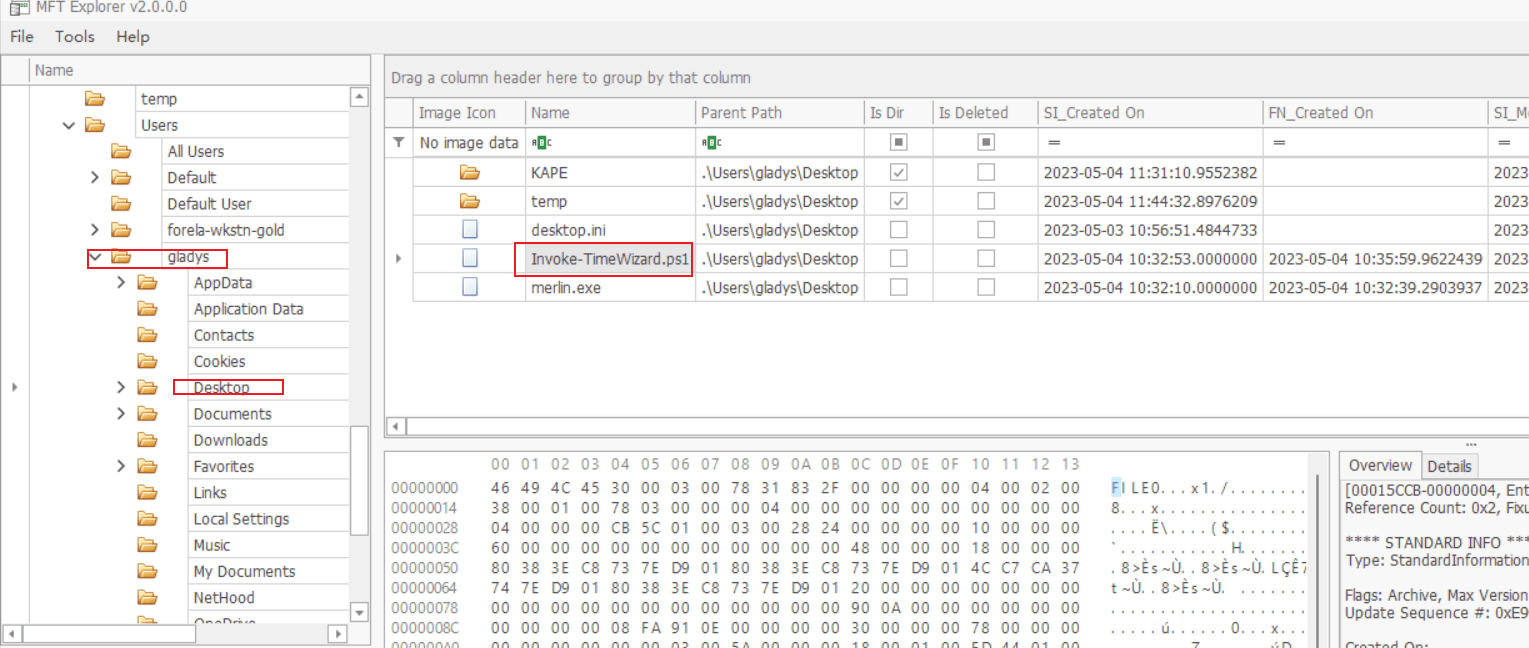
Invoke-TimeWizard.ps1
Task8 When did the initial access connection start?
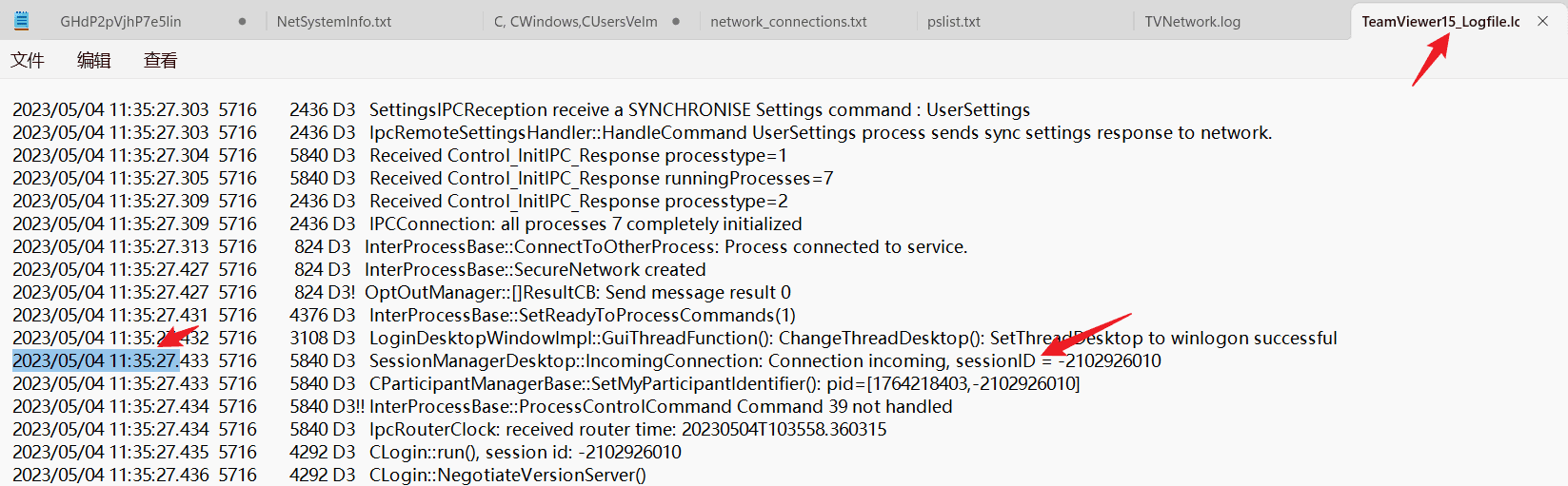
2023/05/04 11:35:27
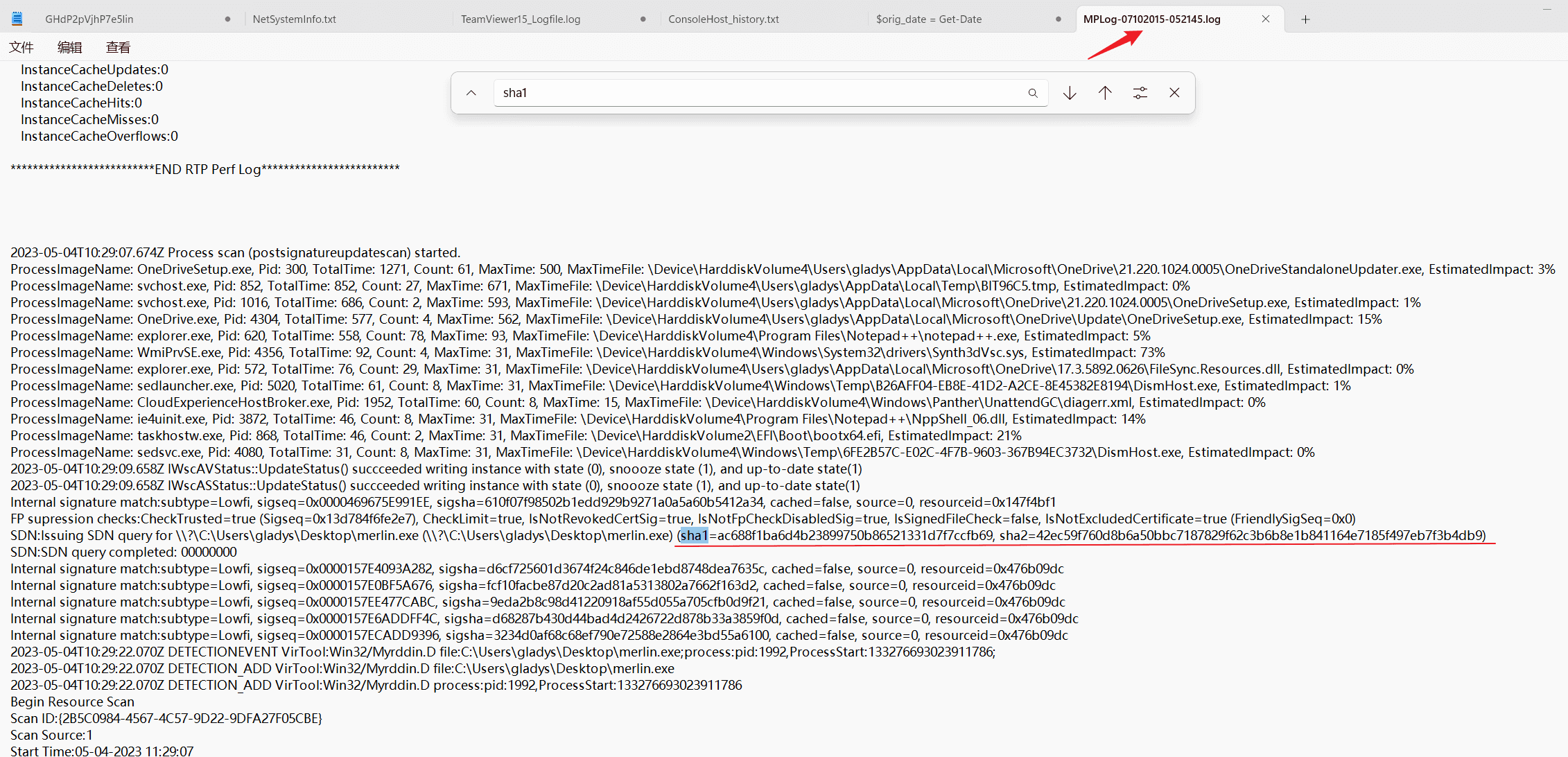
Task9 What is the sum of the SHA1 and SHA2 of the malicious binary file?
Analyze the log files under the Windows Defender directory.
Search for SHA1.
Task10 How many times did the PowerShell script change the time on the machine?
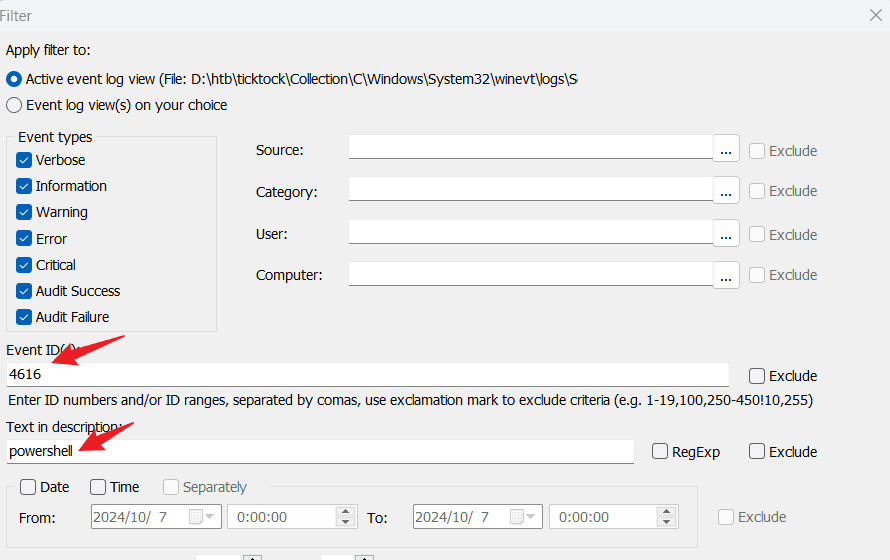
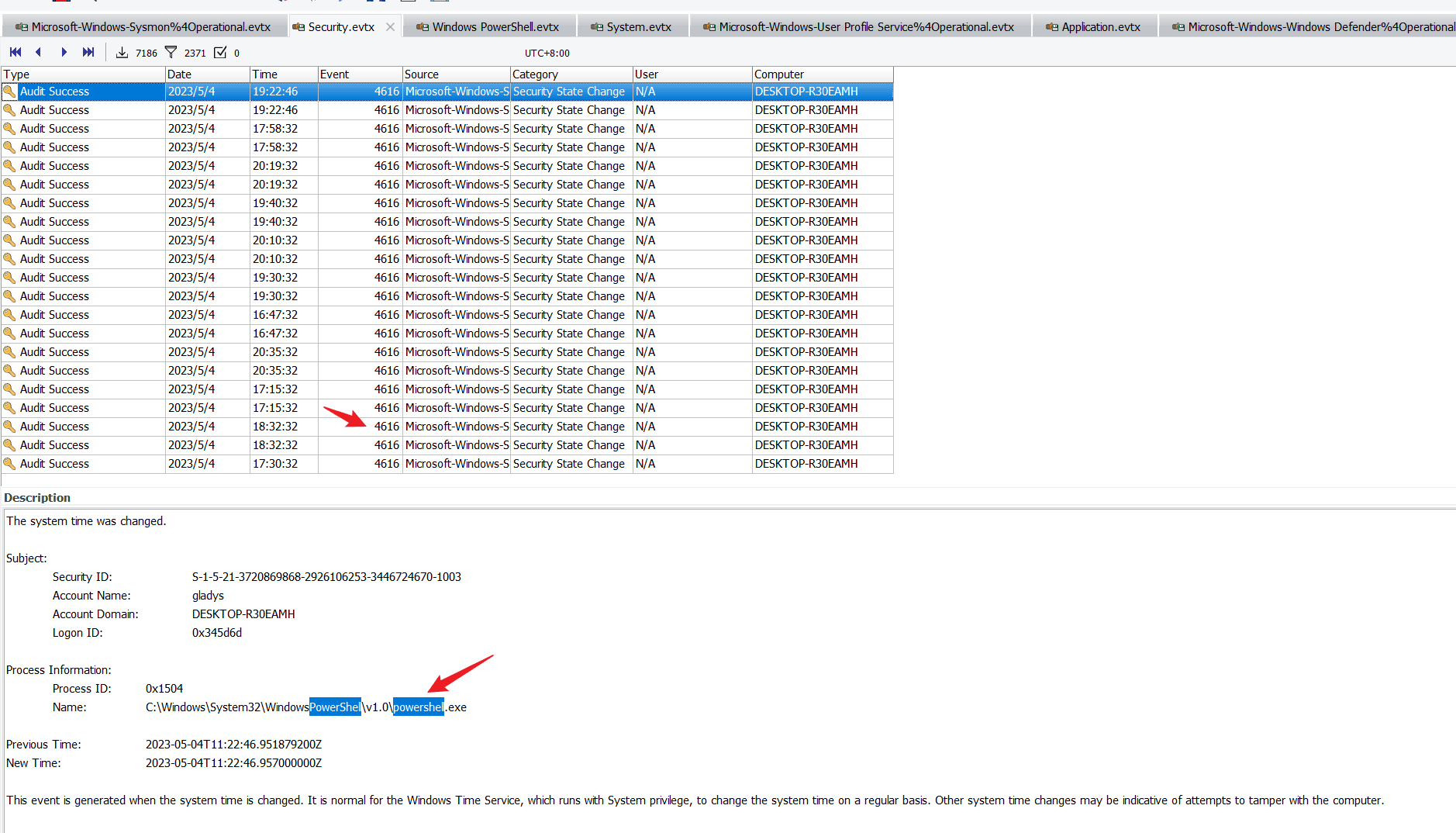
2371
Task11 What is the SID of the victim user?
Check the security logs to find out.
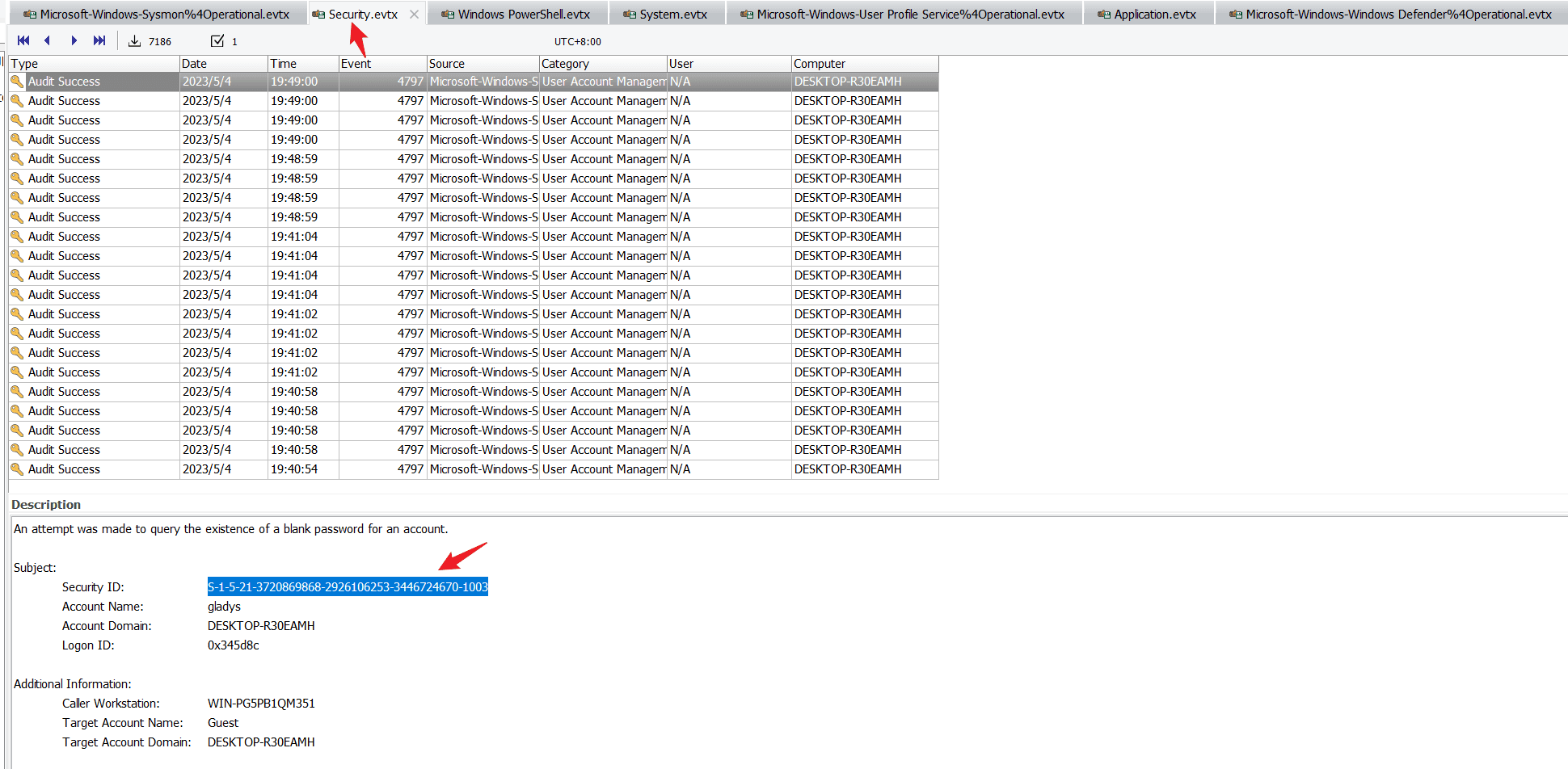
S-1-5-21-3720869868-2926106253-3446724670-1003