[!hint]+ Scenario
You have been given an opportunity to work as a junior Digital Forensics and Incident Response (DFIR) consultant at a large consulting firm. However, they have provided a technical assessment task that you need to complete. Forela-Security Consulting wants to test your mastery of Windows event log analysis. We suspect that the Cyberjunkie user logged into his computer and may have performed malicious actions. Please analyze the provided event logs and report the results back to us.
Tools: event log explorer
Task1 When did cyberjunkie successfully log into the computer for the first time? (UTC time)
The event ID for the login is: 4624, filter this ID.
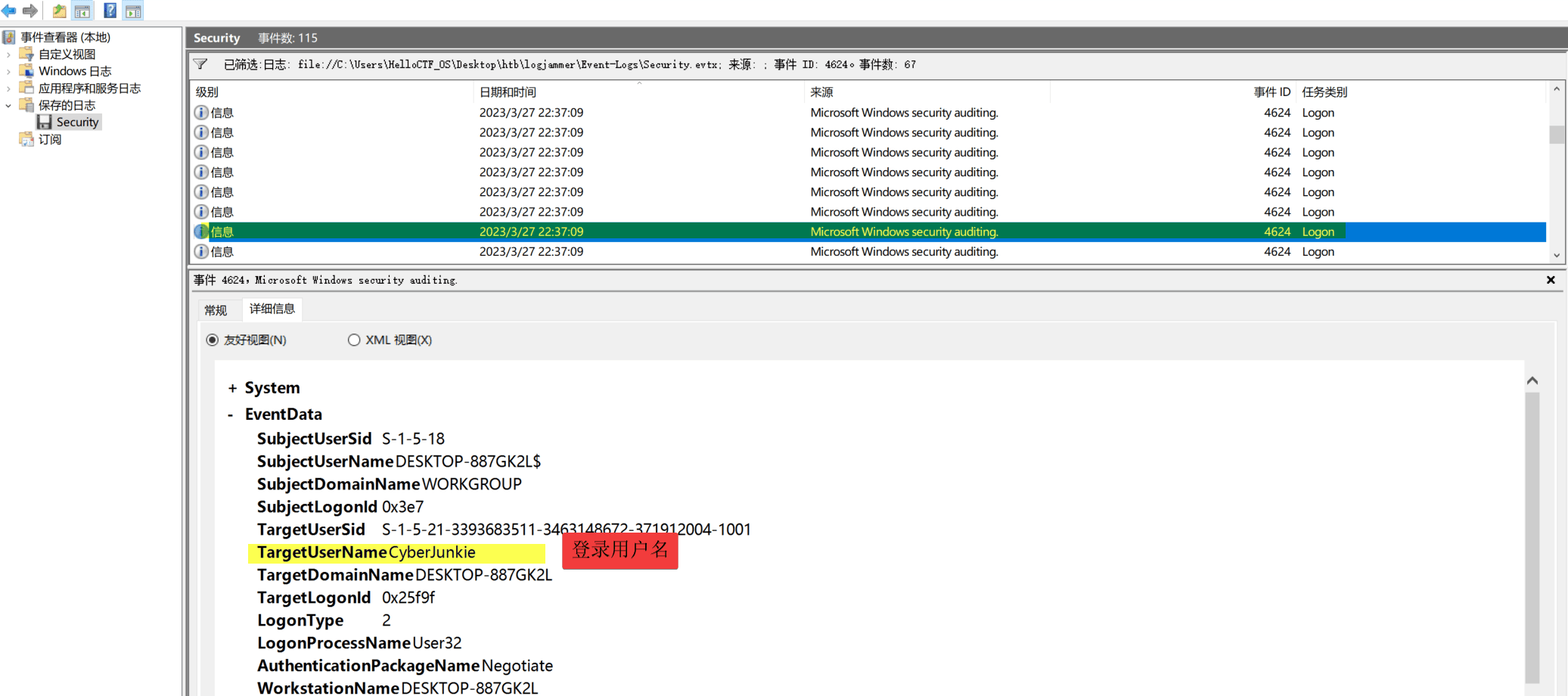
event log explorer log analysis
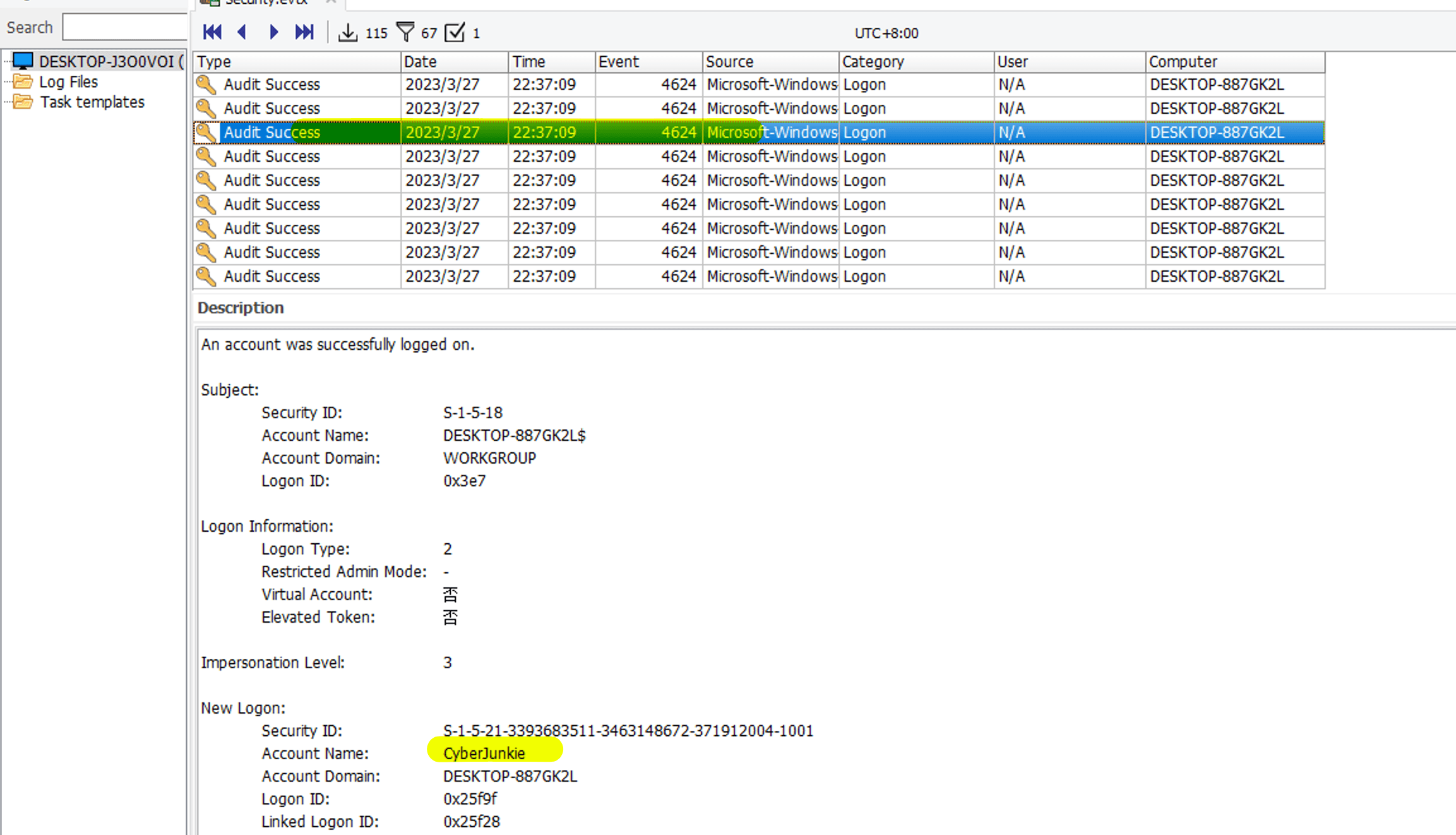
27/03/2023 22:37:09, with a time zone, needs to subtract 8 (UTC+8), which is 27/03/2023 14:37:09.
Task2 The user unauthorizedly modified the firewall configuration in the system. By reviewing the firewall event logs, we can determine what the name of the newly added firewall rule is.
Open the firewall logs to see.
Metasploit C2 Bypass

Task3 How is the traffic direction defined for the firewall rule?
Filter 2004 only.
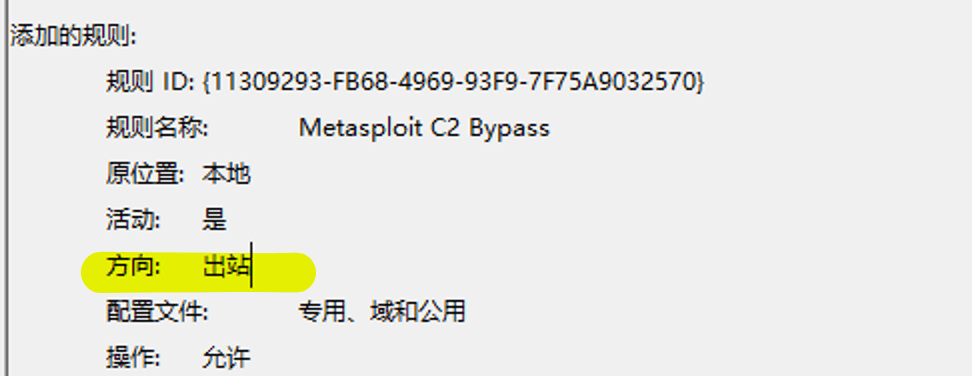

Outbound
Task4 The user adjusted the audit policy of the computer. What subcategory does this adjustment belong to?

Filter 4719, which is Other Object Access Events.
Task5 cyberjunkie created a scheduled task. What is the name of this task?
The event ID for creating a task in security events is 4698.
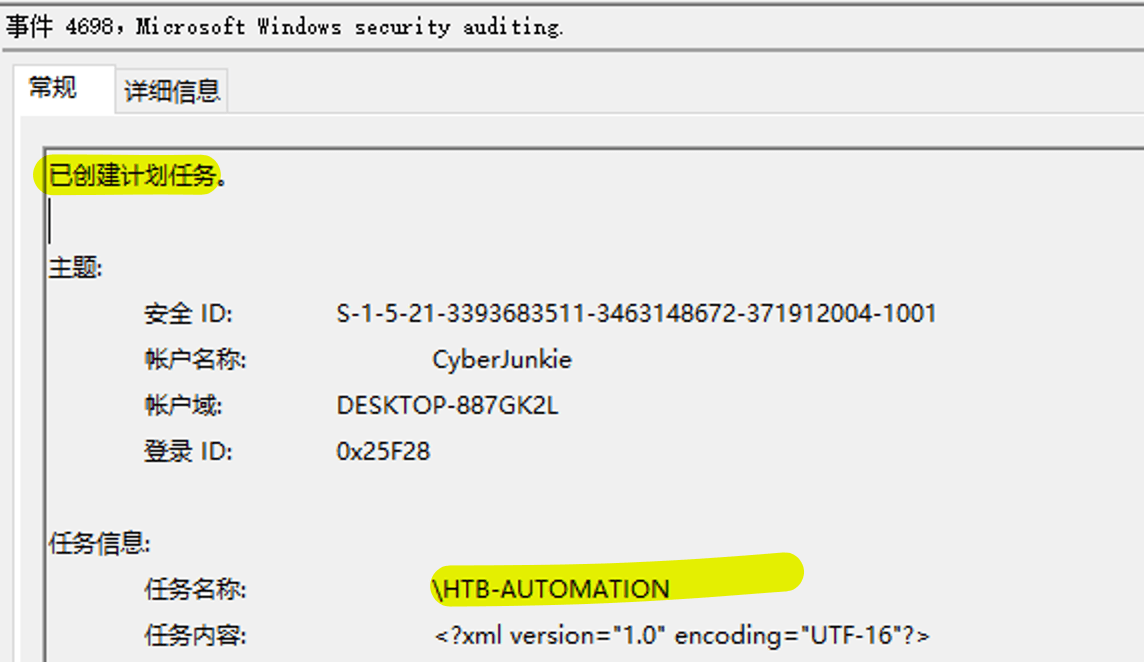
HTB-AUTOMATION
Task6 What is the full path of the file that was scheduled for the task?
Same as above.
C:\Users\CyberJunkie\Desktop\Automation-HTB.ps1
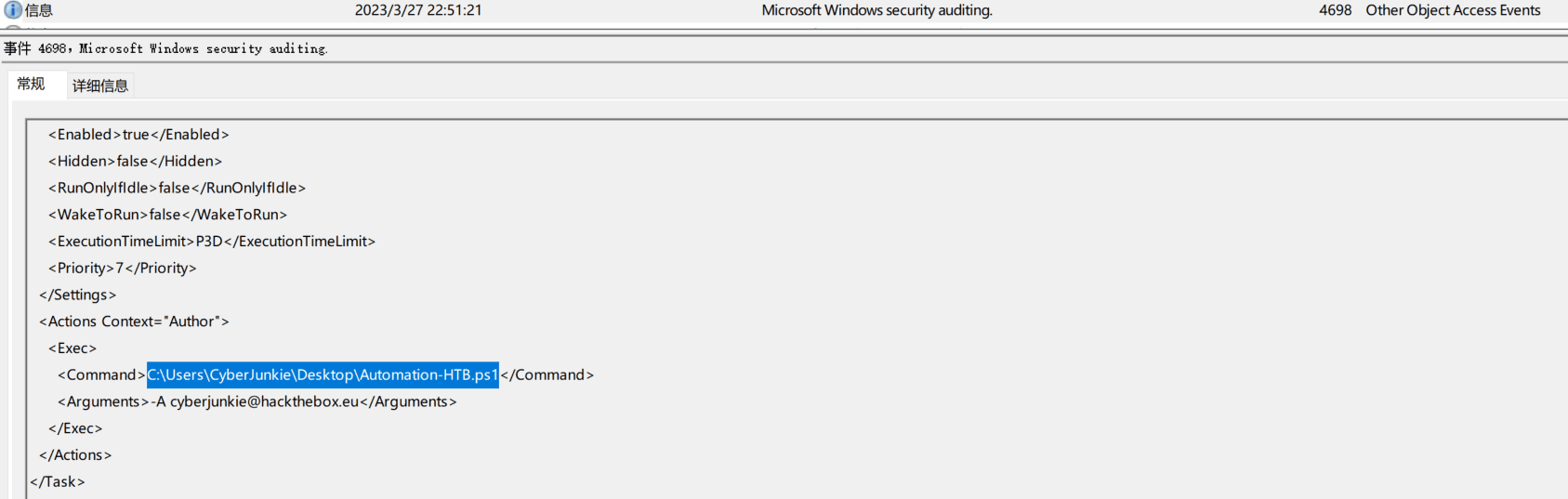
Task7 What parameters are included in the command?
Same as above.
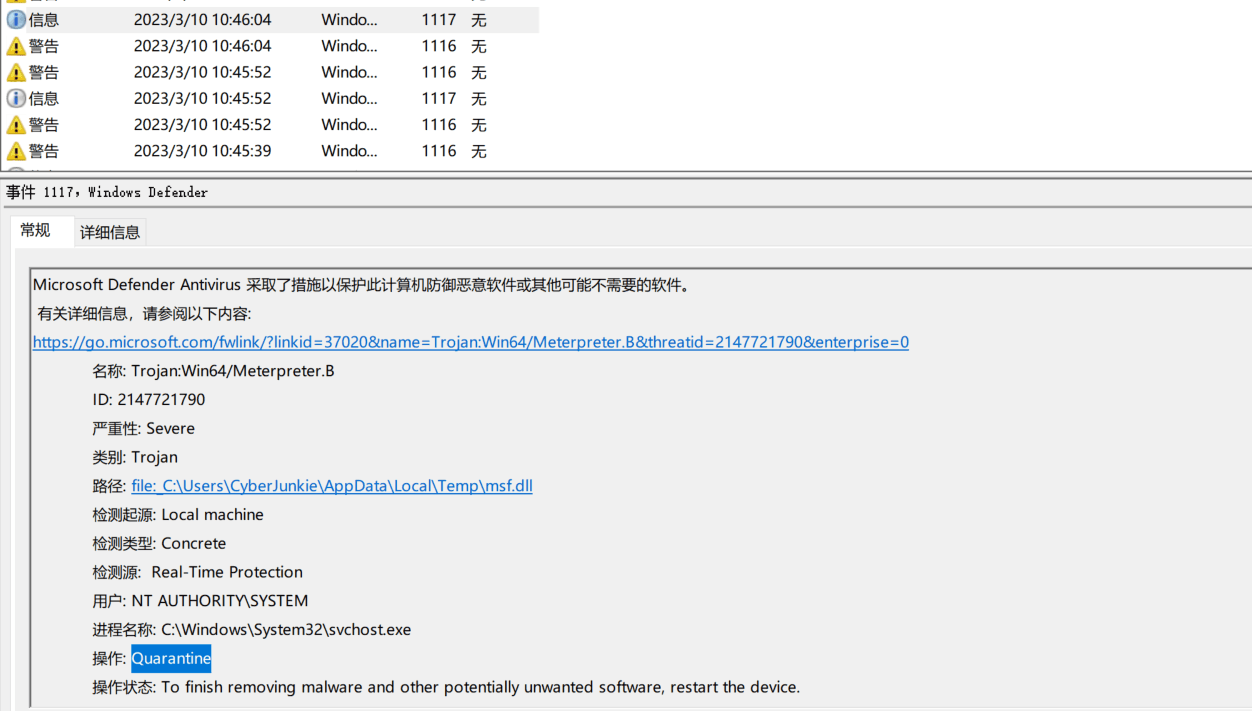
Task8 The antivirus software in the system detected potential threats and took corresponding actions. Which tool was identified as malicious by the antivirus software?
The Windows Defender detection log, open to view the detection records, event ID is 1117.
You can find the SharpHound file.

Task9 What is the full path of the malware that triggered the alert?
Same as above.
C:\Users\CyberJunkie\Downloads\SharpHound-v1.1.0.zip
Task10 What actions did the antivirus software take?
Same as above.
Quarantine
Task11 The user executed commands via PowerShell. What specific command was executed?
PowerShell log, the event ID for executing the command is 4104.
Get-FileHash -Algorithm md5 .\Desktop\Automation-HTB.ps1

Task12 We suspect that the user deleted certain event logs. Which event log file was cleared?
Check the system logs.
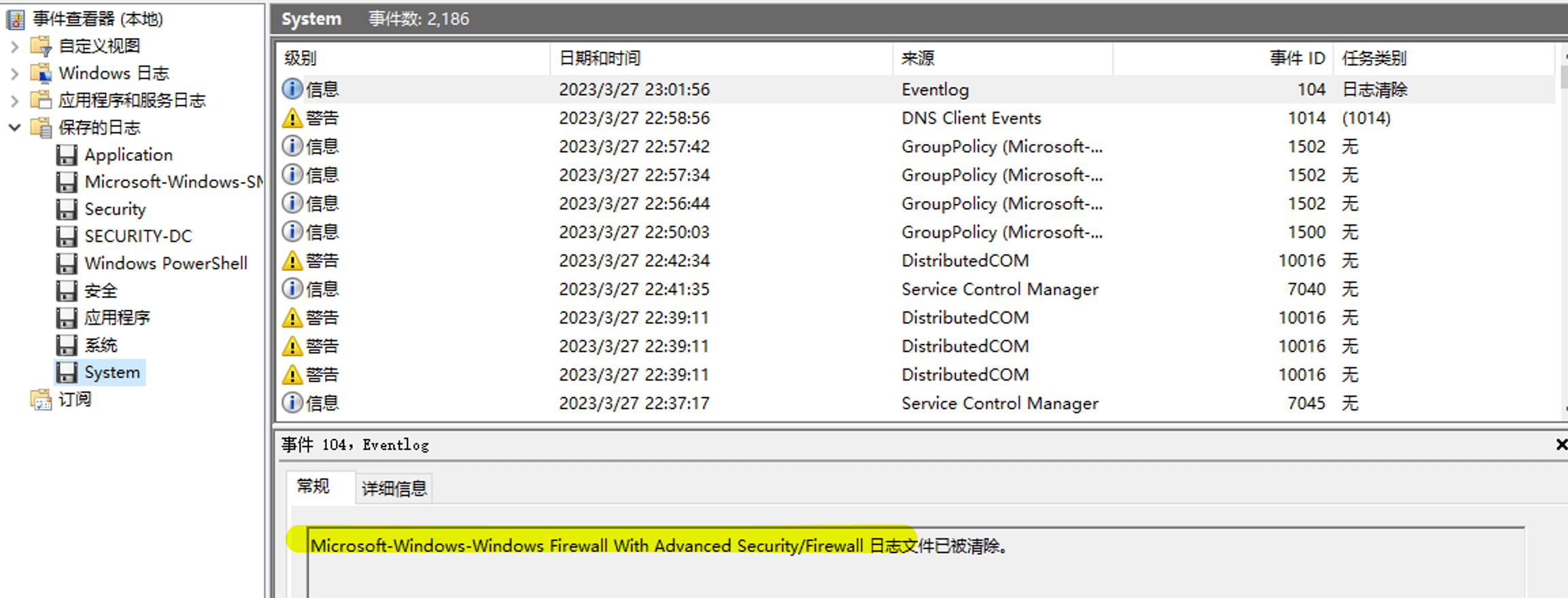
Microsoft-Windows-Windows Firewall With Advanced Security/Firewall